From GitHub to Account Takeover: Misconfigured Actions Place GCP & AWS Accounts at Risk - Rezonate
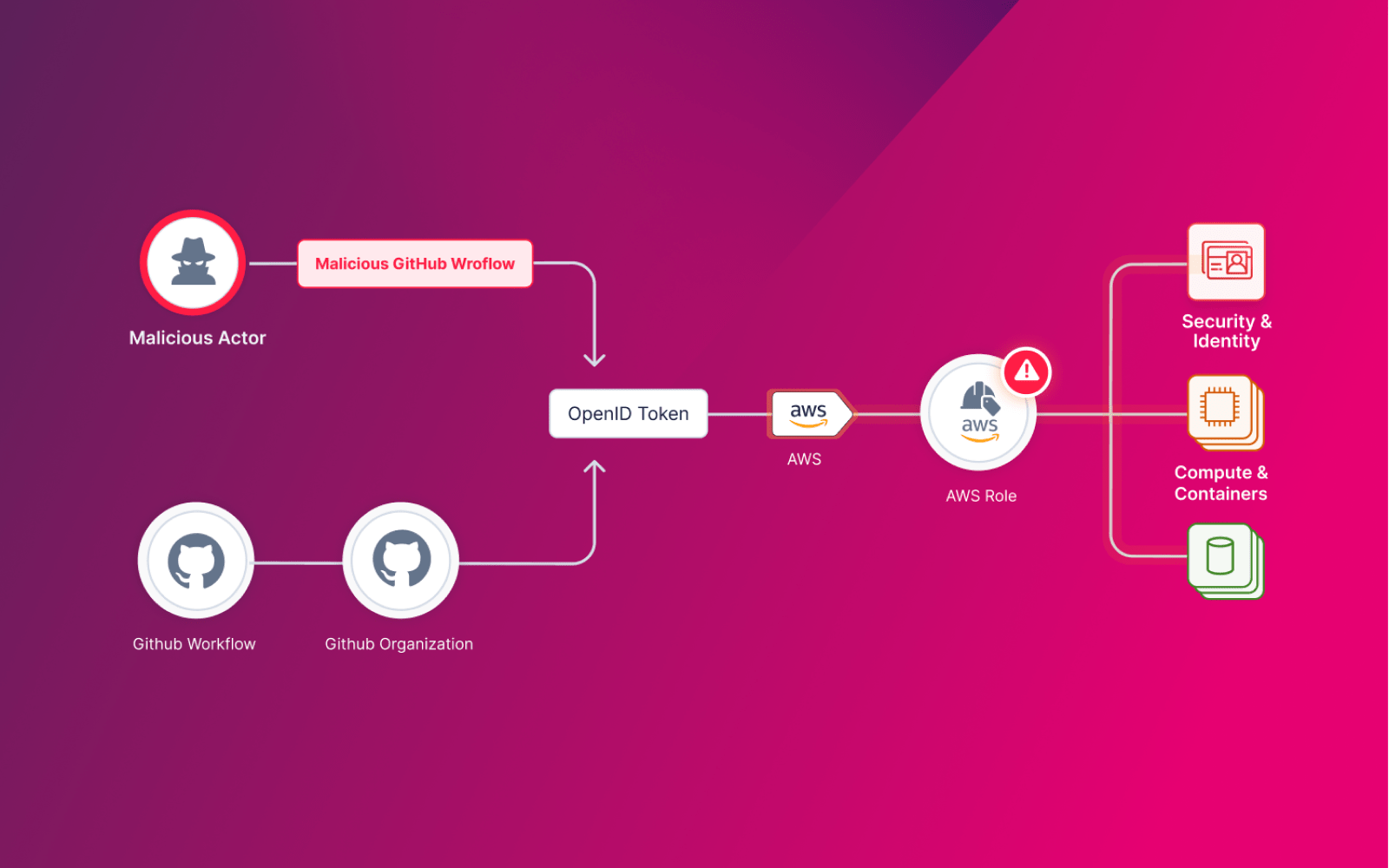
In April 2023, Rezonate research team explored prevalent misconfigurations of GitHub integration with cloud native vendors. GitHub OIDC-based trust relations have been found with the critical misconfigurations that leave connected AWS/GCP accounts vulnerable to potential takeover attacks. Although this issue was discovered and reported in the past, we have found that dozens of GitHub Public| Rezonate - Protect Identities, Everywhere