Web Application Security, Testing, & Scanning - PortSwigger
PortSwigger offers tools for web application security, testing, & scanning. Choose from a range of security tools, & identify the very latest vulnerabilities.| portswigger.net
Top 12 Dynamic Application Security Testing (DAST) Tools in 2026 | Aikido Security
Discover the 12 top best Dynamic Application Security Testing (DAST) tools in 2026. Compare features, pros, cons, and integrations to choose the right DAST solution for your DevSecOps pipeline.| www.aikido.dev
How to Guess a Password: Your 2026 Guide
Discover how to guess a password using various tools and techniques. Our guide provides practical strategies for discovering passwords.| StationX
Web Application Penetration Testing Steps and Test Cases
Explore the essential steps and test cases for web application penetration testing to identify and address security vulnerabilities. Learn how to systematically evaluate your| Strobes Security
Empfehlungsecke • Kuketz IT-Security Blog
Empfehlungsecke des Kuketz-Blogs: Tools, Dienste und Tipps für digitale Souveränität • IT-Sicherheit, Datenschutz und digitale Selbstverteidigung| www.kuketz-blog.de
Out-of-Band Application Security Testing (OAST) Software - PortSwigger
OAST security testing uses external servers to see otherwise invisible vulnerabilities. Find out more about our security testing solutions.| portswigger.net
サイボウズサマーインターン2024 プロダクトセキュリティコース 開催報告 - Cybozu Inside Out | サイボウズエンジニアの...
こんにちは!Cy-PSIRTの田口です。 本記事はサイボウズ サマーインターンシップ2024 プロダクトセキュリティコースの開催報告です。 今年は8月に1ターム、昨年と同様にフルリモートで開催しました。 概要 プロダクトセキュリティコースは8月26日〜29日で開催し、3名のインターン生にご参加いただきました。 インターンでは、普段Cy-PSIRTが行っている業務をベースにコン...| Cybozu Inside Out | サイボウズエンジニアのブログ
What Is Penetration Testing | Flatiron School
What is penetration testing? Flatiron School cybersecurity students learn about pen tests and how they compromise network security.| Flatiron School
Testing OWASP's Top 10 API Security Vulnerabilities | Nordic APIs |
There are ten top security vulnerabilities for APIs. Here's how to test your services for them, along with helpful tools to avoid these most common flaws.| Nordic APIs
Essentials of Automotive Penetration Testing - Apriorit
Looking to improve your vehicle software security? Discover how to efficiently apply penetration testing in automotive systems.| Apriorit
Web app testing guide: 8 important types
Learn different types of web application testing and their purposes: 1. Functionality testing 2. Usability testing 3. Interface testing + more.| Hostinger Tutorials
Best Kali Linux Tools 2025: The Ultimate Arsenal for Ethical Hackers - Homes for Hackers
Kali Linux is the go-to operating system for penetration testers, security researchers, and ethical hackers. Every year, it evolves, bringing in more powerful tools to help professionals assess and fortify cybersecurity. If you're looking to explore the best Kali Linux tools in 2025, you're in the right place. This year, the toolkit is more refined,| Homes for Hackers - Learn Ethical Hacking & Penetration Testing
25 Top DevSecOps Tools (Ultimate Guide for 2025)
Discover 25 essential DevSecOps tools for a secure development lifecycle and learn how to create a more resilient environment for your applications.| StationX
Block YouTube Ads on AppleTV by Decrypting and Stripping Ads from Profobuf
Apple TV and iOS YouTube ads are not blocked by Pi-hole, so I researched this and discovered a flaw in Protobuf that allows me to restrict YouTube ads.| ericdraken.com
Login - PortSwigger
PortSwigger offers tools for web application security, testing & scanning. Choose from a wide range of security tools & identify the very latest vulnerabilities.| portswigger.net
9 Best Vulnerability Scanning Tools - Sprinto - Sprinto
Vulnerability scanning tools help identify security weaknesses in your systems. Learn how they work and why they're essential for cybersecurity.| Sprinto
Internal Security Audit Checklist for Increasing Product Quality | Apriorit
Learn how internal security audits can increase the quality of your product. Use our checklist to ensure the robust security of your application.| Apriorit
A Complete Guide to Penetration Testing - All You Need To Know
In this guide, we discuss the types of Pen Tests including Web App Pen Testing and Mobile App Pen Testing. Download your free guide today!| Evalian®
7 Essential Considerations for API Automation Testing | AutoKitteh
API automation testing helps them validate API functionality and performance and improve code coverage with minimum effort. Learn more.| autokitteh
Burp Scanner - Web Vulnerability Scanner from PortSwigger
Burp Scanner is the industry's gold standard dynamic web vulnerability scanner. Start vulnerability scanning today with a free trial of Burp Suite.| portswigger.net
Shambles: The Next-Generation IoT Reverse Engineering Tool to Discover 0-Day Vulnerabilities
Simplifying the discovery of IoT/ICS 0-days. Revolutionizing embedded systems reverse engineering in a tool for everyone.| Boschko Security Blog
Web Application Penetration Testing: Steps, Methods, & Tools
Web application penetration tests are performed primarily to maintain secure software code development throughout its lifecycle.| PurpleSec
Offensive Security 101: Guide to Proactive Cyber Defense
Offensive security proactively identifies vulnerabilities before attackers exploit them. Learn how it strengthens cybersecurity and reduces risks.| Strobes Security
Exploiting a JDBC deserialization vulnerability in MFT Server by JSCAPE | Markuta
A technical blog post on finding and exploiting an authenticated JDBC deserialization vulnerability in JSCAPE MFT Server to gain remote command execution. This vulnerability is caused by an out-of-date H2 database library bundled into the default install package. A proof of concept is provided that works on Windows x64.| Markuta
Security autotests for measurable and stable application security processes | Cossack Labs
Security automation contributes to measurable improvements: stable security processes and efficient assessments that save time and effort. Security-focused pre-built templates covering prevalent security testing scenarios that can be customised and tailored to your specific needs.| Cossack Labs
What is API Discovery, and How to Use it to Reduce Your Attack Surface
APIs are the bilingual translators of the software world, enabling applications to communicate with one another seamlessly.| open-appsec
50 Online Tools Every Cyber Security Professional Should Know About
50 Online Tools Every Cyber Security Professional Should Know AboutThere a notion in cyber security that the job of a cyber aggressor is much easier than that of a cyber security professional. Cyber assailants just need to get right once to wreak havoc on the systems and devices within a defending network. A defending network has to get security right 100% of the time to remain secure. With the range of newly connected devices growing exponentially (think tracking beacons, refrigerators, and ...| www.cybersecuritydegrees.com
Web Security Academy: Free Online Training from PortSwigger
The Web Security Academy is a free online training center for web application security, brought to you by PortSwigger. Create an account to get started.| portswigger.net
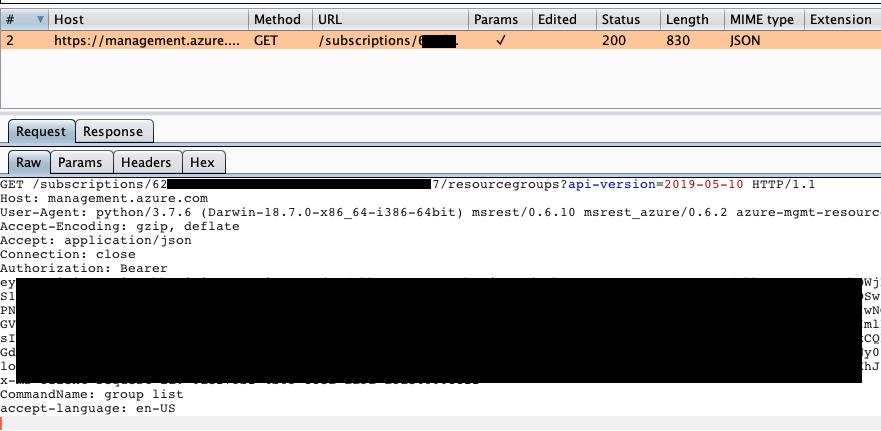
Proxying and Intercepting CLI Tools - ropnop blog
Sometimes you need to intercept traffic from CLI tools. In this post I cover using Burp to intercept traffic from Java, Python, Node and Go CLIs| ropnop blog
Top 10 CI/CD Security Tools - Spectral
On the one hand, your sales department is pushing for new features at an alarming rate, forcing you into faster deployment processes. On the other hand,| Spectral
RCE on Spip and Root-Me • Think Love Share
Vulnerability research write-up on spip, the web framework used by root-me.org. The issues found goes from XSS to RCE, passing by SQLi!| thinkloveshare.com
Stripe is Silently Recording Your Movements On its Customers' Websites · mtlynch.io
An investigation into how Stripe tracks your users and what you can do to prevent it| mtlynch.io