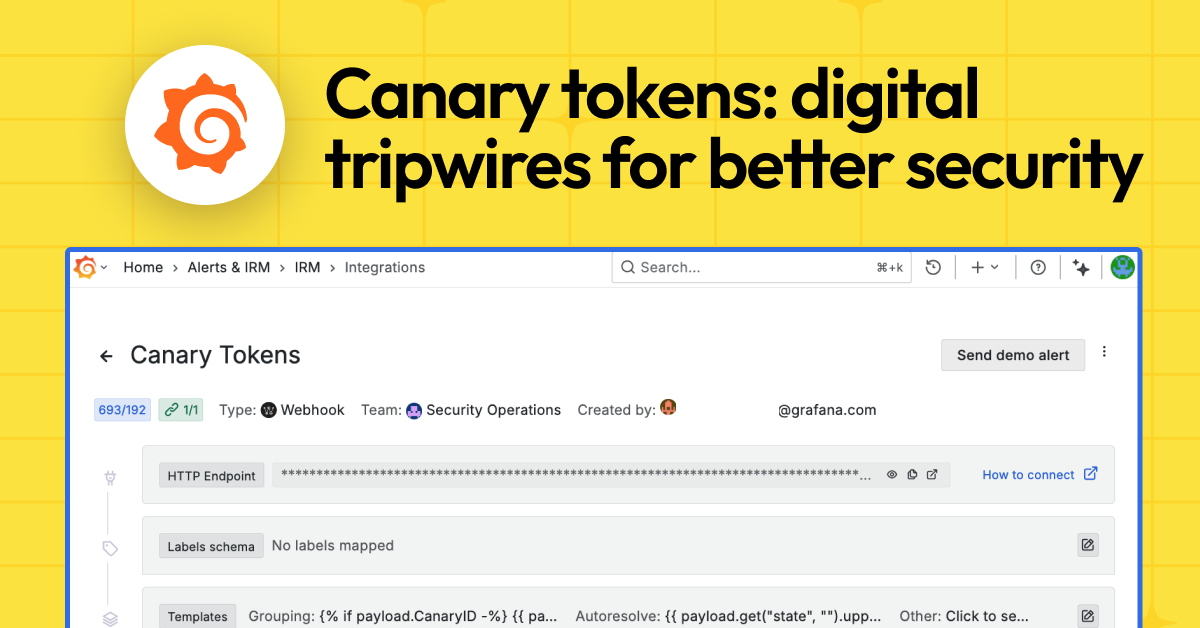
Canary tokens: Learn all about the unsung heroes of security at Grafana Labs | Grafana Labs
Learn why the use of canary tokens let us spot a recent intrusion and swarm quickly in response, and find out why you should be using canary tokens to prevent serious security incidents in the future.| Grafana Labs