Abusing and Detecting LOLBIN Usage of .NET Development Mode Features – bohops
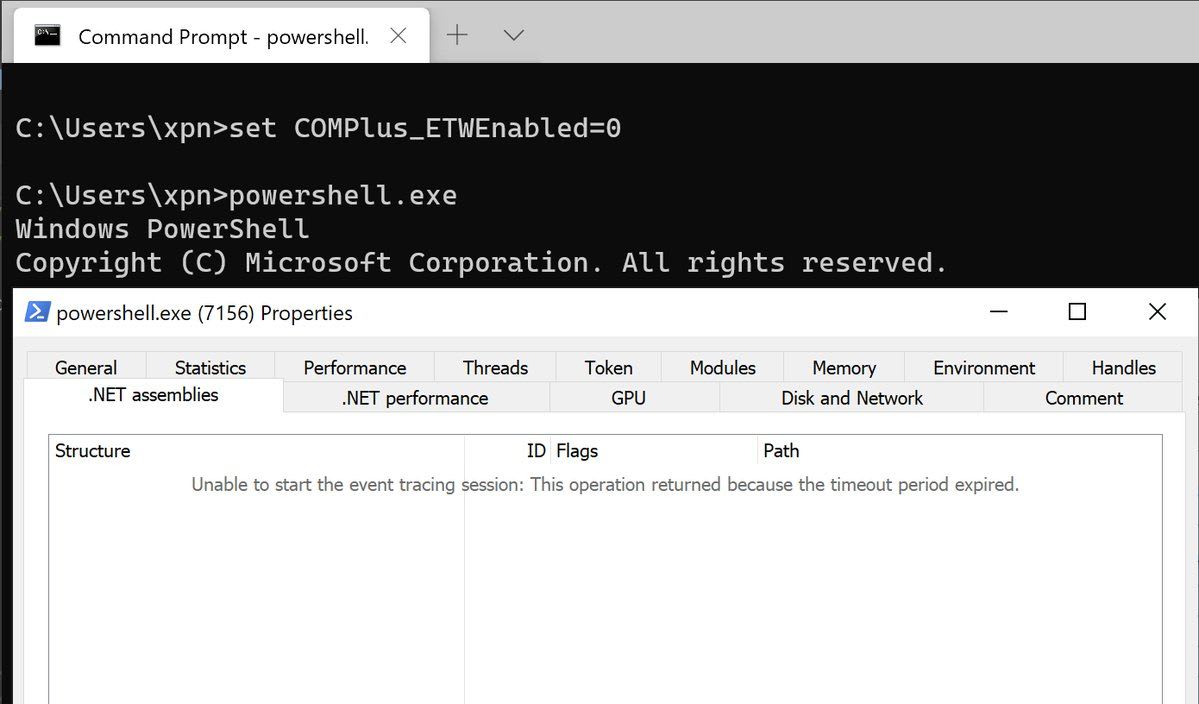
Background As discussed in this previous post, Microsoft has provided valuable (explicit and implicit) insight into the inner workings of the functional components of the .NET ecosystem through onl…| bohops