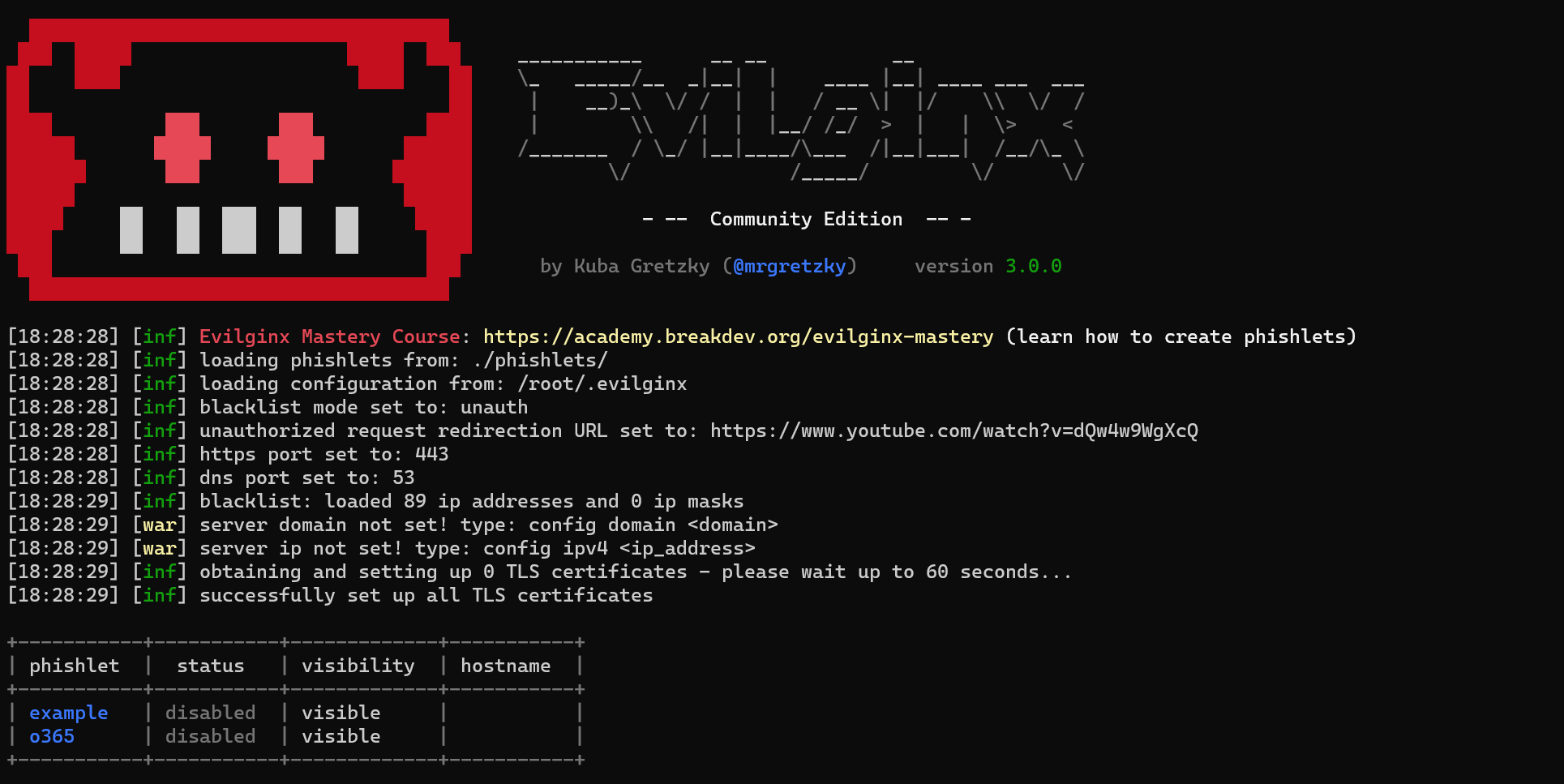
AiTM/ MFA phishing attacks in combination with "new" Microsoft protections (2024 edition)
Adversary-in-the-middle phishing attacks are still more common in use. Since the removal of basic authentication from Exchange Online more and more attackers are using more modern attacks like adversary-in-the-middle phishing, cookie theft, QR code phishing, and other used attacks. Last...| Jeffrey Appel - Microsoft Security blog