Fake Zoom Ends in BlackSuit Ransomware – The DFIR Report
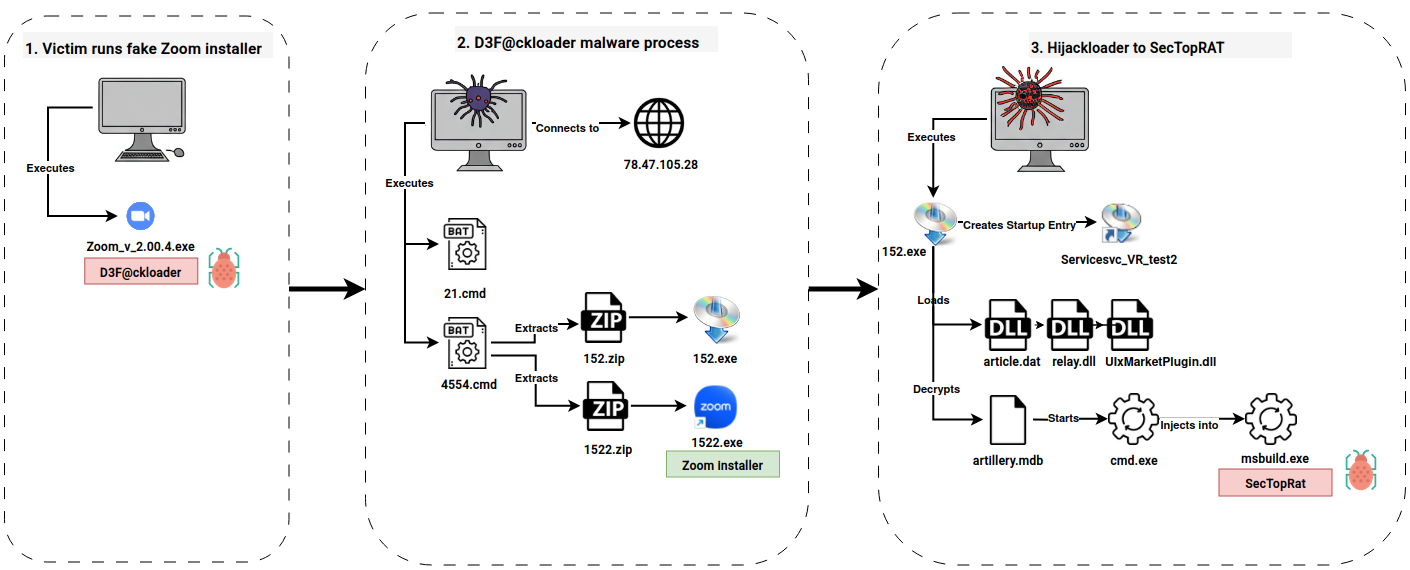
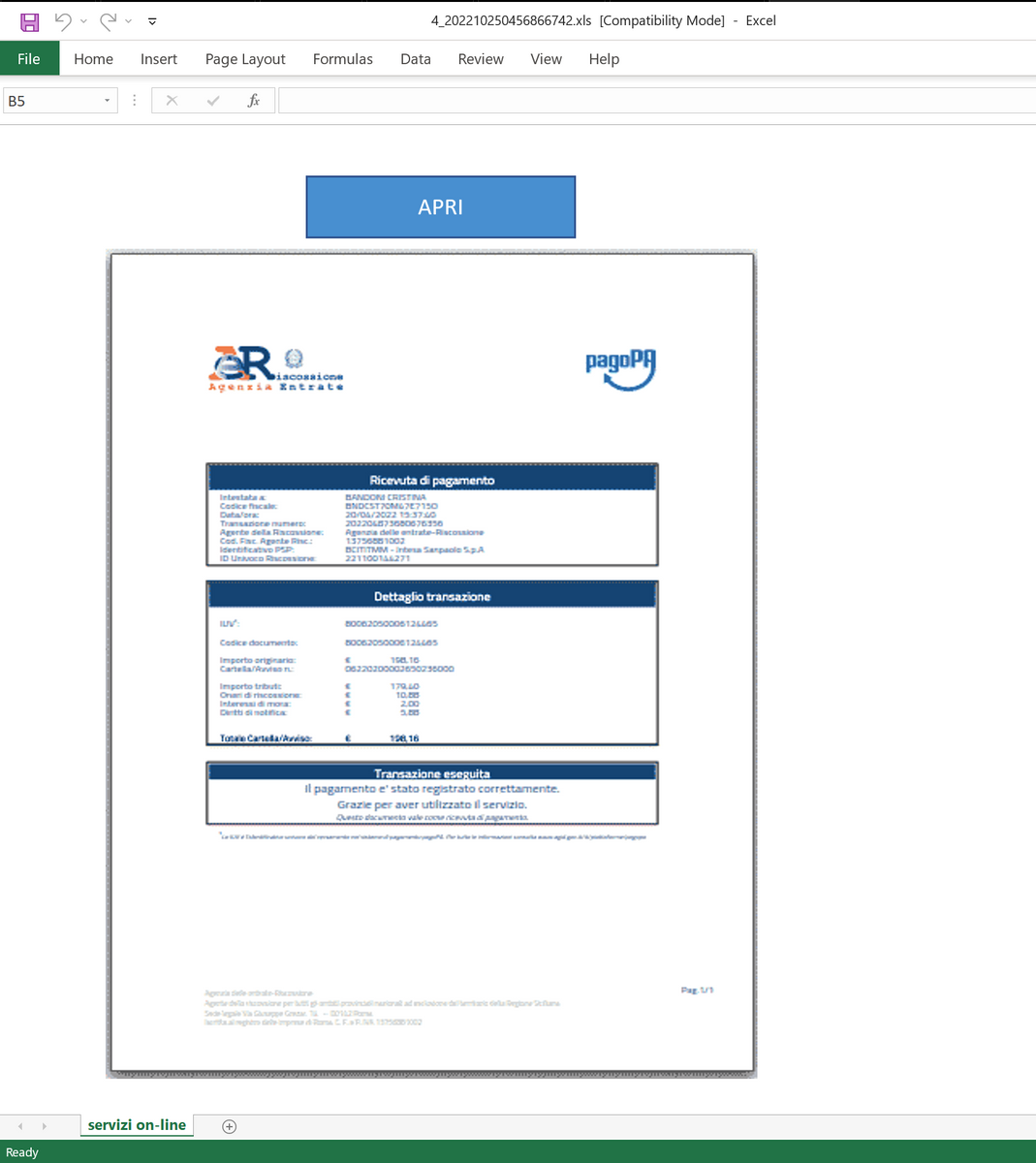
Key Takeaways The threat actor gained initial access by a fake Zoom installer that used d3f@ckloader and IDAT loader to drop SectopRAT. After nine days of dwell time, the SectopRAT malware dropped …| The DFIR Report