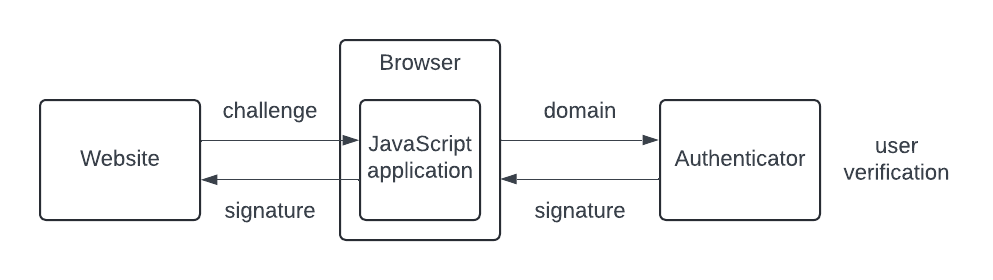
This post will examine the cryptography behind passkeys, the guarantees they do or do not give, and interesting cryptographic things you can do with them, such as generating cryptographic keys and storing certificates.| The Trail of Bits Blog
You’ve just completed a threat modeling exercise with us. You have our final report in hand. You’ve maybe even started remediating our findings! But threat modeling can only document the risks that were present in your system at the time of assessment. As you continue adding new components, security controls, and features, does our threat model still accurately describe your system? What new risks has your work introduced?| blog.trailofbits.com