Social Engineering 2.0
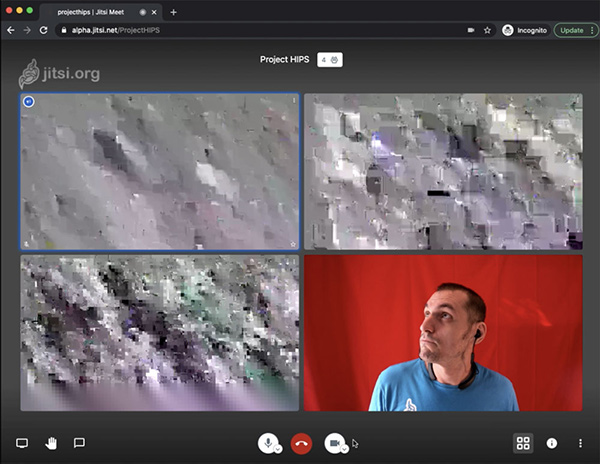
In early 2024, a Hong Kong-based clerk at multinational consulting engineering firm Arup was duped into transferring about $25 million to scammers who used AI to impersonate the company’s CFO, and other senior executives, in a live video meeting. The fraud only became apparent when the employee checked in with headquarters in London.| Communications of the ACM