Risk Scoring in Silent Push Community and Enterprise Editions - Silent Push
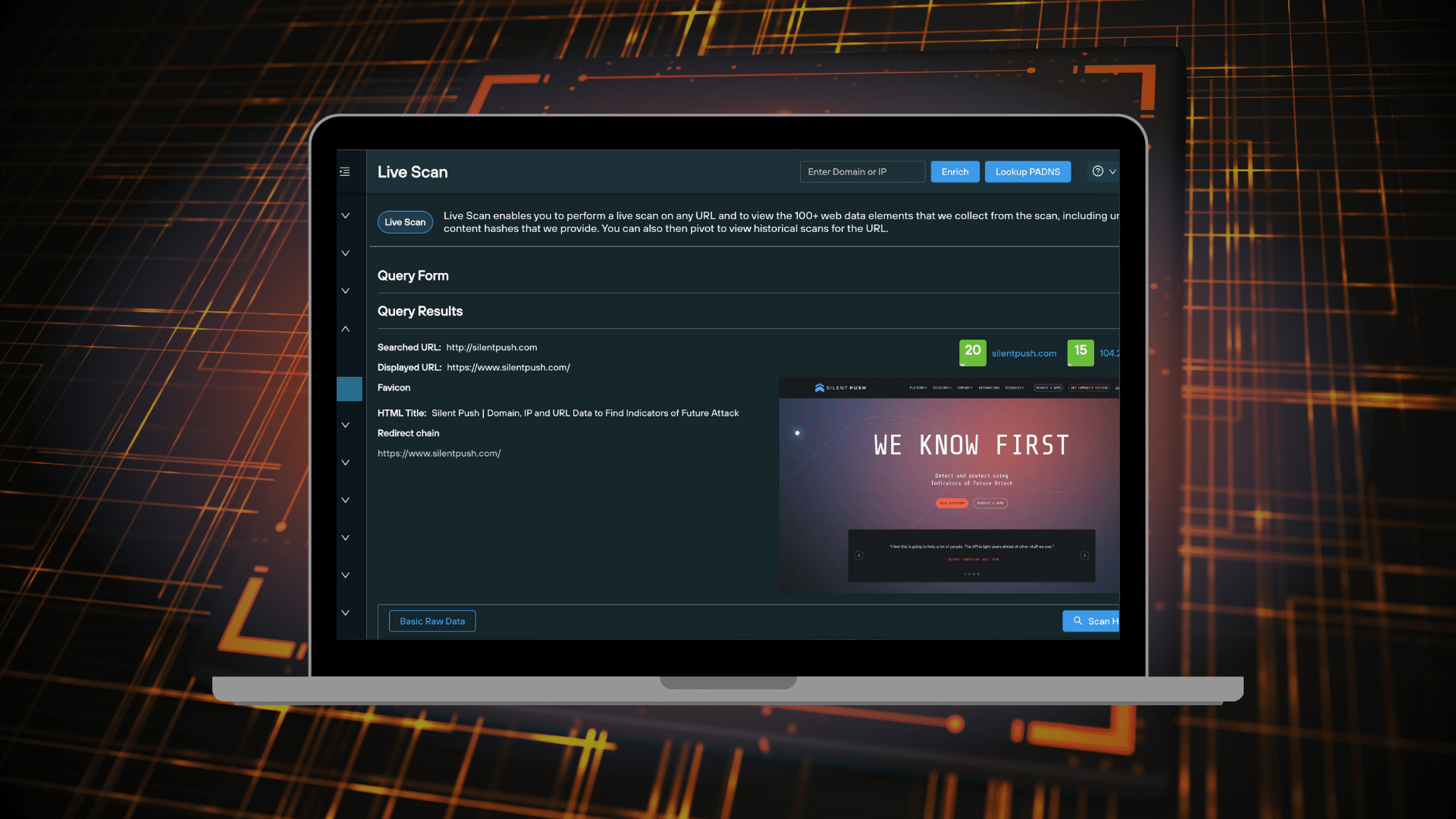
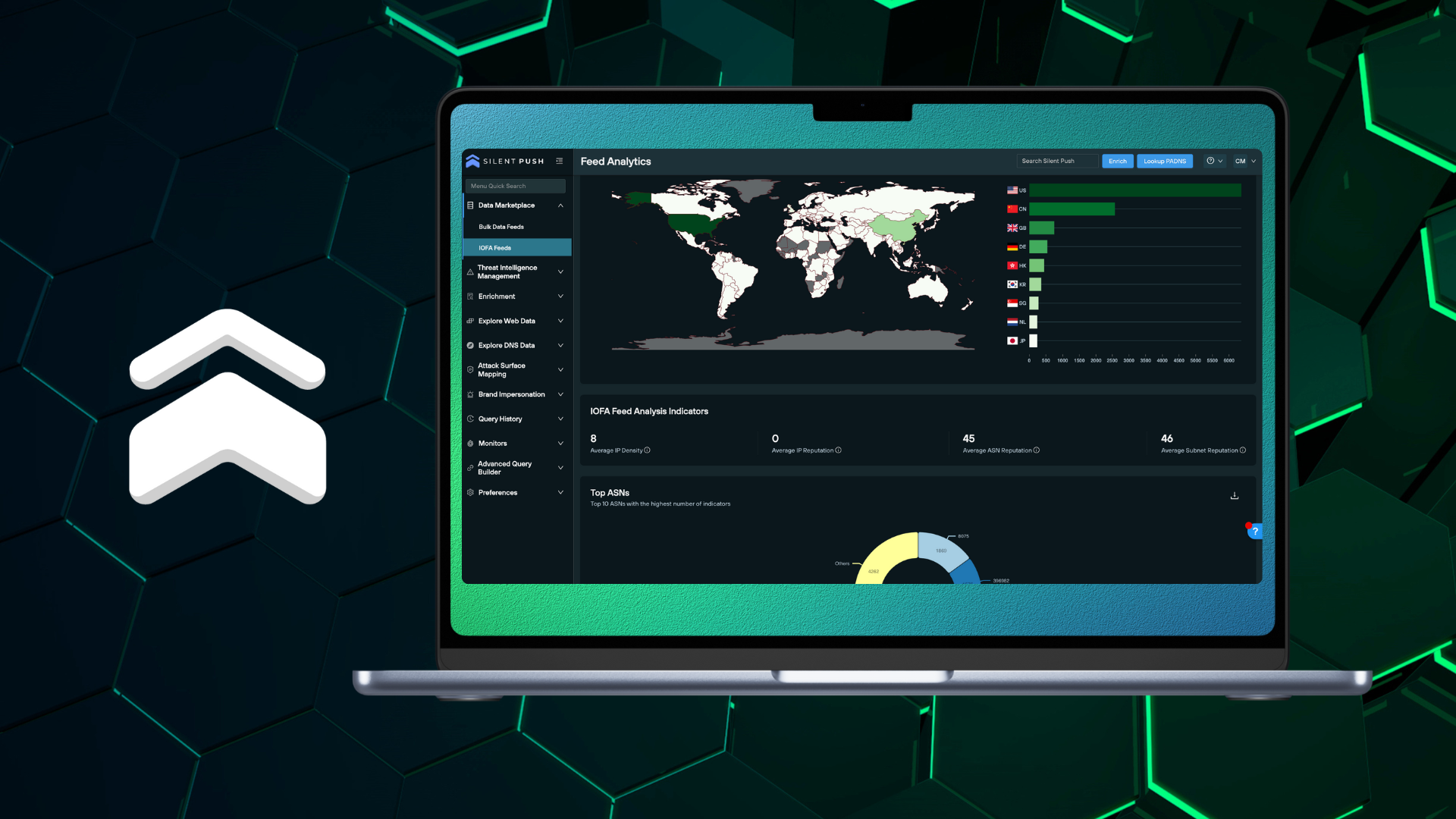
In this blog, we’ll take you through how the Silent Push console and API outputs risk scores, and how to utilize scoring methodologies to level-up your threat intelligence operation. We'll explain how each score is calculated, including the different factors we take into account, and how to operationalize the data.| Silent Push - We Know First