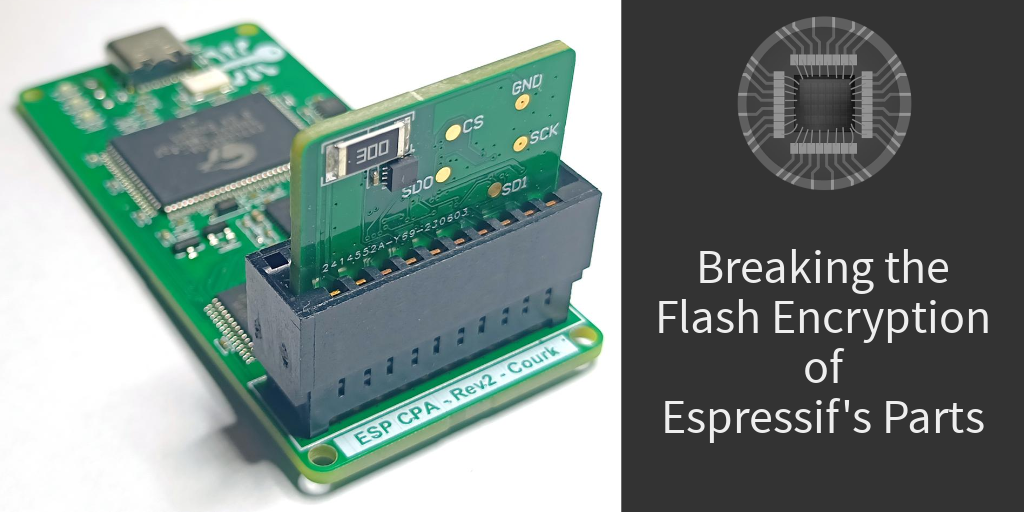
Courk's Blog – Fault Injection Attacks against the ESP32-C3 and ESP32-C6
In a previous article, the vulnerabilities of the ESP32-C3 and ESP32-C6 against side-channel attacks have been demonstrated. Recovering enough key information to decrypt the external flash data is possible. However, a new attack needs to be performed for each new 128-byte block. Since attacking a single block takes hours, this makes decrypting the entire flash content using such a method very impractical. This frustrating limitation led me to the following question: is it possible, given cont...| Courk's Blog