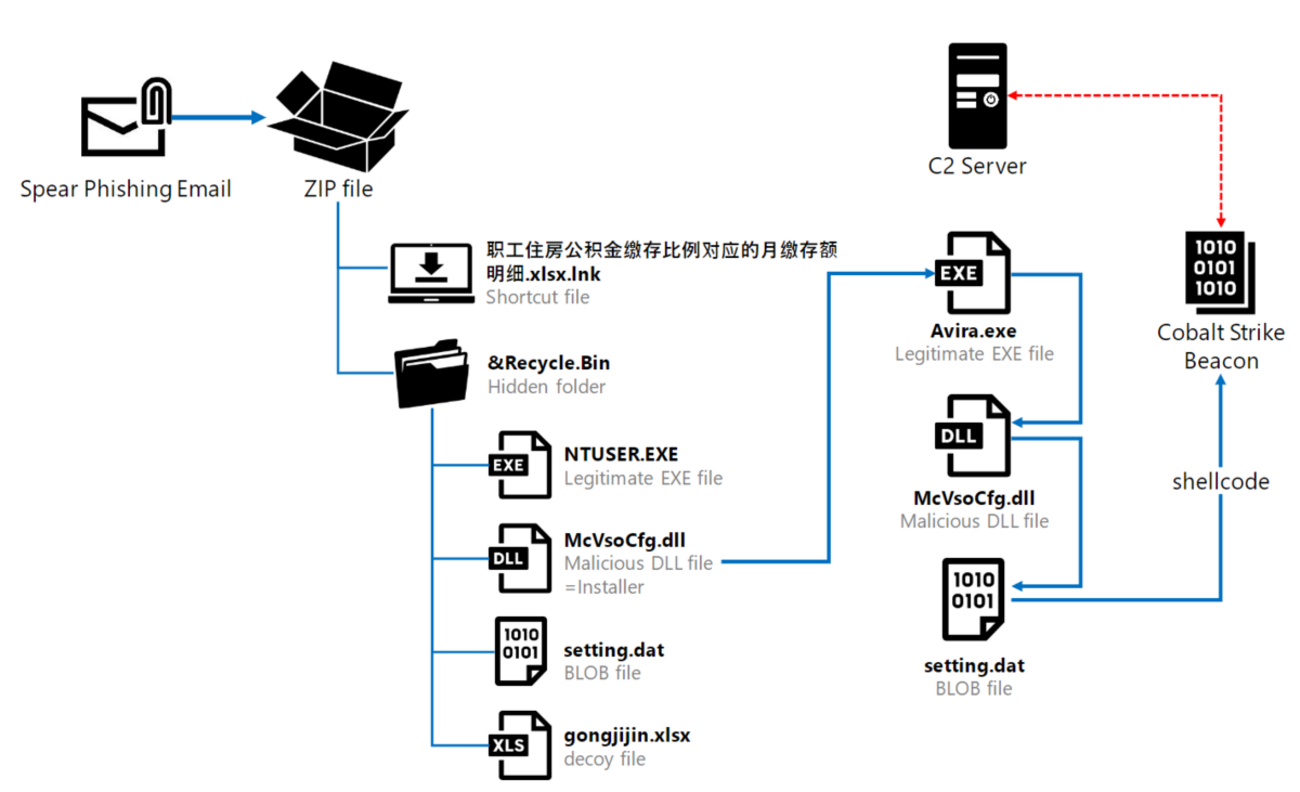
Windows Shortcut (LNK) Malware Strategies
Our telemetry shows a surge in Windows shortcut (LNK) malware use. We explain how attackers exploit LNK files for malware delivery. Our telemetry shows a surge in Windows shortcut (LNK) malware use. We explain how attackers exploit LNK files for malware delivery.| Unit 42