AppLocker Rules as Defense Evasion: Complete Analysis | Splunk
The Splunk Threat Research Team analyzes 'Azorult loader' (a payload that imports its own AppLocker rules) to understand the tactics and techniques that may help defend against these types of threats.| Splunk
10 Critical Security Gateway Exploitations
Security gateways are designed to be trusted. They sit in front of authentication, terminate VPNs, and decrypt traffic before it enters the network. When Ten real-world security gateway exploits showing how VPNs, firewalls, and gateways were compromised and why attacker access often persisted long after patching.| HackerTarget.com
Moltbot Personal Assistant Goes Viral – And So Do Your Secrets
Early 2026, Moltbot a new AI personal assistant went viral. GitGuardian detected 200+ leaked secrets related to it, including from healthcare and fintech companies. Our contribution to Moltbot: a skill that turns secret scanning into a conversational prompt, letting users ask "is this safe?"| GitGuardian Blog - Take Control of Your Secrets Security
Shai-Hulud 2.0: the supply chain attack that learned
On November 24, a new wave of the Shai-Hulud supply chain attack emerged. The threat actors exfiltrate stolen credentials directly to GitHub repositories created with compromised tokens.| GitGuardian Blog - Take Control of Your Secrets Security
Immutable Strings in Java - Are Your Secrets Still Safe? - Include Security Research Blog
Java programmers might not be aware their secrets could be floating around in system memory long after it's assumed those secrets have been removed. The problem is a combination of immutability and garbage collection in Java. Our most recent post explores the unpredictability of Java garbage collection and the implications that has for secrets in code. We developed a simple proof of concept designed to measured these "secret ghosts" and demonstrate how to avoid them.| Include Security Research Blog
Production Security, Not That Kind - Include Security Research Blog
The Include Security team takes a foray into the world of audio production equipment in our latest blog post. We look under the hood of a professional-grade audio mixer to explore its security profile, consider how its functionality could be leveraged by an attacker in a real world setting, and develop a proof-of-concept exploit to demonstrate quick n' easy privilege escalation.| Include Security Research Blog
A File Format to Aid in Security Vulnerability Disclosure
When security vulnerabilities are discovered by researchers, proper reporting channels are often lacking. As a result, vulnerabilities may be left unreported.| Colin Cogle's Blog
DNS pivoting: Attack surface discovery through DNS
Expand your attack surface view with DNS pivoting. Follow DNS records, subdomains, Reverse IP and Zone transfers to map attack surfaces.| HackerTarget.com
The GhostAction Campaign: 3,325 Secrets Stolen Through Compromised GitHub Workflows
On September 5, 2025, GitGuardian discovered GhostAction, a massive supply chain attack affecting 327 GitHub users across 817 repositories. Attackers injected malicious workflows that exfiltrated 3,325 secrets, including PyPI, npm, and DockerHub tokens via HTTP POST requests to a remote endpoint.| GitGuardian Blog - Take Control of Your Secrets Security
Joomla Security Testing Guide 2025 : Recon and Exploitation
From passive recon to active exploitation, this Joomla 2025 guide shows the techniques attackers use. Explore common vulnerabilities and attack techniques A 2025 Joomla security testing guide with enumeration methods and exploitation techniques.| HackerTarget.com
Offensive security tools 2025
Offensive security tools for 2025: Metasploit, Nuclei, Bloodhound & more. Uncover and remediate vulnerabilities before they’re exploited.| HackerTarget.com
Claude Code is more than just Coding
Following recent updates I felt it was time to give Claude Code a spin. One thing that has jumped out after using it for a few days is that this is not only a code development tool for programmers. It is far more capable and perhaps even an "agentic" platform for anything you do on […] The post Claude Code is more than just Coding appeared first on HackerTarget.com.| HackerTarget.com
Giving an LLM Command Line Access to Nmap | HackerTarget.com
What would it look like giving LLM's command line access to Nmap. Explore the possibilities in the security tools space.| HackerTarget.com
Is App Attestation on Android and iOS Secure? | Guardsquare
Android and iOS app attestation services help developers protect apps, but security gaps exist. Learn key features to seek in mobile app attestation.| www.guardsquare.com
Cyberchef Tutorial and Tips
CyberChef is a versatile tool for beginners and experts, offering powerful features for easy data handling and analysis.| HackerTarget.com
Replacing a Space Heater Firmware Over WiFi - Include Security Research Blog
Our team hacks space heater firmware updates over wifi in the latest Include Security blog post. We break down, literally and figuratively, each step of the attack to demonstrate how anonymous users on the same wireless network as an affected space heater could overwrite its firmware causing it to behave in unpredictable and potentially dangerous ways!| Include Security Research Blog
Nmap Dashboard with Grafana
Generate an Nmap Dashboard using Grafana and Docker to get a clear overview of the network and open services. This weekend's project uses a similar technique to the previous Zeek Dashboard to build an easy to deploy dashboard solution for Nmap results. Building small deployments like this gives the operator a greater understanding of how […] The post Nmap Dashboard with Grafana appeared first on HackerTarget.com.| HackerTarget.com
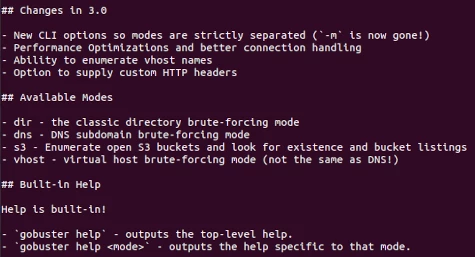
Gobuster tutorial
You would be surprised at what people leave unprotected on a web server. An initial step in attacking a web application is Recon, and part of that entails| HackerTarget.com
Vulnerabilities in Open Source C2 Frameworks
Our latest post focuses on the command and control (C2) software frameworks used by professional offensive security red teams and criminal organizations alike. We dived into the source code of multiple high-profile, open-source C2s and discovered vulnerabilities in most of them. In this post, we provide a brief overview of C2 concepts, review the details of the frameworks' identified vulnerabilities (with nifty reproduction gifs included!), and conclude with some final thoughts about the curr...| Include Security Research Blog
API Threat Landscape: New Resource for API Security Research
Since 2022, Escape's security research team has been tracking API-related data breaches. We’ve decided to make our database public, providing detailed insights into primary attack vectors, threat actors, tools, and techniques. The database is updated every two weeks.| Escape DAST - Application Security Blog
Discovering Deserialization Gadget Chains in Rubyland - Include Security Research Blog
If you have ever looked at the source code of a Ruby deserialization gadget chain, I bet you've thought "what sorcery is this"?| Include Security Research Blog
Snort Tutorial and Practical Examples | HackerTarget.com
In this Snort tutorial you will not only get started with this powerful tool but also find practical examples and immediate use cases.| HackerTarget.com