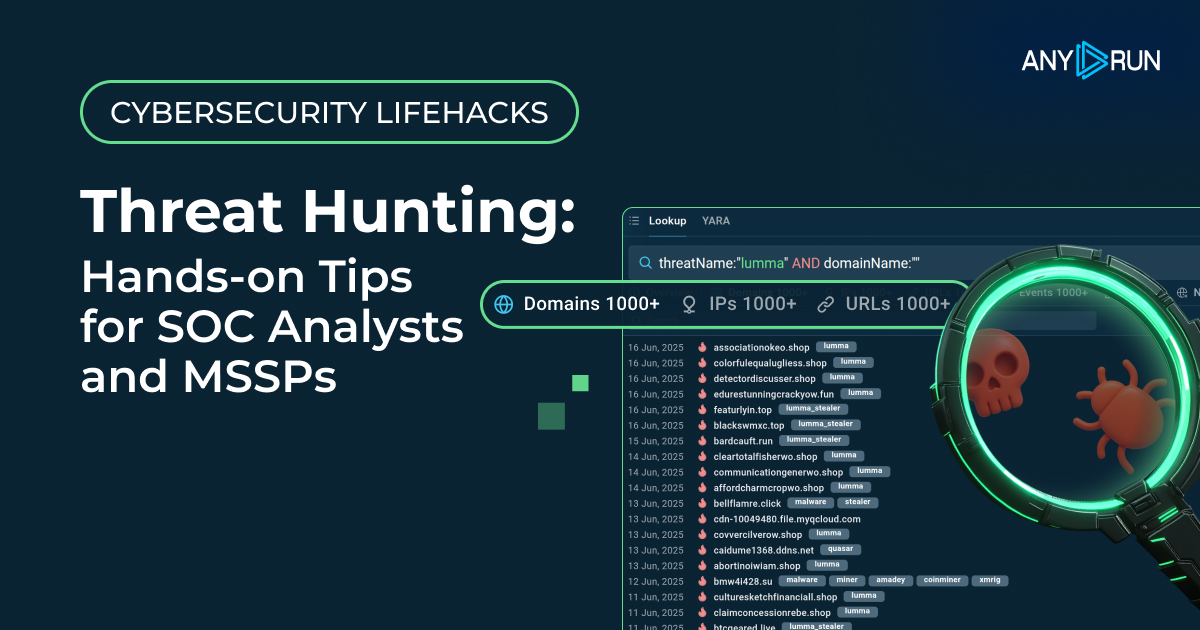
Bridging the Threat Intelligence Gap in Your SOC: A Guide for Security Leaders - ANY.RUN's Cybersecurity Blog
Find crucial steps to take as a CISO to empower your SOC operations with threat intelligence to mitigate risks and improve key metrics.| ANY.RUN's Cybersecurity Blog