API Keys ≠ Security: Why API Keys Are Not Enough | Nordic APIs |
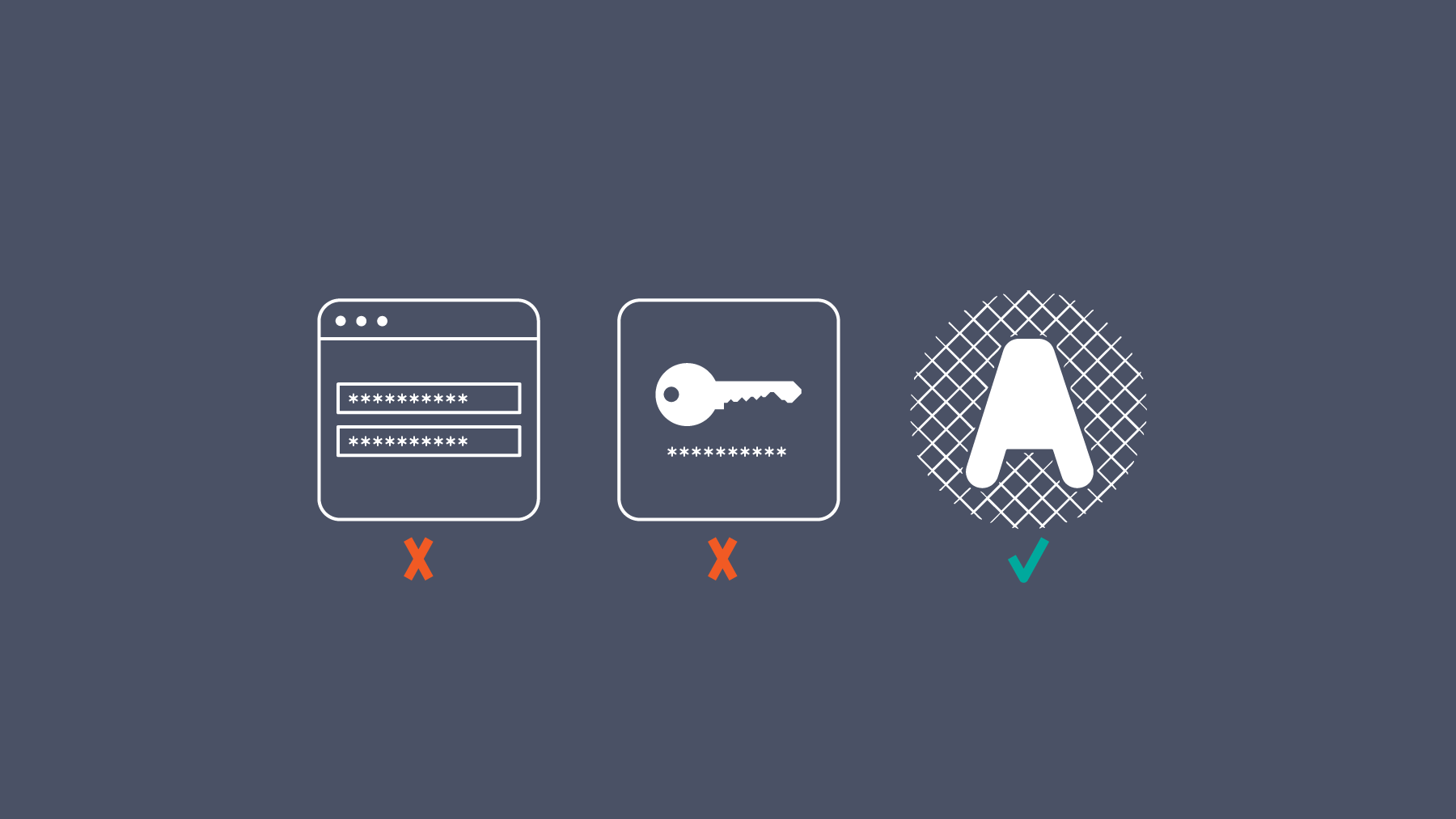
API Keys are not security. By design they lack granular control, and there are many vulnerabilities at stake: applications that contain keys can be decompiled to extract keys, or deobfuscated from on-device storage, plaintext files can be stolen for unapproved use, and password managers are susceptible to security risks as with any application. In this piece we outline the disadvantages of solely relying on API keys to secure the proper access to your data.| Nordic APIs