PQShield plugs timing leaks in Kyber / ML-KEM to improve PQC implementation maturity | PQShield
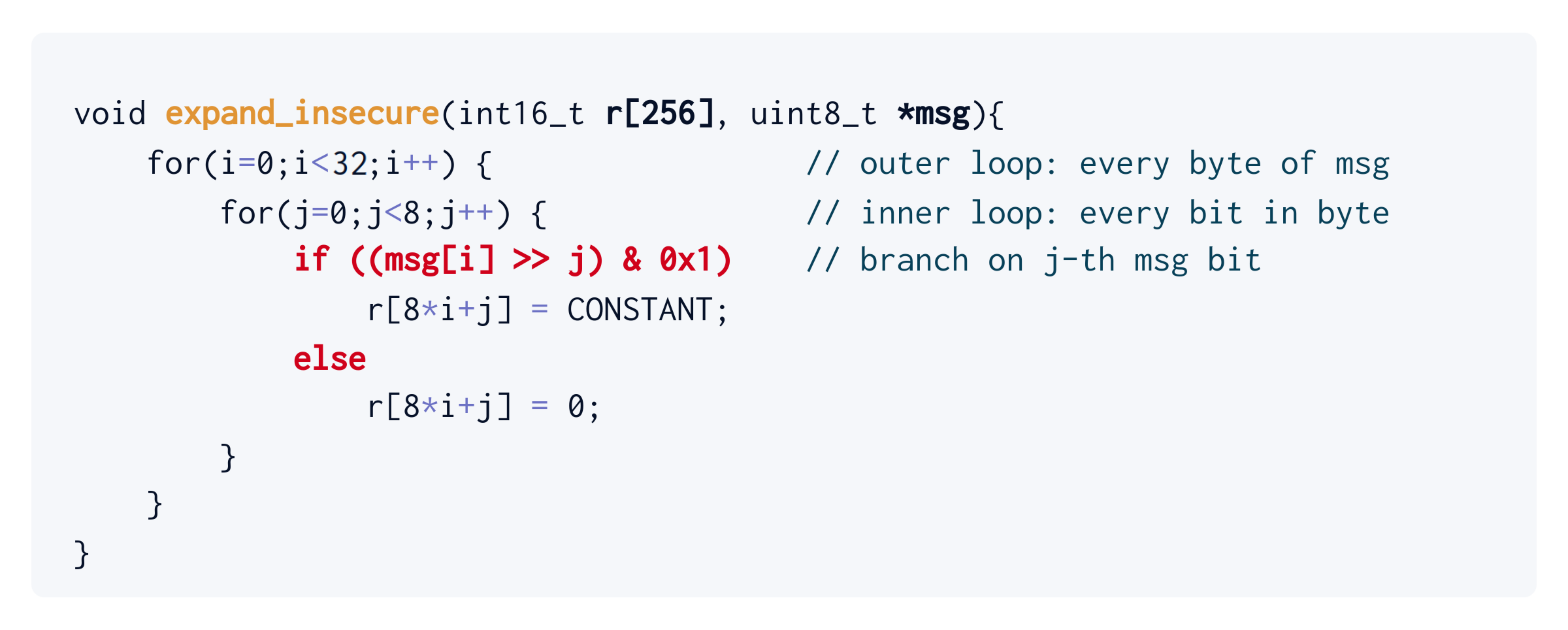
Compilers can suddenly and silently introduce implementation vulnerabilities in yesterday's secure code. PQShield recently discovered an instance of this problem in the popular ML-KEM (Kyber) reference implementation, and it has been resolved with the help of Peter Schwabe and the Kyber team. Read More.| PQShield