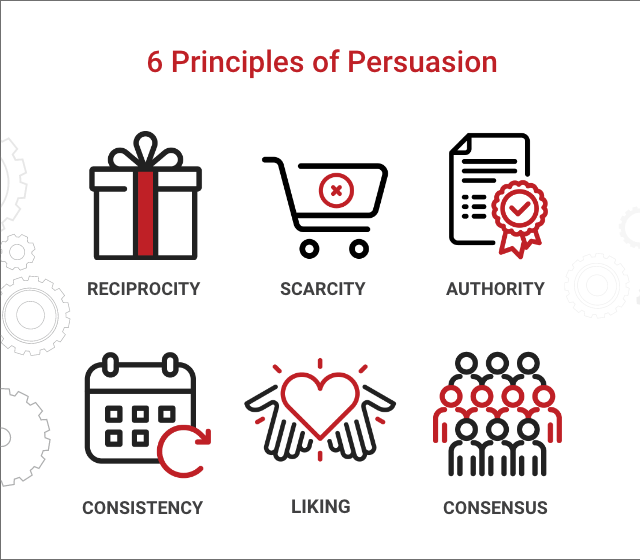
Dr. Robert Cialdini's Seven Principles of Persuasion | IAW
In the increasingly overloaded lives we lead, more than ever we need shortcuts or rules of thumb to guide our decision-making. Dr. Cialdini's research has identified six of these shortcuts as universals that guide human behavior.| Influence at Work