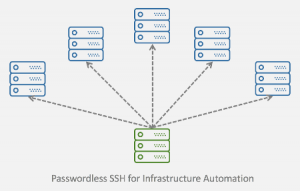
How to Configure and Use Passwordless SSH for Infrastructure Automation on Ubuntu | Amikelive | Technology Blog
In the previous post, we revisited SSH public key authentication protocol that brought passwordless SSH to life. We perused and summarized the RFCs. To visualize the authentication process, we drew…| Amikelive | Technology Blog