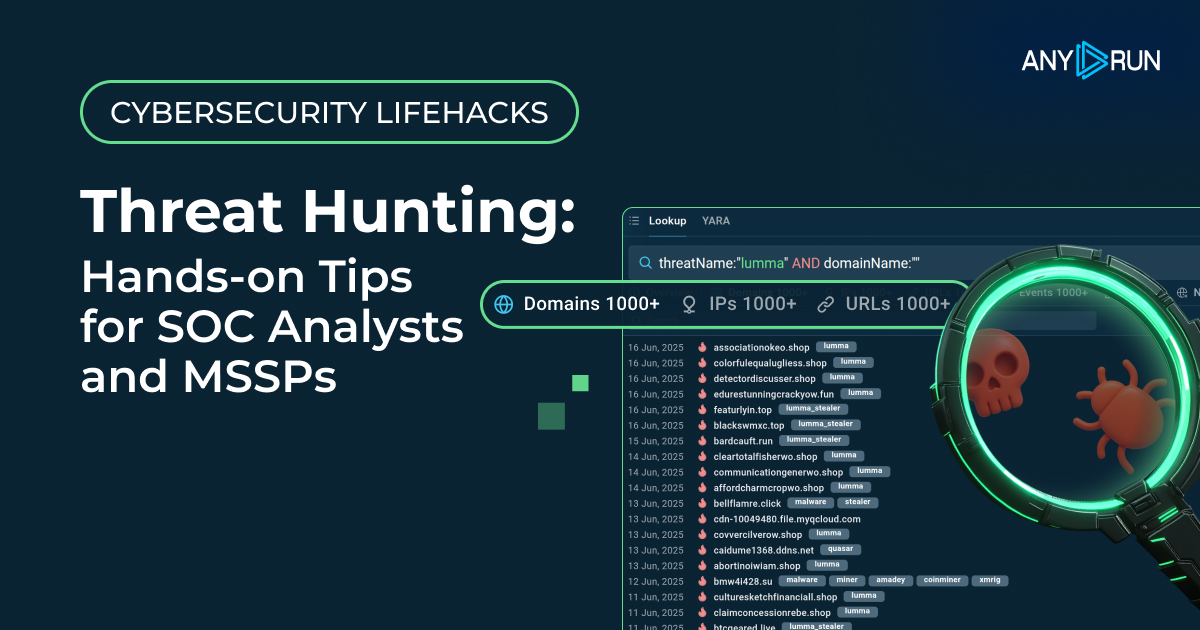
Threat Hunting: Hands-on Tips for SOC Analysts and MSSPs - ANY.RUN's Cybersecurity Blog
Learn actionable threat hunting techniques to proactively identify malware hidden inside your infrastructure and enrich your defense with fresh IOCs.| ANY.RUN's Cybersecurity Blog