Fickling’s new AI/ML pickle file scanner -The Trail of Bits Blog
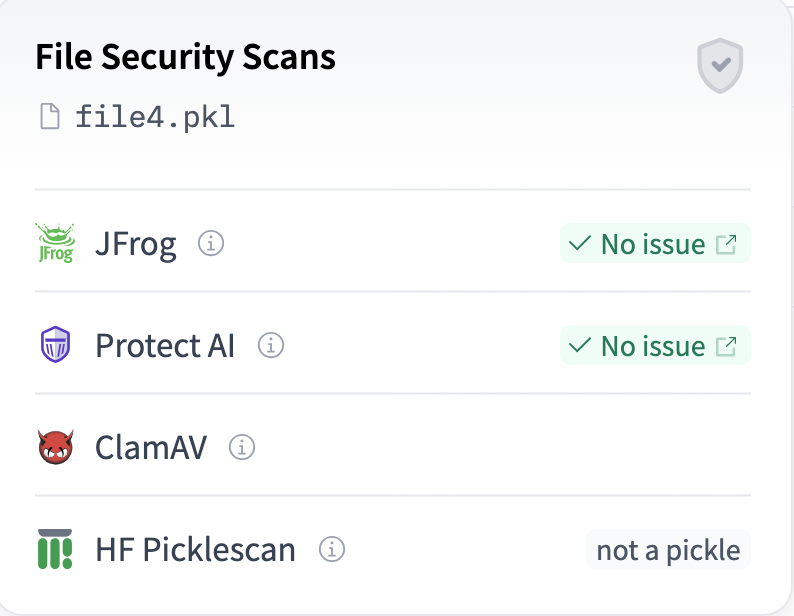
We’ve added a pickle file scanner to Fickling that uses an allowlist approach to protect AI/ML environments from malicious pickle files that could compromise models or infrastructure.| The Trail of Bits Blog