The Great iPwn: Journalists Hacked with Suspected NSO Group iMessage 'Zero-Click' Exploit - The Citizen Lab
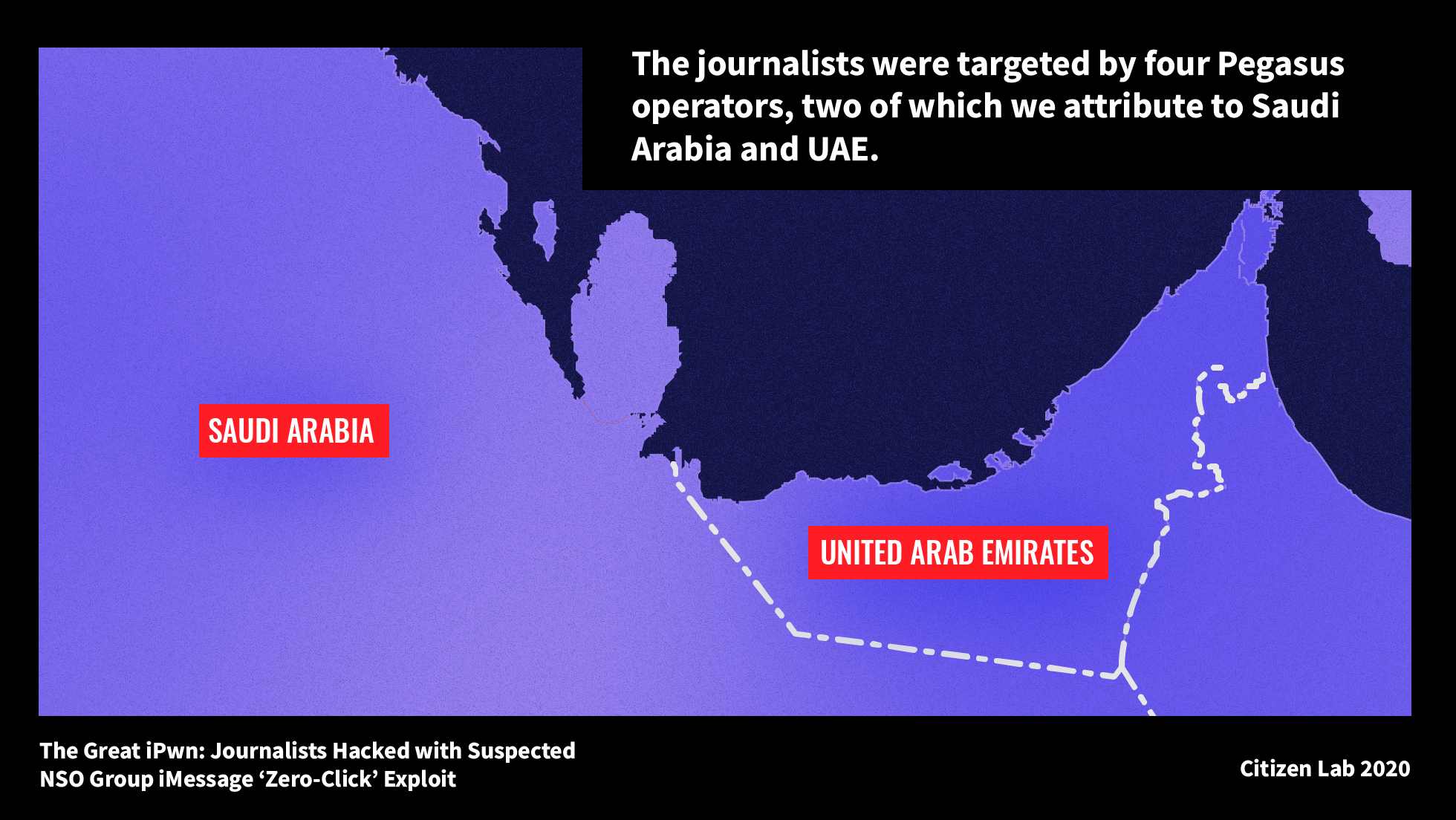
Government operatives used NSO Group’s Pegasus spyware to hack 36 personal phones belonging to journalists, producers, anchors, and executives at Al Jazeera. The journalists were hacked by four Pegasus operators, including one operator MONARCHY that we attribute to Saudi Arabia, and one operator SNEAKY KESTREL that we attribute to the United Arab Emirates.| The Citizen Lab