Enterprise Phishing: How Attackers Abuse Trusted Microsoft & Google Platforms
ANY.RUN observes a growing trend of phishing kit infrastructure being hosted on legitimate cloud and CDN platforms, rather than on newly registered domains. These campaigns often target enterprise users specifically, creating a global threat to businesses. The shift creates serious visibility challenges for security teams, as trusted platforms and valid indicators shield malicious activity from detection. For a deeper dive, read on and see the breakdown of such cases, along ...| ANY.RUN's Cybersecurity Blog
Attackers Are Taking Over Real Email Threads to Deliver Phishing: New Enterprise Risk
Think you can trust every email that comes from a business partner? Unfortunately, that’s no longer guaranteed; attackers now slip into legitimate threads and send messages that look fully authentic. That’s exactly what happened in a new case uncovered by ANY.RUN researchers; a trust takeover inside a real executive discussion about a document awaiting final approval. By detonating the suspicious message, the investigation exposed the […] The post Attackers Are Taki...| ANY.RUN's Cybersecurity Blog
Fix Staff Shortage & Burnout in Your SOC with Better Threat Intelligence
In cybersecurity, humans occupy both ends of the vulnerability spectrum. They click what should never be clicked, reuse passwords like heirlooms, and generously donate credentials to phishing pages that look “kind of legit.” Yet the same species becomes the strongest link once you step inside a SOC. Cybersecurity professionals don’t fail because they are careless […] The post Fix Staff Shortage & Burnout in Your SOC with Better Threat Intelligence appeared first on ANY.RUN's Cyber...| ANY.RUN's Cybersecurity Blog
From Forgotten Tool to Powerful Pivot: Using JA3 to Expose Attackers’ Infrastructure
A growing skepticism around JA3 is evident, and quite understandable as well. Public lists are rarely updated, and initiatives like JA3-fingerprints have been effectively frozen since 2021, creating the impression that this is a “yesterday’s technology.” However, JA3 fingerprints have not disappeared. Sensors continue to collect them, they appear in reports and threat intelligence interfaces; it’s just that many teams treat them formally, as yet […] The post From Forgott...| ANY.RUN's Cybersecurity Blog
German Manufacturing Under Phishing Attacks: Tracking a Stealthy AsyncRAT Campaign
Manufacturing companies have quietly become one of the most hunted species in the modern threat landscape. Not because they are careless, but because they are operationally critical, geographically distributed, and often rely on complex IT and OT environments that attackers love to probe. Key Takeaways The Threat Landscape: Manufacturing Under Siege ANY.RUN‘s data, based on sandbox submissions […] The post German Manufacturing Under Phishing Attacks: Tracking a Stealthy AsyncRA...| ANY.RUN's Cybersecurity Blog
CastleLoader Malware Analysis: Full Execution Breakdown
Read full-cycle technical analysis of CastleLoader malware, covering its entire multi-stage execution by ANY.RUN.| ANY.RUN's Cybersecurity Blog
Tracing a Paper Werewolf campaign through AI-generated decoys and Excel XLLs
Learn about a new backdoor, novel XLL execution trick. AI-generated decoy documents, exploitation of a new WinRar CVE and more. The post Tracing a Paper Werewolf campaign through AI-generated decoys and Excel XLLs appeared first on Intezer.| Intezer
Real-Time Industry & Geo Threat Landscape in TI Lookup
Prioritize alerts, cut noise, and focus on attacks that matter. Get real-time industry and geo context for any threat or IOC with ANY.RUN.| ANY.RUN's Cybersecurity Blog
How We Caught Lazarus's IT Workers Scheme Live on Camera
See how Lazarus Group's IT workers scheme was exposed on a live camera using real-time monitoring inside ANY.RUN’s sandbox.| ANY.RUN's Cybersecurity Blog
Major Cyber Attacks in November 2025
See November’s top cyber attacks, from XWorm and JSGuLdr to new TI Report findings, and learn what SOC teams can use to improve detection.| ANY.RUN's Cybersecurity Blog
A Guide for SOCs and MSSPs: See Critical Incidents in Alert Overload
Learn how SOC analysts can avoid missing critical incidents during alert overload using threat intelligence and ANY.RUN’s TI Lookup for fast IOC analysis.| ANY.RUN's Cybersecurity Blog
Solve Alert Fatigue: Action Plan for CISOs
Get a practical action plan for CISOs to eliminate alert fatigue and refocus SOC teams with real-time visibility and automation from ANY.RUN.| ANY.RUN's Cybersecurity Blog
Major October 2025 Cyber Attacks Your SOC Can’t Ignore
October’s top threats revealed: Google phishing, Figma abuse, LockBit 5.0. Insights SOCs can act on in minutes.| ANY.RUN's Cybersecurity Blog
Live Malware Code Mutation: How AI Generates Evasive Malware
Live Malware Code Mutation: How AI Generates Evasive Malware - Malware Analysis - Information Security Newspaper | Hacking News| Information Security Newspaper | Hacking News
SpyNote Malware C2 Emulator - eln0ty
SpyNote is a sophisticated Android malware (aka SpyMax)| eln0ty
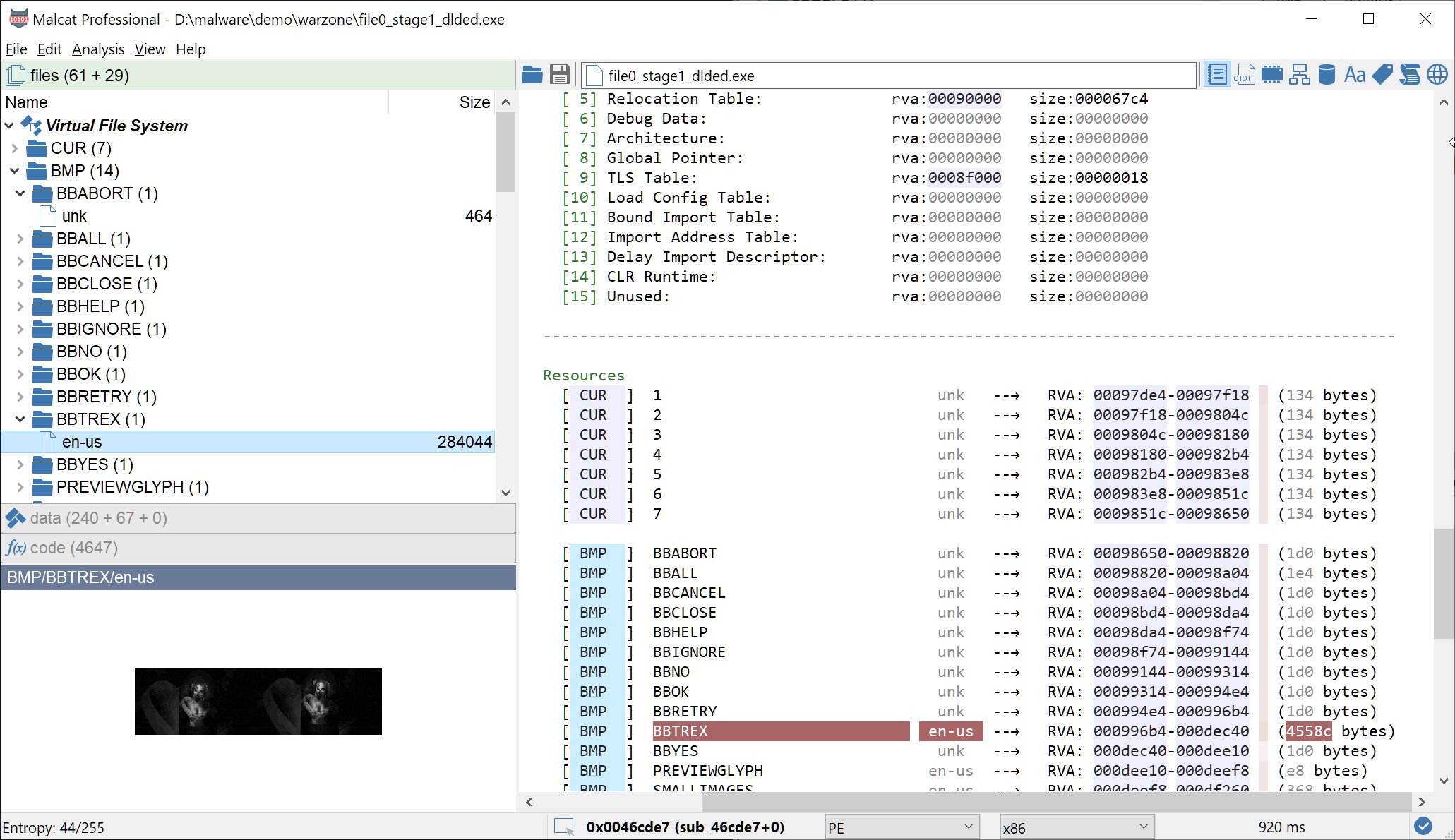
Malcat scripting tutorial: deobfuscating Latrodectus
In this tutorial, we will learn how to leverage Malcat's scripting and patching capabilities to deobfuscate an unpacked Latrodectus sample.| MALCAT
Major August 2025 Cyber Attacks Your SOC Can't Ignore
Explore how top attacks like Tycoon2FA, Rhadamanthys and Salty2FA unraveled in August 2025 and what insights SOC teams can take away.| ANY.RUN's Cybersecurity Blog
Get your swimsuit, we're diving into a black SEO scheme
What started like an easy unpacking session to fill a Friday afternoon lead us to a singular black-SEO campaign. Together, we will unravel 4 different malicious loaders written in 4 different programming languages, briefly analyse the final 10MB black-seo client and reverse engineer its command and control protocol. All of this for XXL swimsuits.| MALCAT
Salty 2FA: Undetected PhaaS from Storm-1575 Hitting US and EU Industries - ANY.RUN's Cybersecurity Blog
Dive deeper into malware analysis of a PhaaS framework discovered by ANY.RUN's experts: Salty2FA, targeting industries in the USA and EU.| ANY.RUN's Cybersecurity Blog
PyLangGhost RAT: Rising Stealer from Lazarus Group Striking Finance and Technology - ANY.RUN's Cybersecurity Blog
Discover analysis of PyLangGhost RAT, the newest Lazarus Group malware targeting finance and tech professionals.| ANY.RUN's Cybersecurity Blog
Major Cyber Attacks in July 2025 SOCs Cannot Ignore
Discover detailed breakdown of top cyberattacks in July 2025, from DeerStealer with LNK and LOLBin abuse to Remote Access Tools exploits.| ANY.RUN's Cybersecurity Blog
Backdooring ATMs via Bootloader? These Hackers Showed It’s Still Possible in 2025”
In a case that redefines the boundaries of modern cybercrime, a threat actor known as UNC2891 has carried out a multi-vector cyber-heist targeting ATM infrastructure across several banking institutions. Group-IB’sRead More → The post Backdooring ATMs via Bootloader? These Hackers Showed It’s Still Possible in 2025” appeared first on Information Security Newspaper | Hacking News.| Information Security Newspaper | Hacking News
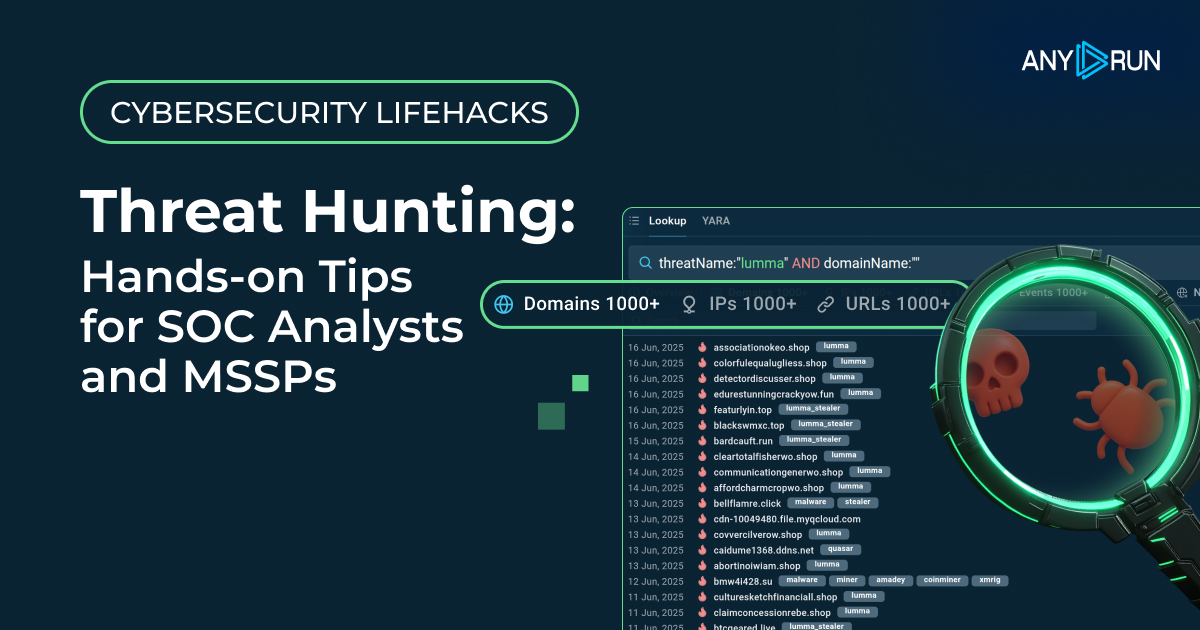
Threat Hunting: Hands-on Tips for SOC Analysts and MSSPs - ANY.RUN's Cybersecurity Blog
Learn actionable threat hunting techniques to proactively identify malware hidden inside your infrastructure and enrich your defense with fresh IOCs.| ANY.RUN's Cybersecurity Blog
PE32 Ransomware: A New Telegram-Based Threat on the Rise - ANY.RUN's Cybersecurity Blog
Read technical analysis of PE32, a new ransomware strain that demands ransom for both decryption and not leaking stolen data.| ANY.RUN's Cybersecurity Blog
LNK forensic and config extraction of a cobalt strike beacon
Windows shortcut files can contain valuable data. We will see how to extract the most information out of a .lnk downloader and will manually extract the configuration file of the final cobalt strike beacon using malcat| MALCAT
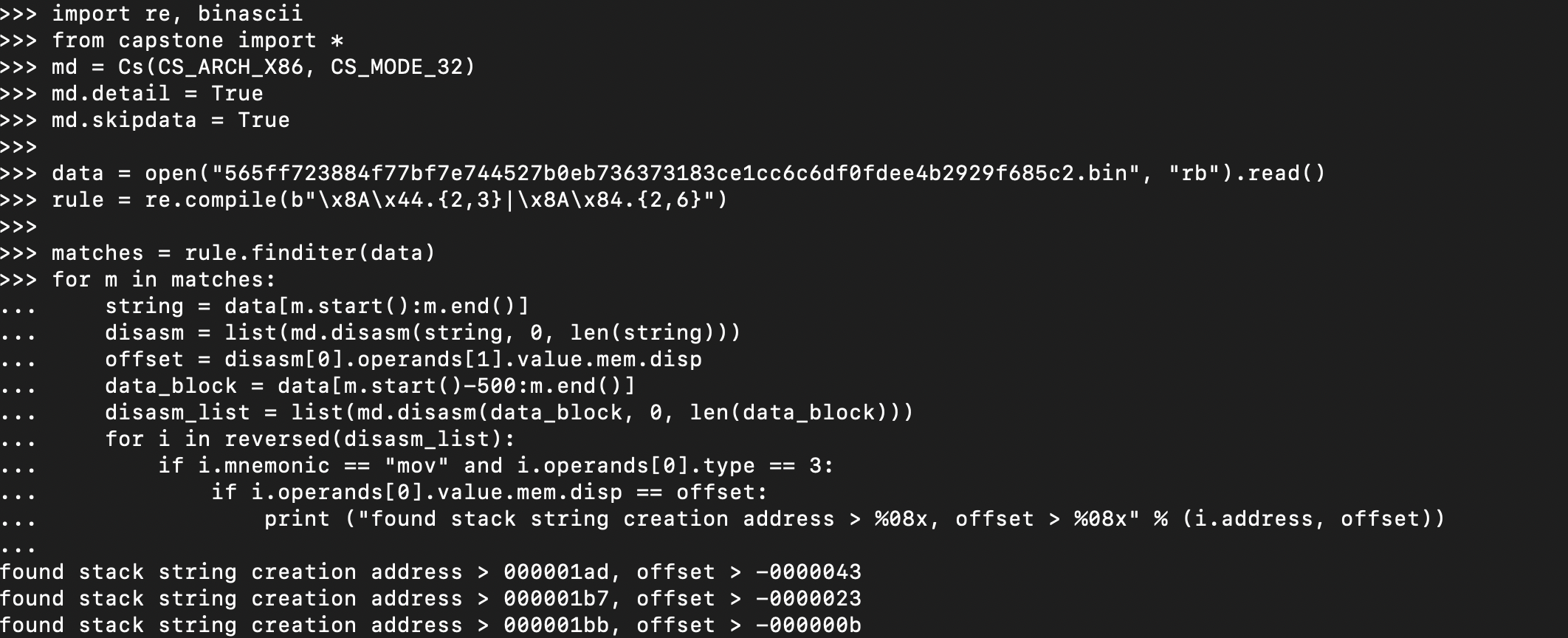
Identifying X-Refs with Capstone | 0ffset Training Solutions
In this post, I will explain how you can locate cross references programmatically using Python modules that are generally helpful in reverse engineering.| 0ffset Training Solutions | Practical and Affordable Cyber Security Training
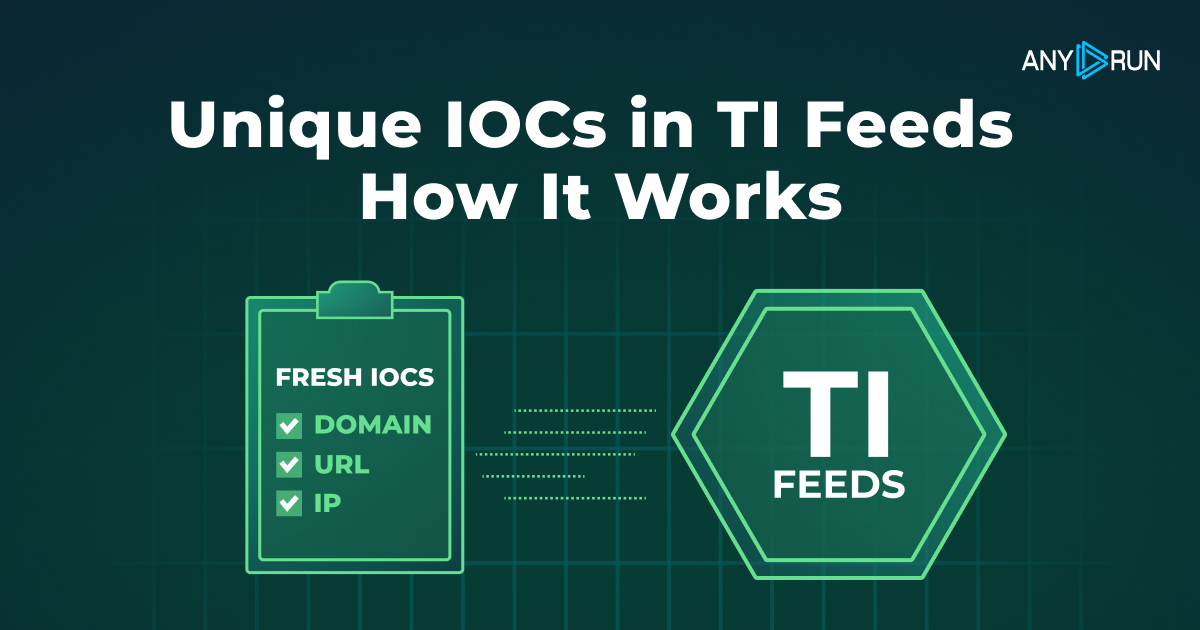
Enriching ANY.RUN's TI Feeds with Unique IOCs: How It Works - ANY.RUN's Cybersecurity Blog
See how ANY.RUN sources unique indicators of compromise for Threat Intelligence Feeds, helping businesses detect cyber threats.| ANY.RUN's Cybersecurity Blog
InvisibleFerret Malware: Technical Analysis - ANY.RUN's Cybersecurity Blog
Discover a detailed technical analysis of the InvisibleFerret malware that targets businesses across different industries.| ANY.RUN's Cybersecurity Blog
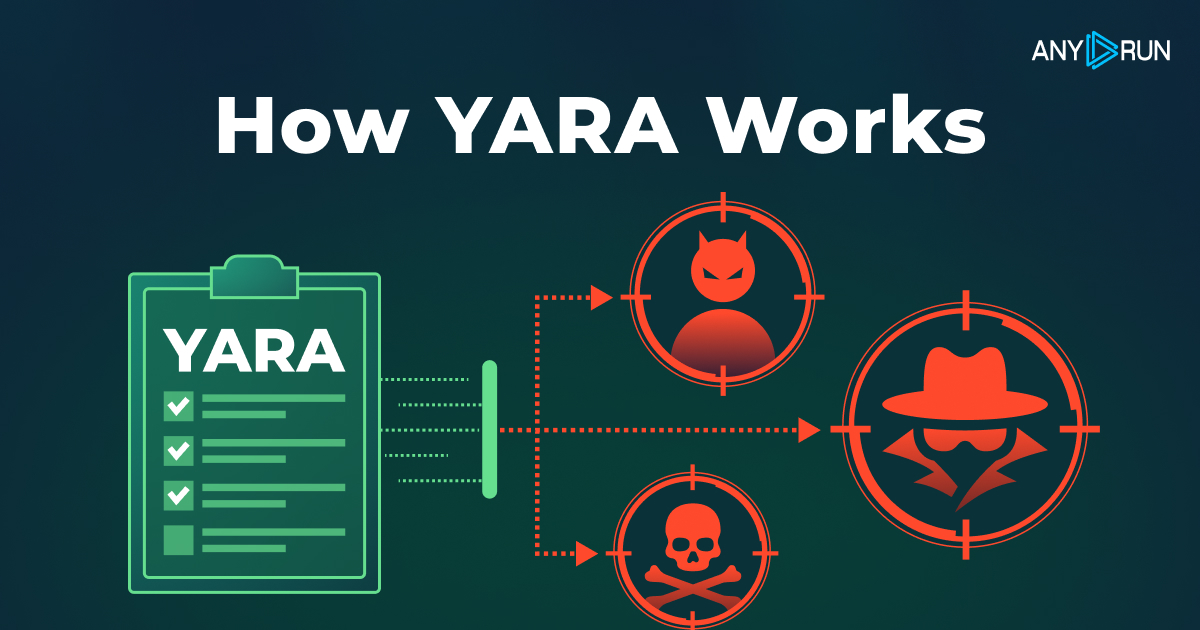
YARA Rules: Cyber Threat Detection Tool for Modern Cybersecurity - ANY.RUN's Cybersecurity Blog
Discover how YARA detection rules work and see real-world examples of rules used in ANY.RUN's Interactive Sandbox.| ANY.RUN's Cybersecurity Blog
IcedID gziploader analysis (Part1)
Introduction| eln0ty
HermeticWiper/FoxBlade Analysis (in-depth)
On February 23 during the war between Russia and Ukrainian, A malware which is targeting Ukrainian infrastructure (windows devices) by Russian Federation forces has since been observed in the neighboring countries of Latvia and Lithuania. HermeticWiper makes a system inoperable by corrupting its data by manipulating the MBR resulting in subsequent boot failure. Malware artifacts suggest that the attacks had been planned for several months.| eln0ty
Playing with AsyncRAT - eln0ty
AsyncRAT is a Remote Access Tool (RAT) designed to remotely monitor and control other computers| eln0ty
Examining Smokeloader’s Anti Hooking technique
Hooking is a technique to intercept function calls/messages or events passed between software, or in this case malware. The technique can be used for malicious, as well as defensive cases. Rootkits for example can hook API calls to make themselves invisible from analysis tools, while we as defenders can use hooking to gain more knowledge […]| Malware and Stuff
Unleashing the Viper : A Technical Analysis of WhiteSnake Stealer
Case Study WhiteSnake Stealer first appeared on hacking forums at the beginning of February 2022. The stealer collects data from various browsers such as Firefox, Chrome, Chromium, Edge, Brave, Vivaldi, CocCoc, and CentBrowser. Besides browsing data, it also collects data from Thunderbird, OBS-Studio, FileZilla, Snowflake-SSH, Steam, Signal, Telegram, Discord, Pidgin, Authy, WinAuth, Outlook, Foxmail, The Bat!, CoreFTP, WinSCP, AzireVPN, WindscribeVPN. The following are crypto wallets collect...| RussianPanda Research Blog
Writing a Qakbot 5.0 config extractor with Malcat
Starting from a (backdoored) MSI installer, we will unroll the infection to chain to get the final Qakbot sample. Sticking to pure static analysis, we will then decrypt Qakbot's configuration and finally write a script in Malcat to automate the process.| MALCAT
Reversing a NSIS dropper using quick and dirty shellcode emulation
We will statically unpack and emulate a malicious NSIS installer running multiple shellcodes, up to the final Lokibot password stealer and its configuration.| MALCAT
Cutting corners against a Dridex downloader
When one faces obfuscated code, it is sometimes more efficient to focus on the data instead. By using Malcat's different views and analyses (and a bit of guessing as well), we will show how to statically unpack an excel downloader and the following obfuscated native dropper without (much) reverse engineering.| MALCAT
Exploit, steganography and Delphi: unpacking DBatLoader
We will unroll a maldoc spam exploiting CVE-2018-0798 leading to a multi-staged Delphi dropper abusing steganography and cloud services to conceal its payload| MALCAT
Statically unpacking a simple .NET dropper
Our target is a 2-layers .NET dropper using multiple cipher passes (XOR, AES ECB and AES CBC + PBKDF2) to finally drop a Loki sample. Without even starting a debugger, we will show how to unpack it 100% statically using Malcat's builtin transformations and the python scripting engine.| MALCAT
The DLL Search Order And Hijacking It
If you ever used Process Monitor to track activity of a process, you might have encountered the following pattern: The image above is a snippet from events captured by Process Monitor during the execution of x32dbg.exe on Windows 7. DNSAPI.DLL and IPHLPPAPI.DLL are persisted in the System directory, so you might question yourself: Why would …The DLL Search Order And Hijacking It Read More »| Malware and Stuff
PEB: Where Magic Is Stored
As a reverse engineer, every now and then you encounter a situation where you dive deeper into the internal structures of an operating system as usual. Be it out of simple curiosity, or because you need to understand how a binary uses specific parts of the operating system in certain ways . One of the …PEB: Where Magic Is Stored Read More »| Malware and Stuff
DGAs – Generating domains dynamically
A domain generation algorithm is a routine/program that generates a domain dynamically. Think of the following example: An actor registers the domain evil.com. The corresponding backdoor has this domain hardcoded into its code. Once the attacker infects a target with this malware, it will start contacting its C2 server. As soon as a security company …DGAs – Generating domains dynamically Read More »| Malware and Stuff
Deobfuscating DanaBot’s API Hashing
You probably already guessed it from the title’s name, API Hashing is used to obfuscate a binary in order to hide API names from static analysis tools, hindering a reverse engineer to understand the malware’s functionality. A first approach to get an idea of an executable’s functionalities is to more or less dive through the …Deobfuscating DanaBot’s API Hashing Read More »| Malware and Stuff
Resolving Stack Strings with Emulation | 0ffset Training Solutions
It's not uncommon to come across some kind of string encryption functionality within malware samples, often more complex than a simple single-byte XOR operation which can often be brute-forced with simplicity. By encrypting strings, malware authors are able to potentially lower the detection rate by anti-malware software, obscuring strings that may be identified as "malicious",| 0ffset Training Solutions | Practical and Affordable Cyber Security Training
Analyzing SpyEye Malware for Fun
This is kind of a shot in the dark when it comes to content. As with most of my blog, this is mainly for my own tracking and edification but I hope to provide something adequate for others. This is a subject matter I’ve been trying to break into for a while but have been struggling for quite some time. It’s definitely out my realm of comfortability, but I’m hoping this blog will help with that.| anubissec.github.io
Python Opcode Obfuscation: A Powerful Anti-Analysis Technique
What if we could somehow compile some Python code that couldn’t be disassembled with your average Python interpreter? What if instead of LOAD_NAME or POP_TOP, we switched it’s opcode value with BUILD_LIST or PUSH_NULL?| 0ffset Training Solutions | Practical and Affordable Cyber Security Training
GuLoader's Obfuscation Technique: Understanding Stack Manipulation | 0ffset Training Solutions
Learn about GuLoader malware's stack manipulation technique for decrypting data blobs and how to implement it. A useful resource for those interested in reverse engineering shellcode or obfuscated malware.| 0ffset Training Solutions | Practical and Affordable Cyber Security Training
Deep Analysis of Anubis Banking Malware - n1ghtw0lf
Anubis is a well known android banking malware. Although it hasn’t been around for long, it had…| n1ghtw0lf
Deep Analysis of SmokeLoader - n1ghtw0lf
SmokeLoader is a well known bot that is been around since 2011. It’s mainly used to drop other malware families…| n1ghtw0lf
Deep Analysis of Snake Keylogger - XJunior
Snake Keylogger is a malware developed using .NET. It’s focused on stealing sensitive information from a victim’s device, including saved credentials, the victim’s keystrokes, screenshots of the victim’s screen, and clipboard data.| XJunior
Kraken - The Deep Sea Lurker Part 1 - Toxin Labs
Part 1 of analyzing the KrakenKeylogger Malware| Toxin Labs
Deep Analysis of GCleaner - n1ghtw0lf
GCleaner is a Pay-Per-Install (PPI) loader first discovered in early 2019, it has been used to deploy other malicious families like…| n1ghtw0lf
Deep Analysis of QBot Banking Trojan - n1ghtw0lf
Qbot is a modular information stealer also known as Qakbot. It has been active for years since 2007. It has…| n1ghtw0lf
LummaC2 - Stealer Features BreakDown - Toxin Labs
Breakdown of a key features stored in LummaC2 Stealer| Toxin Labs
BumbleBee DocuSign Campaign - Toxin Labs
Breakdown of a BumbleBee PowerShell Dropper & extracting the config of BumbleBee| Toxin Labs