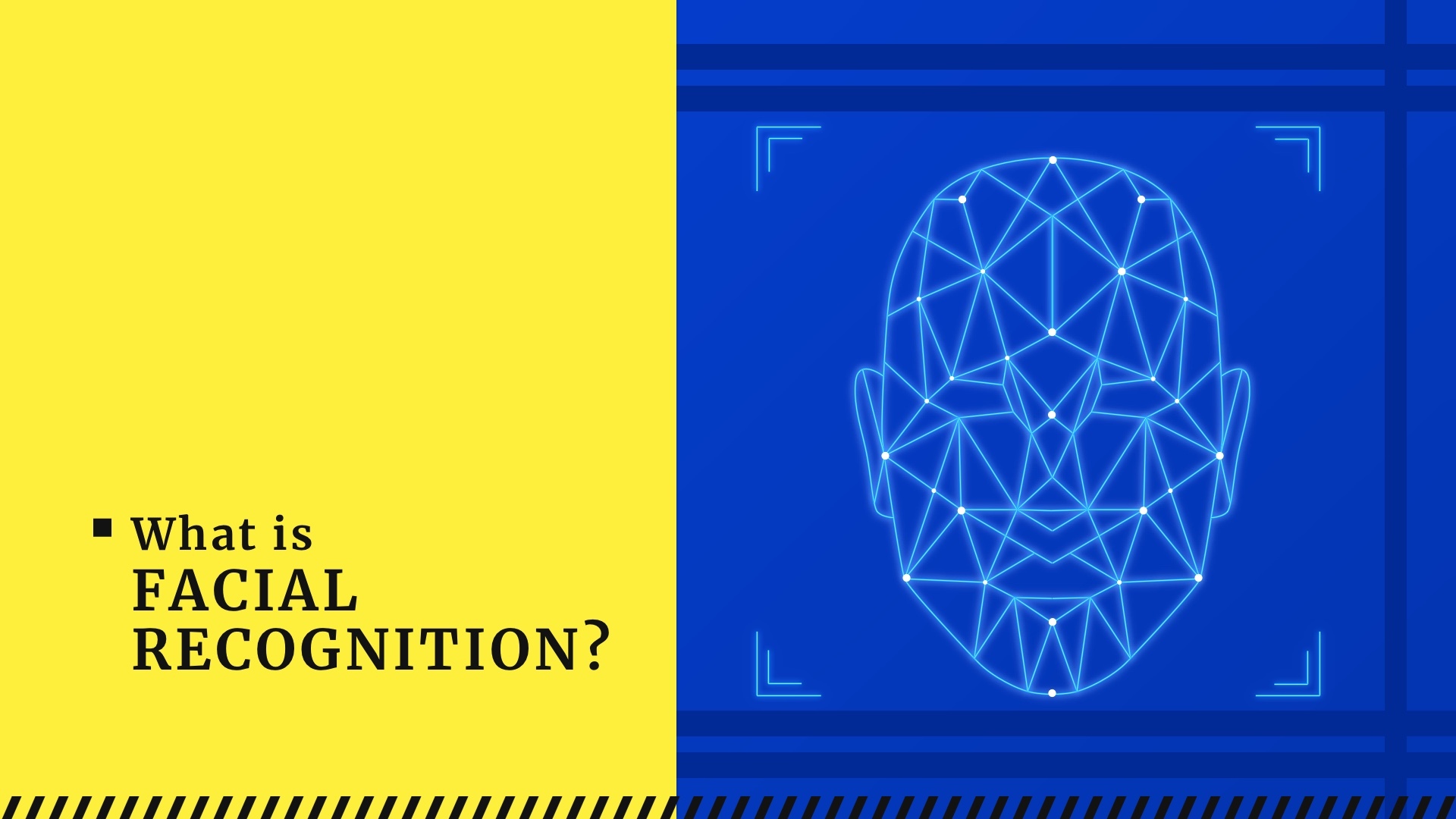
Facial Recognition technologies are the ways to identify a person and distinguish it from others. They are not new to the technological world but still have a lot of development potential.| Gridinsoft LLC
Insider threat is an exceptionally potent attack vector, which can open wide variety of other attack possibilities.| Gridinsoft Blogs
Phishing attack - What is Phishing attacks- How Does Phishing Work?-types of phishing attacks-how to prevent phishing attacks| Gridinsoft Blogs
Phishing is a unspoken pandemic. It is important to know how to avoid phishing emails and uncover them before its too late.| Gridinsoft Blogs
Protect You Personal Data: ✰ 1. Two-factor authentication ✰ 2. Antivirus protection ✰ 3. Firewall ✰ 4. Private Wi-Fi ✰ 5. Email Protection| Gridinsoft Blogs
Most Common Facebook Scams Today. Fraudsters develop new ways and methods to make an attack and remain unseen.| Gridinsoft Blogs