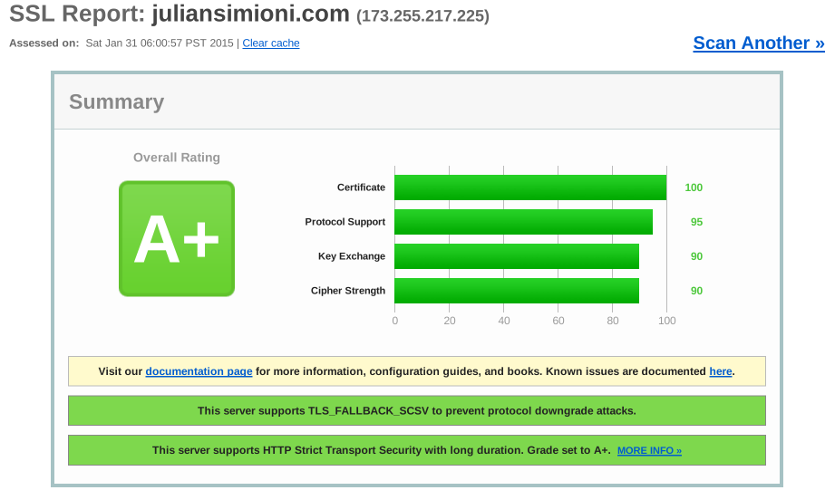
HTTPS on Nginx: From Zero to A+ (Part 2) - Configuration, Ciphersuites, and Performance - Julian Simioni
On the internet today, all our web sites need a strong, secure HTTPS setup, even the most basic static sites. This is part two of a series on how to set up Nginx securely. When we left off after …| juliansimioni.com