The US False Claims Act Becomes a Cybersecurity Enforcement Engine
For years, many government contractors treated cybersecurity compliance as a technical checklist, important, certainly, but often siloed within IT departments. That mindset is no longer tenable. The U.S. Department of Justice (DOJ) has announced that cybersecurity representations to the federal government are now squarely within the enforcement core of the False Claims Act (FCA). What began in October 2021 as the Civil Cyber-Fraud Initiative has matured into a sustained and expanding enforce...| Cyble
Compromised Routers, DNS, and a TDS Hidden in Aeza Networks
When most people say DNS, they are thinking about the global DNS system, the official mechanism for resolving domain names on the internet. But shadow systems exist. Visiting a website relies on a DNS resolution chain that iteratively queries authoritative name servers within the distributed DNS hierarchy to get an IP address. This resolution all […] The post Compromised Routers, DNS, and a TDS Hidden in Aeza Networks appeared first on Infoblox Blog.| Infoblox Blog
The Dangers of Cracking Tools | The Sequence
Cracking tools often introduce hidden vulnerabilities. Learn how real exploits and a macOS privilege escalation put systems at risk.| the-sequence.com
Enriched Actor Profiles in Cerberus
Actor Profiles in Cerberus are now enriched with temporal data and clear visualizations, making it faster for investigators to gather intelligence and de-anonymize actor aliases. Contact sales| Searchlight Cyber
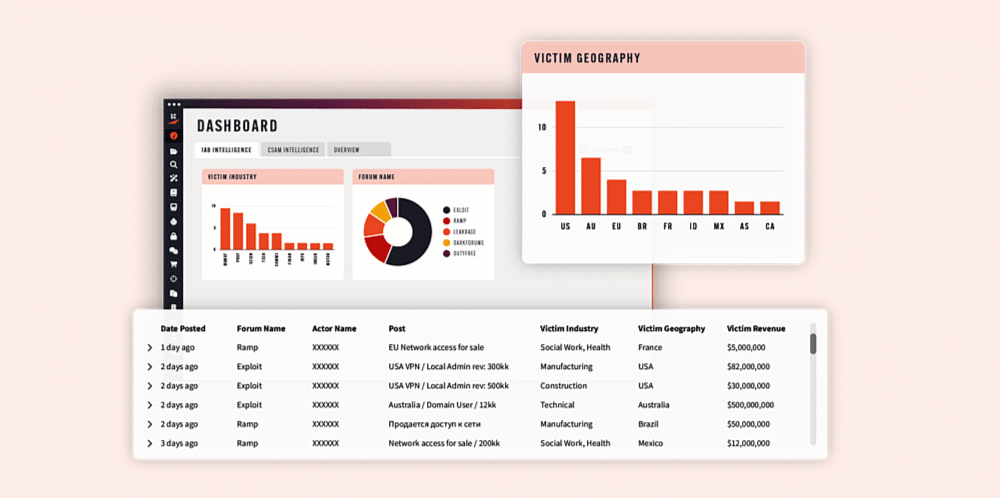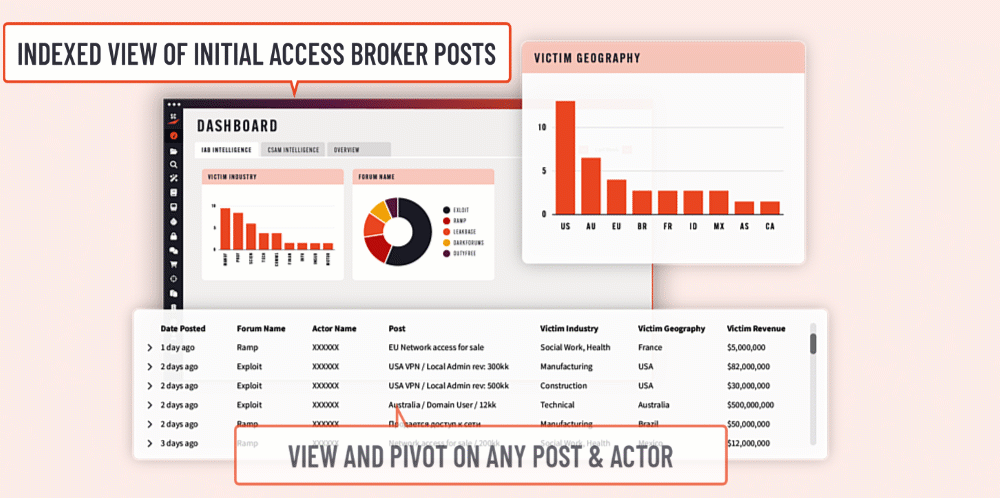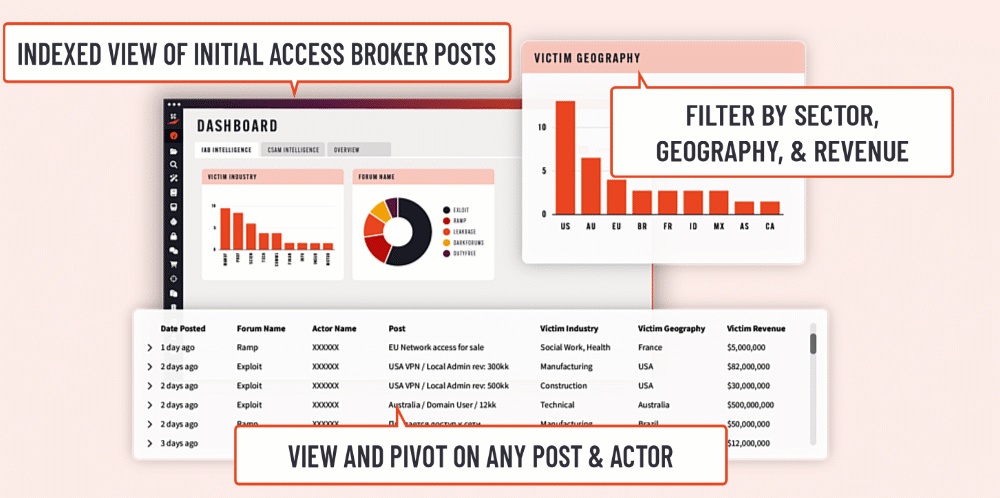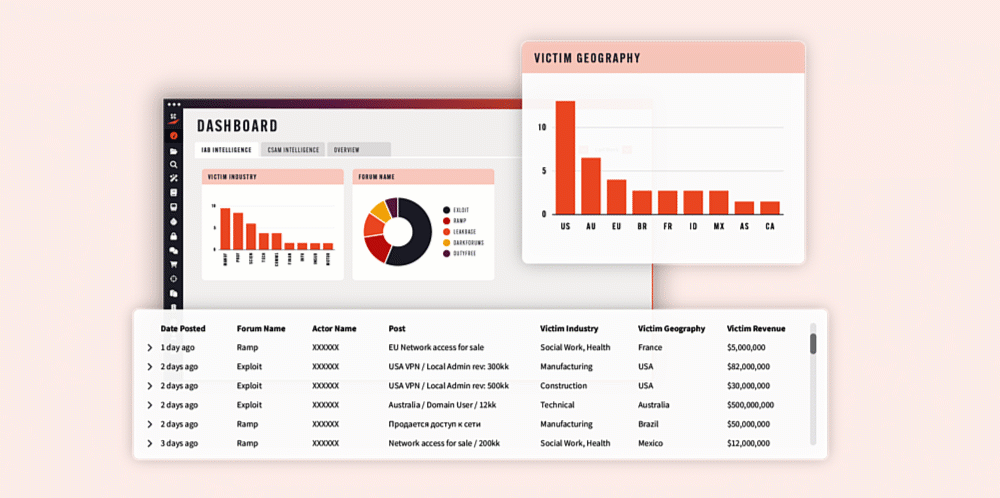
Introducing the Initial Access Broker (IAB) Dashboard › Searchlight Cyber
The new IAB dashboard helps teams detect pre-attack indicators more efficiently, enabling faster identification of unauthorized network access to you or a partner – before it can be sold and exploited. Contact sales| Searchlight Cyber
The Human Layer of Security: Why People are Still the Weakest Link in 2026
By 2026 humans remain cybersecurity’s weakest—and most vital—link as AI-enabled social engineering rises; prioritize behavioral design, real‑time interventions, and leadership. The post The Human Layer of Security: Why People are Still the Weakest Link in 2026 appeared first on Security Boulevard.| Security Boulevard
NSFOCUS Monthly APT Insights – December 2025
Regional APT Threat Situation In December 2025, the global threat hunting system of Fuying Lab detected a total of 24 APT attack activities. These activities were primarily concentrated in regions including South Asia, East Asia, with a smaller portion also found in Eastern Europe and South America. Some organizations remain unattributed to known APT groups, […] The post NSFOCUS Monthly APT Insights – December 2025 appeared first on NSFOCUS, Inc., a global network and cyber security leade...| NSFOCUS, Inc., a global network and cyber security leader, protects enterpris...
Why Are Ransomware Attacks Becoming More Common, and How to Handle Them
Ransomware attacks are no longer rare, targeted incidents. They are repeatable, automated, and profitable operations that scale across industries. For CISOs, IT leaders, and infrastructure providers, this shift matters right now. Ransomware is moving faster than traditional defenses, exploiting gaps outside the enterprise perimeter and hitting organizations that thought they were “well protected.” In this […] The post Why Are Ransomware Attacks Becoming More Common, and How to Handle Th...| Cybersecurity Solutions | Email & Network Security
How to prevent a rootkit attack - ThreatDown by Malwarebytes
Rootkit attacks are considered one of the most dangerous cyberthreats today. Learn what they are, how they infect systems, and how to protect against them.| ThreatDown by Malwarebytes
Ransomware Attacks And Supply Chain Threats In 2025
Ransomware attacks and supply chain attacks surged in 2025. Review key data, threat actors, targeted sectors, and trends shaping 2026 risks.| Cyble
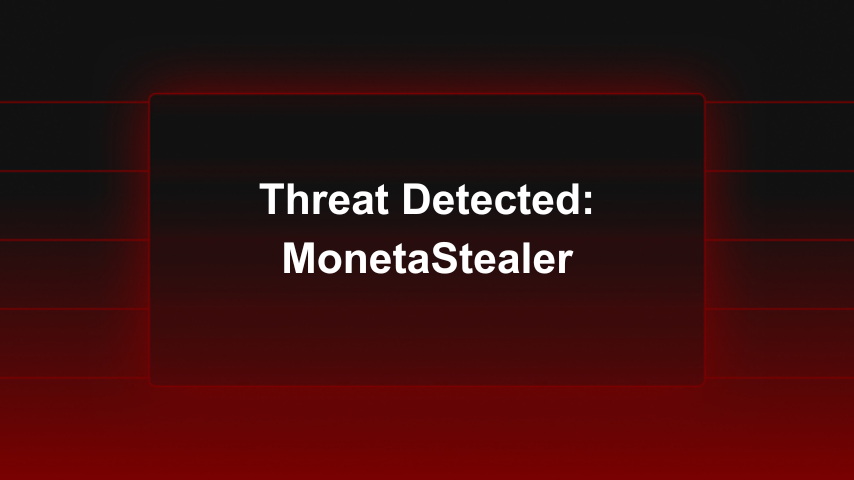
Analyzing the MonetaStealer macOS Threat | The Sequence
Learn how MonetaStealer targets macOS users, what it steals, and why early-stage malware still poses real risk.| the-sequence.com
Cyber-Risiko: Fake IT-Mitarbeiter (Tipps für HR und SOC included)
Die Schatten-Kollegen: Warum dein neuer Senior-Entwickler vielleicht für Pjöngjang arbeitet| Tizian Kohler
What Regulations and Compliance Requirements Can a Threat Intelligence Feed Like Guardian Intel Help With?
Security teams are no longer judged only on whether they stop attacks. Regulators increasingly care about how quickly threats are detected, whether action is taken, and if there is evidence to prove it. For ISPs, hosting providers, cloud platforms, and large enterprises, this shift creates a problem. Many regulations expect visibility into abuse and malicious […] The post What Regulations and Compliance Requirements Can a Threat Intelligence Feed Like Guardian Intel Help With? appeared firs...| Cybersecurity Solutions | Email & Network Security
THE KNOWNSEC LEAK: Yet Another Leak of China’s Contractor-Driven Cyber-Espionage Ecosystem
Leaked Knownsec documents reveal China’s cyberespionage ecosystem. Analyze TargetDB, GhostX, and 404 Lab’s role in global reconnaissance and critical infrastructure targeting. The post THE KNOWNSEC LEAK: Yet Another Leak of China’s Contractor-Driven Cyber-Espionage Ecosystem appeared first on DomainTools Investigations | DTI.| DomainTools Investigations | DTI
Cybersecurity Reading List - Week of 2026-01-05 - DomainTools Investigations | DTI
Commentary followed by links to cybersecurity articles that caught our interest internally.| DomainTools Investigations | DTI
12 Months of Fighting Cybercrime & Defending Enterprises | The SentinelLABS 2025 Review
From ransomware repurposed for espionage to increased exploitation of cloud platforms, learn about the key trends from SentinelLABS research in 2025.| SentinelOne
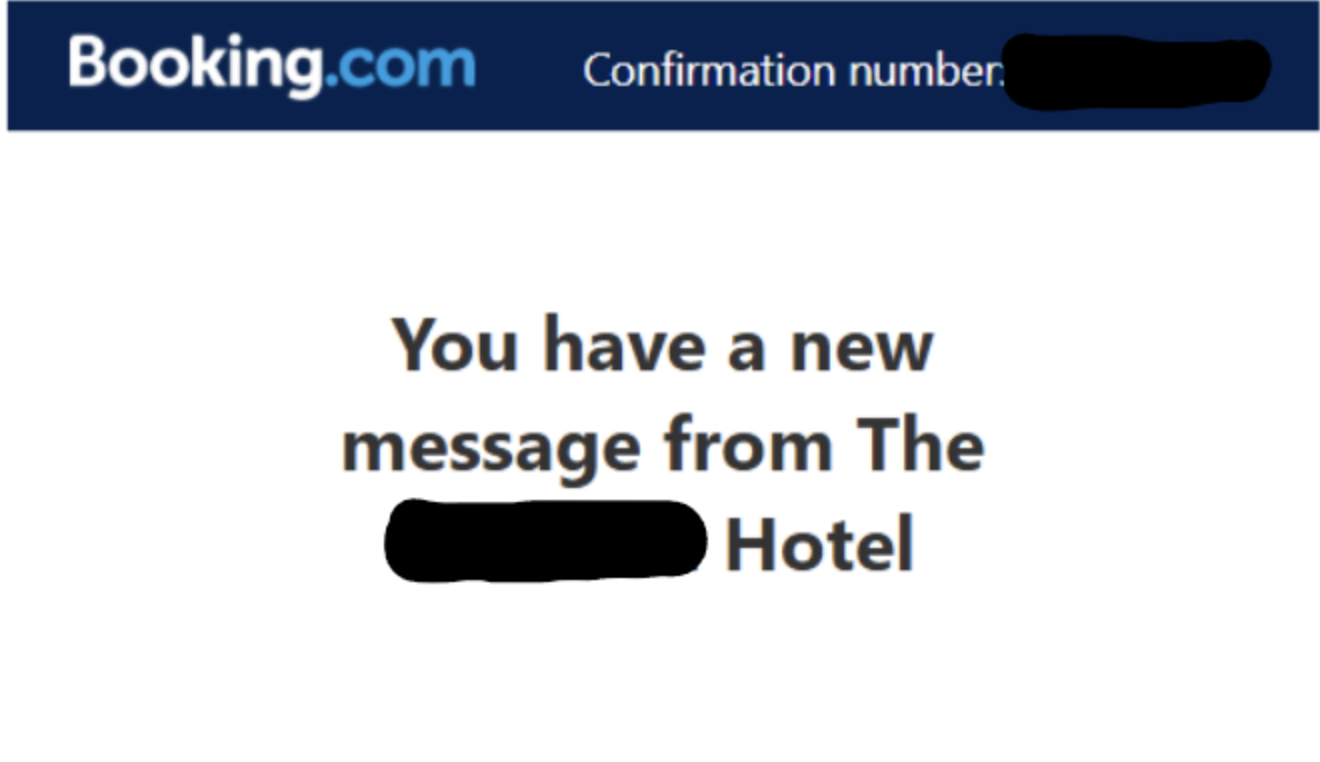
B2B2C Supply Chain Attack: Hotel’s Booking Accounts Compromised to Target Customers - DomainTools Investigations | DTI
New B2B2C supply chain attack targets Booking.com customers. Attackers are compromising hotel accounts to send "verify or cancel" phishing messages with dynamic booking data. Learn how to spot these fake domains and protect your payment info.| DomainTools Investigations | DTI
VTPRACTITIONERS{ACRONIS}: Tracking FileFix, Shadow Vector, and SideWinder
Introduction | VirusTotal Blog
VTPRACTITIONERS{SEQRITE}: Tracking UNG0002, Silent Lynx and DragonClone
Introduction | VirusTotal Blog
Advanced Threat Hunting: Automating Large-Scale Operations with LLMs
Last week, we were fortunate enough to attend the fantastic LABScon conference, organized by the SentinelOne Labs team. While there, we presented a workshop titled 'Advanced Threat Hunting: Automating Large-Scale Operations with LLMs.' The main goal of this workshop was to show attendees how they could automate their research using the VirusTotal API and Gemini. Specifically, we demonstrated how to integrate the power of Google Colab to quickly and efficiently generate Jupyter notebooks using...| VirusTotal Blog
Supercharging Your Threat Hunts: Join VirusTotal at Labscon for a Workshop on Automation and LLMs
We are excited to announce that our colleague Joseliyo Sánchez, will be at Labscon to present our workshop: Advanced Threat Hunting: Automating Large-Scale Operations with LLMs. This workshop is a joint effort with SentinelOne and their researcher, Aleksandar Milenkoski. | VirusTotal Blog
Research that builds detections
Note: You can view the full content of the blog here.| VirusTotal Blog
Unlock Threat Intelligence for Free with the Guardian Intel Community API
Ever wish you could tap into world-class threat intelligence without negotiating contracts, jumping through hoops, or burning through budget? Well, now you can! We’re excited to introduce the Guardian Intel Community API — your free key to the same rich, real-time abuse data powering enterprise-grade security systems around the world. Wait… Free? Yep. Totally free. […] The post Unlock Threat Intelligence for Free with the Guardian Intel Community API appeared first on Cybersecurity So...| Cybersecurity Solutions | Email & Network Security
Why CGNAT Is a Cancer on the Internet
So, you’ve asked me to whitelist your CGNAT IPs. I’d love to hear your justification and where the benefit is here for me or our users? In my opinion CGNAT is the cancer of the ISP/telecoms industry. “But Steve – we’re running out of IPv4 addresses, so we need CGNAT to fill the gap […] The post Why CGNAT Is a Cancer on the Internet appeared first on Cybersecurity Solutions | Email & Network Security.| Cybersecurity Solutions | Email & Network Security
AI-orchestrated cyberattacks
Sophisticated attackers once struggled to scale. Now, experienced groups can scale by adding agents to their workforce, and inexperienced or under‑resourced groups can attempt large‑scale operations with AI support.| ThreatDown by Malwarebytes
Inside EDR-Freeze: How ThreatDown stops the attack before it spreads
EDR-Freeze exploits legitimate Windows functionality to suspend security software, and it works entirely in user-mode using native Windows components.| ThreatDown by Malwarebytes
The APT35 Dump Episode 4: Leaking The Backstage Pass To An Iranian Intelligence Operation
APT35/Charming Kitten's leaked documents expose the financial machinery behind state-sponsored hacking. Learn how bureaucracy, crypto micro-payments, and administrative ledgers sustain Iranian cyber operations and link them to Moses Staff. The post The APT35 Dump Episode 4: Leaking The Backstage Pass To An Iranian Intelligence Operation appeared first on DomainTools Investigations | DTI.| DomainTools Investigations | DTI
Chinese Malware Delivery Domains Part IV
Chinese Malware Delivery Domains Part IV uncovers 1,900+ new sites targeting Chinese-speaking users. Get a deep dive into infrastructure, TTPs, and AI-powered threat analysis. The post Chinese Malware Delivery Domains Part IV appeared first on DomainTools Investigations | DTI.| DomainTools Investigations | DTI
React2Shell and related RSC vulnerabilities threat brief: early exploitation activity and threat actor techniques
Early activity indicates that threat actors quickly integrated this vulnerability into their scanning and reconnaissance routines and targeted critical infrastructure including nuclear fuel, uranium and rare earth elements. We outline the tactics they appear to be using and how Cloudflare is protecting customers.| The Cloudflare Blog
China-nexus cyber threat groups rapidly exploit React2Shell vulnerability (CVE-2025-55182) | AWS Security Blog
December 29, 2025: The blog post was updated to add options for AWS Network Firewall. December 12, 2025: The blog post was updated to clarify when customers need to update their ReactJS version. Within hours of the public disclosure of CVE-2025-55182 (React2Shell) on December 3, 2025, Amazon threat intelligence teams observed active exploitation attempts by […]| Amazon Web Services
Cybersecurity 2026 | The Year Ahead in AI, Adversaries, and Global Change
Explore SentinelLABS' take on what 2026 may bring for cybersecurity, including emerging trends and actionable insights.| SentinelOne
How Ignoring the Dark Web Impacts an Organization
By continuously monitoring the dark web, security teams can uncover early indicators of compromise and gain visibility into potential threat exposure.| Searchlight Cyber
Investigating Shai-Hulud: Inside the NPM Supply Chain Worm | The Sequence
Learn how the Shai Hulud NPM worm spread through the software supply chain, stole credentials, and evolved into a persistent developer threat.| the-sequence.com
Best 5 Dark Web Intelligence Platforms – Hackread – Cybersecurity News, Data Breaches, Tech, AI, Crypto and More
Follow us on Bluesky, Twitter (X), Mastodon and Facebook at @Hackread| hackread.com
Cybersecurity Reading List - Week of 2025-11-24
Infosec, know thyself. It’s no surprise that I’m an advocate for deeply introspective paths. My autism positions me for rumination (and much overthinking), but also self-examination and self-evaluation in order to identify strengths to capitalize on and inefficiencies to drum out. In talks I give on autism in cybersecurity with my good friend and work […] The post Cybersecurity Reading List - Week of 2025-11-24 appeared first on DomainTools Investigations | DTI.| DomainTools Investigations | DTI
Threat Intelligence Report: APT35 Internal Leak of Hacking Campaigns Against Lebanon, Kuwait, Turkey, Saudi Arabia, Korea, and Domestic Iranian Targets
Unmasking APT35 (Charming Kitten). New report analyzes leaked internal documents, revealing their operational profile, Exchange attack chains (ProxyShell, EWS), and quota-driven compromise strategies. The post Threat Intelligence Report: APT35 Internal Leak of Hacking Campaigns Against Lebanon, Kuwait, Turkey, Saudi Arabia, Korea, and Domestic Iranian Targets appeared first on DomainTools Investigations | DTI.| DomainTools Investigations | DTI
CrashOne - A Starbucks Story - CVE-2025-24277
On a cold autumn day in Budapest in 2024, I met independent security researcher Gergely Kalman at a local Starbucks to swap ideas, dead ends, and updates on our research. Over coffee, we started talking about crash logs, and that’s when we stumbled onto something big.| The Sequence
The Top Cyber Threats Facing SMBs in 2025
Small and midsize businesses (SMBs) are under siege in 2025. Attackers know these organizations often run lean IT teams with limited budgets, making them prime “path of least resistance” targets.| The Sequence
Inside the Great Firewall Part 3: Geopolitical and Societal Ramifications - DomainTools Investigations | DTI
Part 3 analyzes the GFW as geopolitical infrastructure: economic protectionism, the export of cyber sovereignty norms, and the emergence of an authoritarian coalition (Russia, Iran).| DomainTools Investigations | DTI
Extending STIX: How Custom objects empower your intelligence work
Discover how EclecticIQ Platform 3.6 empowers analysts with Custom objects to capture, structure, and operationalize intelligence beyond STIX. Model data your way, streamline investigations, and stay ready for emerging threats.| blog.eclecticiq.com
The era of predictive threat intelligence is here
Cybersecurity has been stuck in reaction mode for too long. Detect, respond, patch, repeat. That cycle isn’t working anymore especially not when threat actors are moving faster, scaling wider, and using AI to outpace defenders.| blog.eclecticiq.com
Customer Spotlight: Insights from a threat intelligence veteran
Fighting ransomware isn’t about more data — it’s about smarter context. Veteran Jeremy Nichols reveals how to outpace threats with automation.| blog.eclecticiq.com
Three Lazarus RATs coming for your cheese – Fox-IT International blog
Authors: Yun Zheng Hu and Mick Koomen Introduction In the past few years, Fox-IT and NCC Group have conducted multiple incident response cases involving a Lazarus subgroup that specifically targets…| Fox-IT International blog
LazarOps: APT Tactics Targeting the Developers Supply Chain [PART 1]
LazarOps: APT Tactics Targeting the Developers Supply Chain [PART 1]| Security Joes
Perplexity is using stealth, undeclared crawlers to evade website no-crawl directives
Perplexity is repeatedly modifying their user agent and changing IPs and ASNs to hide their crawling activity, in direct conflict with explicit no-crawl preferences expressed by websites.| The Cloudflare Blog
How to install ThreatMapper in Kali Linux?
Before starting, let’s understand a few terms,what is CNAPP? CNAPP aka cloud Native Application Protection Platform is all-in one cloud-native software platform that simplifies DevSecops practices.This term CNAPP was orignally coined by Gartner in 2021 CNAPPs make it simpler to embed security into the application lifecycle while providing superior protection for cloud workloads and data. A few core features of CNAPP are:- No Vendor Locking, with multi cloud support TI(Threat Intelligence)in...| hugs4bugs
How to onboard your first Microsoft sentinel SIEM tool?
Before jump over the onboarding of Microsoft Sentinel, let’s understand what MS Sentinel is? Definition: Microsoft Sentinel is a cloud native SIEM(Security information and Event Management) and SOAR(Security orchestration,automation,and response) solution,which delivers intelligent security analytics and threat intelligence. Why do we use it? To act as blue teaming as defensive security against attack detection,threat visibility,proactive hunting and threat response. In this blog we’ll be...| hugs4bugs
SIEM And Threat Intelligence: Track Emerging Threats
Learn how SIEM enables real-time threat monitoring for swift identification and response to emerging cyber threats.| Govindhtech
Ransomware in March 2025 - ThreatDown by Malwarebytes
March 2025 saw a huge number of ransomware attacks, and the Pennsylvania State Education Association quietly notify over 500,000 current and former teachers that hackers infiltrated its networks last…| ThreatDown by Malwarebytes
Top 7 Threat Intelligence Platforms & Software in 2025
Threat intelligence platforms help analyze and share cyber threat data. Discover top TIPs , their features, use cases, and comparisons.| eSecurity Planet
Security's Achilles' Heel: Vulnerable Drivers on the Prowl
A notable trend in cyber threats nowadays is the exploitation of vulnerabilities in drivers through the Bring Your Own Vulnerable Driver...| Security Joes
New Attack Vector In The Cloud: Attackers caught exploiting Object Storage Services
Security Joes Incident Response team recently became aware of a set of relatively new CVEs that were released at the end of March 2023....| Security Joes
Process Mockingjay: Echoing RWX In Userland To Achieve Code Execution
Our research team is committed to continuously identifying potential security vulnerabilities and techniques that threat actors may...| Security Joes
Operation Ice Breaker Targets The Gam(bl)ing Industry Right Before It's Biggest Gathering
In September of last year, our Incident Response team was called to an incident that was identified as an attempt of social engineering...| Security Joes
Raspberry Robin Detected ITW Targeting Insurance & Financial Institutes In Europe
Recent attacks documented in previous months seem to be orchestrated by hacking groups using a framework called Raspberry Robin. This...| Security Joes
Dissecting PlugX To Extract Its Crown Jewels
PlugX is a malware family first spotted in 2008. It is a Remote Access Trojan that has been used by several threat actors and provides...| Security Joes
RH-ISAC | Silk Typhoon Targeting IT Supply Chain in Multiple Sectors - RH-ISAC
Microsoft Threat Intelligence has identified a shift in tactics for Silk Typhoon, a Chinese state-sponsored espionage group, to target remote management tools| RH-ISAC
Powering Phishing Protection with Real-Time Intelligence
Watch how zvelo enhances phishing protection solutions with real-time intelligence that helps block phishing attacks before harm occurs.| zvelo
Sandworm APT Targets Ukrainian Users with Trojanized Microsoft KMS Activation Tools in Cyber Espionage Campaigns
Sandworm APT targets Ukrainian users with Trojanized Microsoft KMS tools for cyber espionage, leveraging pirated software to exfiltrate sensitive data and compromise critical infrastructure.| blog.eclecticiq.com
Mission "Data Destruction": A Large-scale Data-Wiping Campaign Targeting Israel
Mission "Data Destruction": A Large-scale Data-Wiping Campaign Targeting Israel| Security Joes
What is Threat Intelligence (TI)? | CIP Blog
Threat intelligence plays a crucial role in cybersecurity decision-making. It involves identifying and gathering cybersecurity information.| CIP Blog
Inside a 90-Minute Attack: Defeating Black Basta Tactics | SlashNext
Discover how a groundbreaking AI solution neutralized a bold Black Basta-style cyberattack in under 90 minutes—the first AI solution in the industry.| SlashNext | Complete Generative AI Security for Email, Mobile, and Browser
Black Basta PowerShell script to establish a Cobalt Strike beacon
We analyze an example of how the Black Basta ransomware group uses PowerShell to prepare their attack| ThreatDown by Malwarebytes
ONNX Store: Phishing-as-a-Service Platform Targeting Financial Institution
EclecticIQ analysts discovered phishing campaigns targeting financial institutions driven by a Phishing-as-a-Service (PhaaS) platform called ONNX Store.| blog.eclecticiq.com
Modern Honeypot Network – Teil 2: Honeypot einrichten
Ist ja schön, dass wir im ersten Artikel "Modern Honeypot Network – Teil 1: Kommandozentrale auf DigitalOcean" eine Kommandozentrale eingerichtet haben, um unsere Honeypots zu kontrollieren. Aber wie bekommen wir es nun hin, dass hier auch wirklich Daten ankommen? Wir müssen dazu unseren ersten Honeypot einrichten bzw. unseren ersten "Sensor" installieren. Ich habe mich dafür […]| Tizian Kohler
Modern Honeypot Network – Teil 1: Kommandozentrale auf DigitalOcean
Letztens kam mir die Idee einen Honeypot aufzusetzen, um Daten über das Vorgehen von Hackern zu sammeln. Also habe ich mich damit beschäftigt und mir mit Modern Honeypot Network (MHN) ein passendes Framework gesucht. Da ich keinen lokalen Honeypot aufsetzen wollte, habe ich eine cloudbasierte Variante mit DigitalOcean realisiert. In diesem Beitrag beschreibe ich kurz […]| Tizian Kohler
Actionable Threat Intel (VI) - A day in a Threat Hunter's life ~ VirusTotal Blog
Kaspersky's CTI analysts recently released their Asian APT groups report, including details on behavior by different adversaries. Followin...| blog.virustotal.com
Operation FlightNight: Indian Government Entities and Energy Sector Targeted by Cyber Espionage Campaign
EclecticIQ analysts identified a threat actor that utilized information stealer HackBrowserData to target Indian government entities and energy sector.| blog.eclecticiq.com
MineMeld: threat intelligence automation – connect to STIX/TAXII service [5] – Scubarda
This post is the fifth of a series on Threat Intelligence Automation topic. Post 1: Architecture and Hardening of MineMeld Post 2: Foundation: write a custom prototype and SOC integration Post 3: E…| Scubarda
Poisonous MD5 - Wolves Among the Sheep
MD5 is known to be broken for more than a decade now. Practical attacks have been shown since 2006, and public collision generator tools are also available since that time. The dangers of the developed collision attacks were demonstrated by academia and white-hat hackers too, but in case of the Flame malware we’ve also seen malicious parties exploiting the weaknesses in the wild.| Silent Signal Techblog
Embracing Curated Threat Intelligence in Times of Cost-Cutting
Explore how curated threat intelligence offers a strategic, cost-effective solution in the face of cybersecurity budget cuts.| zvelo
Social Engineering Tactics in Ransomware Distribution
AI-fueled social engineering tactics are a potent initial infection vector for ransomware as well as a myriad of other cyber threats.| zvelo
Defense-in-Depth: A Layered Strategy for Modern Cybersecurity
This post explores Defense-in-Depth, a comprehensive strategy with a multi-layered approach to modern threat protection.| zvelo