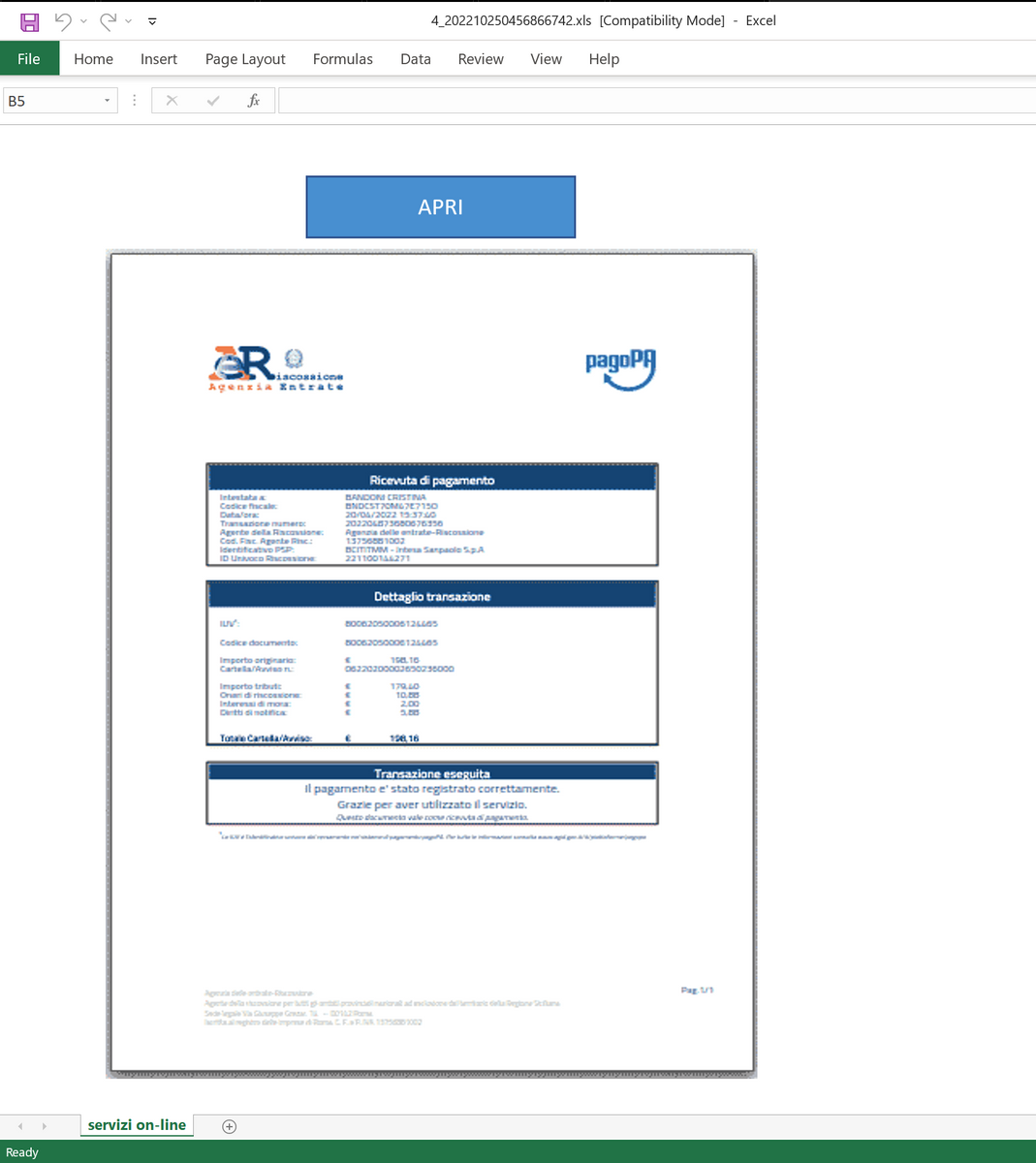
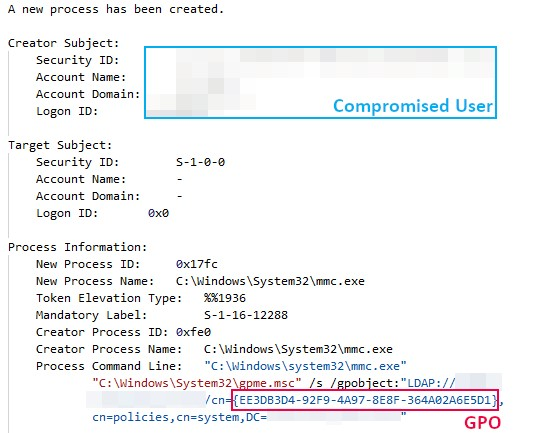
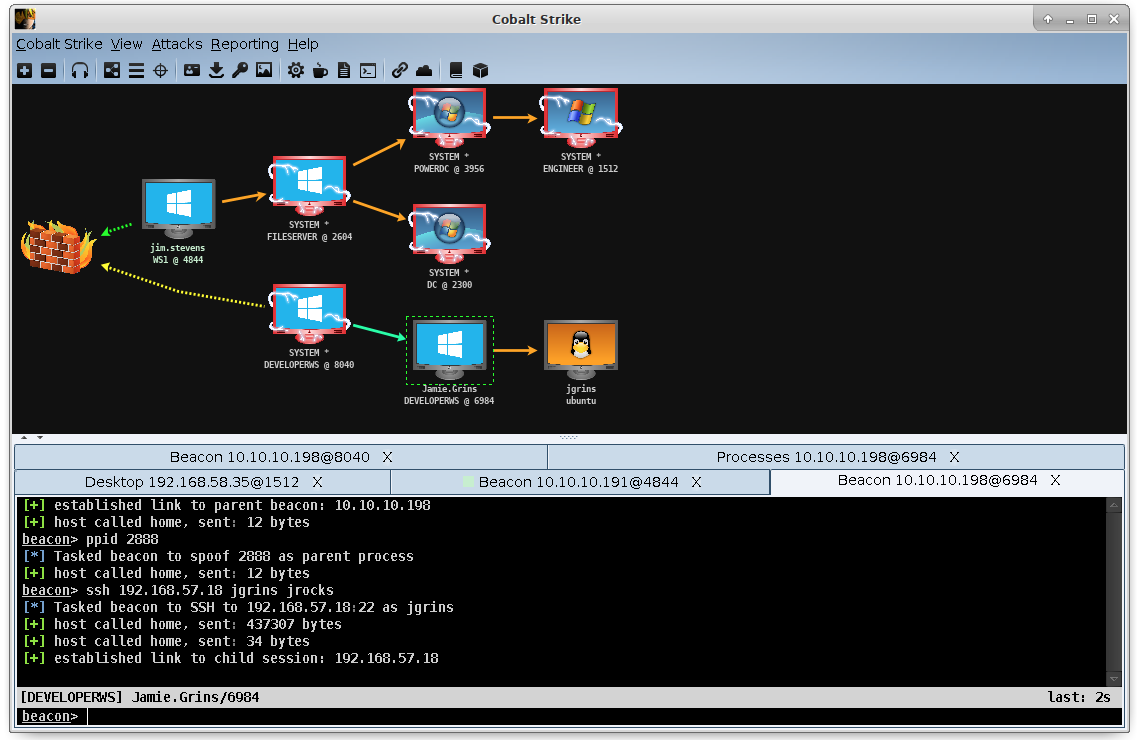
IcedID Macro Ends in Nokoyawa Ransomware – The DFIR Report
Threat actors have moved to other means of initial access, such as ISO files combined with LNKs or OneNote payloads, but some appearances of VBA macros in Office documents can still be seen in use.…| The DFIR Report