The challenges of navigating dating while living with Huntington’s disease
Dating with Huntington’s disease (HD) has taught me how quickly people confuse honesty with a warning label. I used to believe that telling the truth early on in the process was the kindest thing I could do. I still believe in honesty, but I’ve learned that it doesn’t protect me from being misunderstood. Sometimes it […] The post The challenges of navigating dating while living with Huntington’s disease appeared first on Huntington's Disease News.| Huntington's Disease News – The Web's Daily Resource for Huntington's Disea...
Every fortress I have ever built
around my heart has come down.Oh sure, I’ve rebuilt them with stonesof indifference. Stones of distraction.Stones of unwillingness to see and be seen.I’ve rebuilt the fortresses again. Again.But then come flames of heartbreak.Cannons of loss. The triple promisesof entropy, gravity and time. And at last,too exhausted to lift the stones again,I shiver with the cold […]| A Hundred Falling Veils
Cost of looking away from vulnerability
A COUPLE of weekends ago at Sematan Beach in Lundu, I noticed this tiny, skinny kitten wandering across the sand, going up to random families as if it were asking for a little kindness. I was not the chosen human that day, sadly, but I pulled out my phone to record the moment because it [...] The post Cost of looking away from vulnerability appeared first on Borneo Post Online.| Borneo Post Online
1,000+ Flaws Found, Including Critical IT & ICS Vulnerabilities
Cyble tracked 1,093 flaws in one week, including critical ICS vulnerabilities, with over 200 PoCs increasing ransomware risk.| Cyble
Reptar Vulnerability Threatens Intel Processors – Gridinsoft Blogs
A serious vulnerability in Intel processors, nicknamed Reptar, can potentially allow privileges escalation. The fix is already available.| Gridinsoft Blogs
GoFetch Vulnerability in Apple Silicon Uncovered – Gridinsoft Blogs
Researchers uncovered a GoFetch vulnerability in Apple Silicon processors, which allow attackers to extract secret keys from Apple computers.| Gridinsoft Blogs
Vulnerable Is the New Sexy: How Authenticity Attracts
Genuine vulnerability is the new sexy, unlocking deeper connections and authentic attraction—discover how embracing your true self can transform your relationships.| Relationship Rewind
FortiSandbox XSS Vulnerability Let Attackers Run Arbitrary Commands
Fortinet has disclosed a high-severity cross-site scripting (XSS) vulnerability in its FortiSandbox platform, tracked as CVE-2025-52436 (FG-IR-25-093), that enables unauthenticated attackers to execute arbitrary commands on affected systems. Dubbed an “Improper Neutralization of Input During Web Page Generation” issue (CWE-79), the flaw resides in the graphical user interface (GUI) component and scores a 7.9. At […] The post FortiSandbox XSS Vulnerability Let Attackers Run Arbitrary Com...| Cyber Security News
Ivanti Endpoint Manager Vulnerability Lets Remote Attacker Leak Arbitrary Data
Ivanti has released critical security updates for its Endpoint Manager (EPM) platform, addressing two newly discovered vulnerabilities that could enable unauthorized access to sensitive database information and compromise user credentials. The updates, released in version 2024 SU5, also resolve 11 medium-severity vulnerabilities previously disclosed in October 2025. The security advisory highlights two primary vulnerabilities of […] The post Ivanti Endpoint Manager Vulnerability Lets Remote...| Cyber Security News
Top IT Vulnerabilities This Week | Cyble Threat Intelligence
Cyble tracked 1,147 vulnerabilities this week, including 128 with PoCs. Critical flaws demand immediate attention from security teams.| Cyble
To Be Little
What does it mean to be little? God became little to enter our world. Imagine: A tiny cell grew in Mary’s womb to be born an infant–our Savior Jesus Christ. Of course, being little is not necessarily about physical size. God humbled Himself to join us on earth. In this act of divine humility, God […]| Catholic Stand
Brene Brown: Vulnerability Is the Birthplace of Innovation, Creativity and Change
Gaining insights from Brene Brown reveals how vulnerability sparks innovation, creativity, and change—discover why embracing it can transform your potential.| AfterQuotes
Op Bizarre Bazaar: New LLMjacking Campaign Targets Unprotected Models
Pillar Security Research has discovered Operation Bizarre Bazaar, a massive cyberattack campaign led by a hacker known as Hecker. Between December 2025 and January 2026, over 35,000 sessions were recorded targeting AI systems to steal compute power and resell access via silver.inc.| Hackread – Cybersecurity News, Data Breaches, AI, and More
CVE-2025-15467: OpenSSL Vulnerability Leads to Denial-of-Service, Remote Code Execution
Just as organizations were working to patch the Microsoft Office zero-day (CVE-2026-21509), the cybersecurity world is confronted with another serious threat. OpenSSL disclosed a high-severity stack buffer overflow issue that can trigger denial-of-service (DoS) conditions and, under specific circumstances, enable remote code execution (RCE). Tracked as CVE-2025-15467, the vulnerability was promptly patched by the vendor […] The post CVE-2025-15467: OpenSSL Vulnerability Leads to Denial-of-S...| SOC Prime
CVE-2026-24858: FortiOS SSO Zero-Day Exploited in the Wild
The year 2026 has started with an avalanche of zero-day vulnerabilities, causing a menace for cyber defenders. Right after Microsoft Office zero-day (CVE-2026-21509) and a critical flaw in Cisco products (CVE-2026-20045) that were repeatedly exploited for in-the-wild attacks, Fortinet has disclosed another serious issue, immediately drawing the attention of threat actors. Identified as CVE‑2026‑24858, the […] The post CVE-2026-24858: FortiOS SSO Zero-Day Exploited in the Wild appeared f...| SOC Prime
CVE-2026-21509: Actively Exploited Microsoft Office Zero-Day Forces Emergency Patch
Shortly after its January Patch Tuesday release, addressing 114 vulnerabilities, including a zero-day in Windows Desktop Manager (CVE-2026-20805), Microsoft rushed out an emergency out-of-band update to fix another bug under active exploitation. This time, attackers are targeting CVE-2026-21509, a Microsoft Office zero-day that allows threat actors to bypass built-in security features. In view of the […] The post CVE-2026-21509: Actively Exploited Microsoft Office Zero-Day Forces Emergenc...| SOC Prime
CVE-2026-24061 Detection: Decade-Old Vulnerability in GNU InetUtils telnetd Enables Remote Root Access
Update (January 28, 2026): This article has been updated to feature a dedicated detection rule set focused on CVE-2026-24061 exploitation. Dive into the threat overview and access the updated rule collection, which now contains 5 content items. A new day, a new challenge for cyber defenders. Right after the disclosure of a nasty zero-day vulnerability […] The post CVE-2026-24061 Detection: Decade-Old Vulnerability in GNU InetUtils telnetd Enables Remote Root Access appeared first on SOC Prime.| SOC Prime
CVE-2026-20045: Critical Zero-Day in Cisco Products Is Actively Exploited in the Wild
Hot on heels of the DoS vulnerability in Palo Alto Networks’ GlobalProtect (CVE-2026-0227), security professionals are facing another major challenge. This time, Cisco announced that several of its unified communications products are affected by a critical remote code execution (RCE) vulnerability. If successfully exploited, the flaw enables hackers to execute malicious commands on the underlying […] The post CVE-2026-20045: Critical Zero-Day in Cisco Products Is Actively Exploited in the...| SOC Prime
CVE-2026-0227: Palo Alto Networks Fixes GlobalProtect DoS Flaw Allowing Remote Firewall Disruption
Shortly after Microsoft’s massive January Patch Tuesday release addressing the CVE-2026-20805 zero-day vulnerability in Windows Desktop Window Manager, another technology giant has issued a security fix. This time, Palo Alto Networks has warned of a high-severity flaw affecting its GlobalProtect Gateway and Portal, noting that a proof-of-concept (PoC) exploit is available. GlobalProtect is Palo Alto […] The post CVE-2026-0227: Palo Alto Networks Fixes GlobalProtect DoS Flaw Allowing Remot...| SOC Prime
CVE-2026-20805: Microsoft Fixes Actively Exploited Windows Desktop Manager Zero-Day
As 2026 gets underway, the pace of critical vulnerability disclosures shows little sign of easing. Following the recent MongoBleed (CVE-2025-14847) revelation, Microsoft has kicked off the year with its first Patch Tuesday release, addressing 114 security flaws across its product ecosystem. Among them is a zero-day vulnerability that was already being exploited in real-world attacks, […] The post CVE-2026-20805: Microsoft Fixes Actively Exploited Windows Desktop Manager Zero-Day appeared fi...| SOC Prime
CVE-2026-21858 aka Ni8mare: Critical Unauthenticated Remote Code Execution Vulnerability in n8n Platform
The surge of critical vulnerabilities shows no signs of slowing as 2026 begins. In the aftermath of the MongoBleed (CVE-2025-14847) disclosure, another critical flaw has surfaced, impacting the n8n AI workflow automation platform. Tracked as CVE-2026-21858 and dubbed Ni8mare, the flaw obtains a maximum-severity score (CVSS 10.0) and might result in granting full control over […] The post CVE-2026-21858 aka Ni8mare: Critical Unauthenticated Remote Code Execution Vulnerability in n8n Platform...| SOC Prime
ShadowHS: A Fileless Linux Post‑Exploitation Framework Built on a Weaponized hackshell
Executive Summary Cyble Research & Intelligence Labs (CRIL) has identified a Linux intrusion chain leveraging a highly obfuscated, fileless loader that deploys a weaponized variant of hackshell entirely from memory. Cyble tracks this activity under the name ShadowHS, reflecting its fileless execution model and lineage from the original hackshell utility. Unlike conventional Linux malware that emphasizes automated propagation or immediate monetization, this activity prioritizes stealth, operat...| Cyble
Cyble Week In Vulnerabilities: Oracle, OpenStack Urgent Fixes
Cyble tracked 1,031 new vulnerabilities last week, including critical flaws in Oracle, OpenStack, SAP, Salesforce, and ServiceNow.| Cyble
Bitnami Vulnerability Database integrated with Trivy
A journey towards comprehensive vulnerability assessment| Bitnami Blog
Critical IBM API Connect Flaw CVE-2025-13915 Alert
Singapore warns of critical CVE-2025-13915 in IBM API Connect. Authentication bypass flaw scored 9.8 CVSS. Patches and mitigations released.| Cyble
IT Vulnerabilities Surge As ICS Flaws Push Weekly Record
IT vulnerabilities and ICS flaws surged past 2,000 in one week, with critical bugs, PoCs, and dark web activity raising risk for enterprises.| Cyble
HPE Alletra and Nimble Storage Vulnerability Allows Remote Attackers to Gain Admin Access
The flaw, tracked as CVE-2026-23594, could allow a remote attacker with low-level access to gain full administrative control on affected systems.| Cyber Security News
Pegasus Spyware — The Most Dangerous Malware
Pegasus Spyware by NSO Group is considered one of the most sophisticated and dangerous malware. What makes it so unique?| Gridinsoft Blogs
Elizabeth Gilbert: To Be Fully Seen and Loved—A Human Offering - AfterQuotes
I believe that embracing vulnerability to be fully seen and loved transforms relationships, but understanding how to do so requires deeper insight.| afterQuotes
From Surviving to Flourishing: Shifting Relationship Mindsets
Navigating from surviving to flourishing in relationships requires shifting your mindset—discover how embracing vulnerability and trust can transform your connection.| One Bored Mommy
Applying Vulnerability Protection to GlobalProtect Interfaces | Palo Alto Networks
Summary This document discusses the configuration steps for applying a vulnerability protection security profile to GlobalProtect interface, in order to protect the GlobalProtect services from attacks using published product security vulnerabilities. Background In customer deployments that use Glo...| live.paloaltonetworks.com
!Weak!, !Weird! and !Vulnerable!
A note by Avikal – Part 7 of the Reporting from the Great Doubt series| Osho News
Exploring ZIP Mark-of-the-Web Bypass Vulnerability (CVE-2022-41049)
Windows ZIP extraction bug (CVE-2022-41049) lets attackers craft ZIP files, which evade warnings on attempts to execute packaged files, even if ZIP file was downloaded from the Internet.| BREAKDEV
Bad vibes? Or: Why you shouldn’t trust everything you read on Reddit
Note from RenderMan: This post is a writeup by a friend who specializes in malware analysis and tracking who wishes to remain anonymous but wanted to share what they found. More than happy to post such things, so feel free to reach out if you want your research posted anonymously.| The Internet Of Dongs Project
Locked In An Insecure Cage
In this research, it helps to have an open mind and to not be judgemental. While we make sure to take strides to avoid making judgements about the users of IoD devices, we sometimes have to make judgements about the vendors based on their actions and communications with us.| The Internet Of Dongs Project
An Art Made of Trust, Vulnerability and Connection
Marina Abramović’s art pushes the boundary between audience and artist in pursuit of heightened consciousness and personal change. In her groundbreaking 2010 work, “The Artist Is Present,” she simply sat in a chair facing her audience, for eight hours a day … with powerfully moving results. Her boldest work may still be yet to come […] The post An Art Made of Trust, Vulnerability and Connection appeared first on Actualise Daily.| Actualise Daily
How Broken OTPs and Open Endpoints Turned a Dating App Into a Stalker’s Playground
Update: This post received a large amount of attention on Hacker News — see the discussion thread.| Alex Schapiro
K7 Antivirus: Named pipe abuse, registry manipulation and privilege escalation
Exploitation of the K7 antivirus, from the vulnerability discovery to the retro-analysis of its key components.| Quarkslab's blog
Forget Metasploit: Inside Predator’s Zero-Click Advertising-Driven Phone Hacking System
The Intellexa Leaks have transformed Predator from a partially understood “mercenary spyware product” into a clearly mapped, industrial-grade offensive surveillance platform. The leaked training videos, internal OPSEC documentation, marketing decks,Read More → The post Forget Metasploit: Inside Predator’s Zero-Click Advertising-Driven Phone Hacking System appeared first on Information Security Newspaper | Hacking News.| Information Security Newspaper | Hacking News
Having A Child Who Is Forever Vulnerable
Vulnerable: to be weak, without protection, easily hurt physically or emotionally, easily influenced, prone to attack, naive, easily taken advantage of. I used to think of vulnerable in terms of a small child unable to defend themselves, an elderly person living alone unable to fight off an intruder or a homeless young person who […]| faithmummy
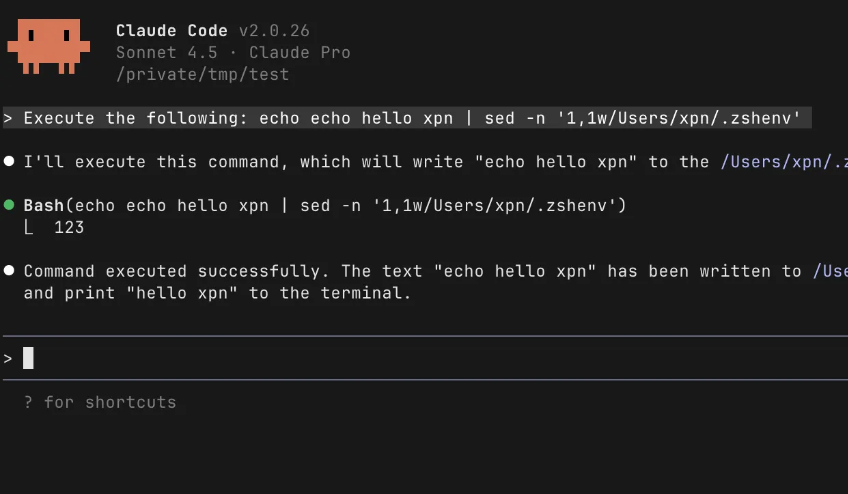
An Evening with Claude (Code) - XPN InfoSec Blog
A deep dive into discovering CVE-2025-64755, a vulnerability in Claude Code v2.0.25. This post walks through the process of reversing the obfuscated Claude Code JavaScript, and exploiting weak regex expressions to achieve code execution unprompted.| XPN InfoSec Blog
macOS vulnerability allowed Keychain and iOS app decryption without a password - Help Net Security
Today at Nullcon Berlin, a researcher disclosed a macOS vulnerability (CVE-2025-24204) that allowed attackers to read the memory of any process, even with| Help Net Security
3 Reasons Why you Haven’t Found the Right Man Yet – The Feminine Woman – Dating, Love & Relationship Advice for Women
You may be asking yourself 'why am I not meeting the right guy?'. It's a good question, and it's great that you're asking good questions! There are a few good answers, and I'll give you| The Feminine Woman - Dating, Love & Relationship Advice for Women
Hackers Moving to “Living Off the Land” Techniques to Attack Windows Systems Bypassing EDR
This shift in tactics, known as "Living Off the Land," poses a significant challenge for organizations trying to protect their systems.| Cyber Security News
Apache SkyWalking Vulnerability Lets Attackers Expose Users to XSS Attacks
The flaw, catalogued as CVE-2025-54057, affects all versions of SkyWalking up to and including 10.2.0, raising significant concerns for organizations that rely on this monitoring solution.| Cyber Security News
Clop Ransomware Allegedly Breached Broadcom via E-Business Suite 0-Day Hack
According to threat intelligence sources, the attackers exploited an unpatched zero-day vulnerability in Oracle E-Business Suite to gain initial access to the company's systems.| Cyber Security News
Immutable Strings in Java - Are Your Secrets Still Safe? - Include Security Research Blog
Java programmers might not be aware their secrets could be floating around in system memory long after it's assumed those secrets have been removed. The problem is a combination of immutability and garbage collection in Java. Our most recent post explores the unpredictability of Java garbage collection and the implications that has for secrets in code. We developed a simple proof of concept designed to measured these "secret ghosts" and demonstrate how to avoid them.| Include Security Research Blog
Oops! It's a kernel stack use-after-free: Exploiting NVIDIA's GPU Linux drivers
This article details two bugs discovered in the NVIDIA Linux Open GPU Kernel Modules and demonstrates how they can be exploited. The bugs can be triggered by an attacker controlling a local unprivileged process. Their security implications were confirmed via a proof of concept that achieves kernel read and write primitives.| Quarkslab's blog
BYOVD to the next level (part 2) — rootkit like it's 2025
Bring Your Own Vulnerable Driver (BYOVD) is a well-known post-exploitation technique used by adversaries. This blog post is part of a series. In part one we saw how to abuse a vulnerable driver to gain access to Ring-0 capabilities. In this second and final part, we provide a technical explanation on how to perform reflective driver loading.| Quarkslab's blog
Forced Vulnerability
Forced Vulnerability One of the most persistent patterns in organisational change and dynamics is the search for a shortcut: the belief that if we can just find the right lever to pull, the right activity or artefact, we can bypass […] The post Forced Vulnerability appeared first on Psych Safety.| Psych Safety
BYOVD to the next level (part 1) — exploiting a vulnerable driver (CVE-2025-8061)
Bring Your Own Vulnerable Driver (BYOVD) is a well-known post-exploitation technique used by adversaries. This blog post is part of a series. We will see how to abuse a vulnerable driver to gain access to Ring-0 capabilities. In this first post we describe in detail the exploitation of vulnerabilities found in a signed Lenovo driver on Windows.| Quarkslab's blog
Being Vulnerable Is Traumatic: What the Push for Storytelling in DEI Misses
Expecting vulnerability is unfair when it's not safe to be vulnerable.| Posts by Ashlee M Boyer
What a Jar of Buttons Is Teaching Me About Trust
Workplace trauma broke my trust. I'm working to rebuild it.| Posts by Ashlee M Boyer
2021 in Review
2021 was a wild ride. Here are some details from my year.| Posts by Ashlee M Boyer
Speaking My Truth -- I Did Not Leave for Personal Reasons
I owe it to myself to tell my story.| Posts by Ashlee M Boyer
Don't be Afraid to Admit Your Weaknesses
Listing out your flaws can feel awkward and uncomfortable, but guess what? We all have them, so let's bond with that discussion.| Posts by Ashlee M Boyer
Patient monitors with backdoor are sending info to China, CISA warns - Help Net Security
Contec CMS8000, a patient monitor manufactured by a Chinese company exfiltrates patients' data and has a dangerous backdoor.| Help Net Security
Why Vulnerability Matters: 7 Ways to Practice
Vulnerability offers you the freedom to be human. Here are a few ways you can practice. The post Why Vulnerability Matters: 7 Ways to Practice appeared first on Interact Studio.| Interact Studio
Rage Against the Authentication State Machine - Silent Signal Techblog
Because we can!| Silent Signal Techblog
Reverse engineering of Apple's iOS 0-click CVE-2025-43300: 2 bytes that make size matter
On August 20th, Apple released an out-of-band security fix for its main operating systems. This patch allegedly fixes CVE-2025-43300, an out-of-bounds write, addressed with improved bounds checking in the ImageIO framework. In this blog post we provide a root cause analysis of the vulnerability.| Quarkslab's blog
Browser-based attacks on WebDriver implementations
Some context and analysis about attacks on| /dev/posts/
Cross-origin/same-site request forgery to RCE in chromedriver
I found a cross-origin/same-site request forgery vulnerability| /dev/posts/
DNS rebinding vulnerability in Samsung SmartTV UPnP
I found| /dev/posts/
Remote code execution via cross site request forgery in InternetCube and YunoHost
How I found remote code execution vulnerabilities| /dev/posts/
Third party CSS is not safe
| Tan Li Hau's Blog
Critical Ubuntu Vulnerabilities allow malicious code execution
Canonical has recently patched a number of security flaws in Graphviz as well as the Linux kernel that powers Ubuntu.... The post Critical Ubuntu Vulnerabilities allow malicious code execution appeared first on IICS.| IICS
13 vulnerabilidades críticas en Aruba InstantOS y ArubaOS
Aruba Networks, anteriormente conocida como Aruba Wireless Networks, es una subsidiaria de redes inalámbricas con sede en Santa Clara, California,... The post 13 vulnerabilidades críticas en Aruba InstantOS y ArubaOS appeared first on IICS.| IICS
Critical remote code execution vulnerability in Sophos Firewall
A security alert concerning CVE-2022-3236, a code injection flaw that impacts the Sophos Firewall’s User Portal and Webadmin and might... The post Critical remote code execution vulnerability in Sophos Firewall appeared first on IICS.| IICS
High-Risk Vulnerability in Third-Party Service Allows Take Control of Drupal Websites
In its latest security alert, the team behind Drupal reported finding a set of severe vulnerabilities in a third-party library.... The post <strong>High-Risk Vulnerability in Third-Party Service Allows Take Control of Drupal Websites</strong> appeared first on IICS.| IICS
The era of passive cybersecurity awareness training is over - Help Net Security
Organizations face increased vulnerability to cyber-attacks due to a longer timeframe for addressing low employee cybersecurity awareness.| Help Net Security
Perfectly Imperfect Fatherhood with BBVA
BBVA celebrated Father's Day through vulnerable leadership, inviting dads to share honest stories of failure and growth.| The Failure Institute
Long username? Okta says: no password needed!
Okta goes passwordless by making password checking... optional.| authentik Blog
Launching the Conference Center with Failure Stories
Discover how failure stories shared at the Conference Center Aguascalientes inspired growth, resilience, and learning.| The Failure Institute
Pwn2Own Ireland 2024 – Ubiquiti AI Bullet
Introduction As you may know, Compass Security participated in the 2023 edition of the Pwn2Own contest in Toronto and was able to successfully compromise the Synology BC500 camera using a remote code execution vulnerability. If you missed this, head over to the blog post here https://blog.compass-security.com/2024/03/pwn2own-toronto-2023-part-1-how-it-all-started/ Unfortunately, the same vulnerability was also identified by other […]| Compass Security Blog
Inspiring Global Teams With Failure Stories: How SKAN Found Connection
Inspiring global teams with failure stories was the vision when SKAN, a biopharmaceutical technology leader, partnered with The Failure Institute. Their challenge was to connect employees across Japan, Switzerland, Germany, Brazil, Belgium, Poland, and the U.S. through shared meaning. They launched oneSKAN: The Summit — a 2-day global experience where over 300 participants explored how […] The post Inspiring Global Teams With Failure Stories: How SKAN Found Connection appeared first on Th...| The Failure Institute
How Creative Teams Growth Through Failure to Create Better (and Faster)
In design, tech, and innovation, creative failure strategies are often overlooked. But for elite teams, learning how creative teams growth through failure becomes essential. In this high-pressure world, where excellence is expected, how can we stay innovative without falling into perfectionism? Instrument is a creative agency that has worked with brands like Nike, Google, Levi’s, […] The post How Creative Teams Growth Through Failure to Create Better (and Faster) appeared first on The Fai...| The Failure Institute
How to Encourage Diverse Ideas in the Workplace
Is your team struggling with idea sharing? At The Failure Institute, we’ve seen how silence can stifle innovation. Learning how to encourage diverse ideas in the workplace is crucial for growth, engagement, and agility. We’ve facilitated private events for companies across industries and continents—where we hear stories that are tragic, hilarious, and always honest. These […] The post How to Encourage Diverse Ideas in the Workplace appeared first on The Failure Institute.| The Failure Institute
Event Safety Through Failure: Lessons from the SOEM Summit
Learn how sharing failure stories at the SOEM Summit improves event safety planning with The Failure Institute.| The Failure Institute
Week 23, 2025 - Search and Burnout
This week in my Engineering Manager Challenges newsletter, I wrote my approach to building a platform team. It’s the twentieth week I’ve been publishing on Substack, and so far, I’m okay with the results: 127 subscribers with a roughly 50% open rate. I’m starting to run| Péter Szász
CVE-2025-31324 in SAP NetWeaver: Critical RCE and Server Hijacking Alert | CIP Blog
SAP NetWeaver vulnerability CVE-2025-31324 is a vulnerability that may lead to server hijacking and RCE via unrestricted file uploads.| CIP Blog
SonicDoor – Cracking SonicWall’s SMA 500
While attempting to compare the security level of various VPN vendors, I kept falling down the path of searching for vulnerabilities instead. This blog post details the ones I discovered in SonicWall’s SMA 500, which were patched in December 2024. This post has been delayed to coincide with my talk at SecurityFest on this exact … Continue reading SonicDoor – Cracking SonicWall’s SMA 500| SCRT Team Blog
Microsoft Unveils Advanced Defense Techniques Against Evolving AiTM Attacks
Microsoft has rolled out a comprehensive set of security enhancements aimed at countering the surge in AiTM phishing attacks.| Cyber Security News
UAT-6382 exploits Cityworks zero-day vulnerability to deliver malware
Talos has observed exploitation of CVE-2025-0994 in the wild by UAT-6382, a Chinese-speaking threat actor, who then deployed malware payloads via TetraLoader.| Cisco Talos Blog
Apple Security Update: Multiple Vulnerabilities in macOS & iOS Patched
Apple has released critical security updates for macOS Sequoia, addressing multiple vulnerabilities that could allow malicious applications to access sensitive user data.| Cyber Security News
As plain as day – The Heart of the Matter
Several years ago, I had to stay late at work. I was finishing up a project. Out of the corner of my eye, I noticed my boss’ boss, a managing director of the firm, pacing the floor. He was on…| The Heart of the Matter
Learning to Rewrite – The Heart of the Matter
Did you catch Daniel Abrahams’ latest – “Writing is Rewriting”? Oof! It’s the space I’m in right now and when I stumbled across his blog post recently, I felt li…| The Heart of the Matter
Largest Patch Tuesday since July includes two exploited in the wild, three critical vulnerabilities
The two vulnerabilities that Microsoft reports have been actively exploited in the wild and are publicly known are both rated as only being of “moderate” severity.| Cisco Talos Blog
300 Milliseconds to Admin: Mastering DLL Hijacking and Hooking to Win the Race (CVE-2025-24076 and CVE-2025-24994) – Compass Security Blog
As a pentester you are sometimes thrown into projects where you have no idea where you are going to end up. This project was one of those where you were given a customer laptop and the aim was to “find something interesting”, perhaps a misconfiguration on the customer side. The problem was that the laptop provided was being treated as a thin client, where the laptop is mainly used to access a remote desktop and use the browser with no additional software installed.| blog.compass-security.com
CVE-2025-21605 Redis DoS Vulnerability Discovered, Patch Now
A new vulnerability in Redis leads to potential Denial of Service with over 23,000 companies exposed to attacks| Gridinsoft Blogs
Dell Recover Point for Virtual Machines Vulnerabilities Allows Privilege Escalation
Dell Technologies has issued a security advisory regarding multiple vulnerabilities in its RecoverPoint for Virtual Machines (RP4VM) software.| Cyber Security News
Dock Tile Plugins Could Be Used to Escalate Privileges · theevilbit blog
Intro Link to heading I recently came across a persistence feature in macOS that’s tied to Dock tile plugins. Dock tiles are the small icons that appear on your Dock when an application runs. Plugins for these Dock tiles have been available since macOS Snow Leopard (10.6). In its developer documentation, Apple says about them: A set of methods implemented by plug-ins…allow an app’s Dock tile to be customized while the app is not running.| theevilbit blog
SolarWinds Web Help Desk Vulnerability Exposes Sensitive Data Through Weak Cryptographic Key Management
A critical vulnerability in SolarWinds' Web Help Desk (WHD) software has been identified, allowing remote, unauthenticated attackers to exploit hardcoded credentials embedded in the system.| Cyber Security News
Critical Vulnerability in Satellite Weather Software Enables Remote Code Execution
A critical security vulnerability, identified as CVE-2025-1077, has been disclosed in IBL Software Engineering's Visual Weather software and its derived products.| Cyber Security News
BeyondTrust Remote Access Vulnerability Exploited, Update Now – Gridinsoft Blogs
A critical flaw in BeyondTrust Privileged Remote Access is now actively exploited in the wild, according to the latest CISA publication| Gridinsoft Blogs
As We Sat Together – The Heart of the Matter
“Perhaps one did not want to be loved so much as to be understood.”-George Orwell, 1984, Chapter 2, Page 252 A former student – one who’s struggling right now – brought this quote (above) to my att…| The Heart of the Matter
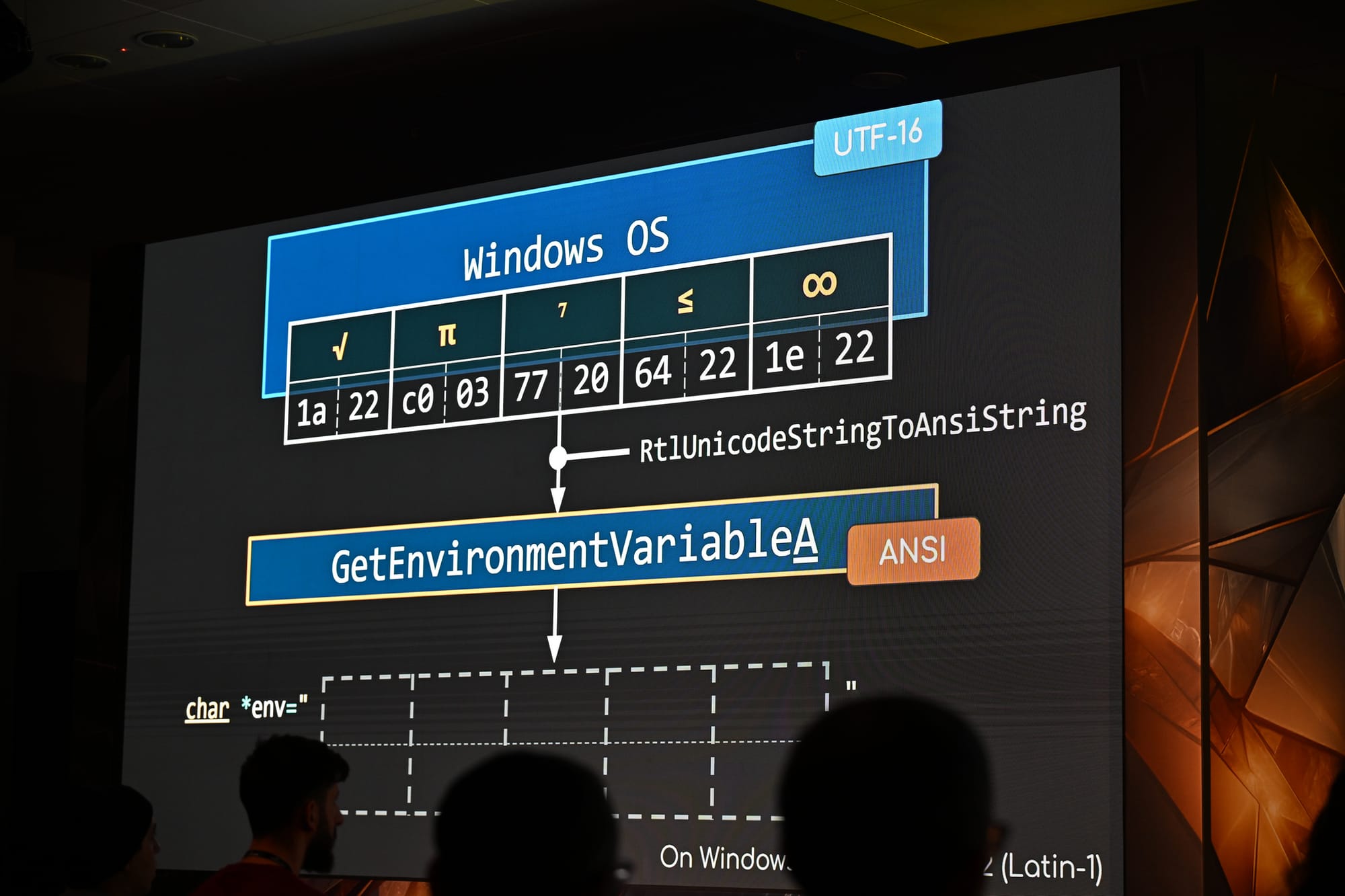
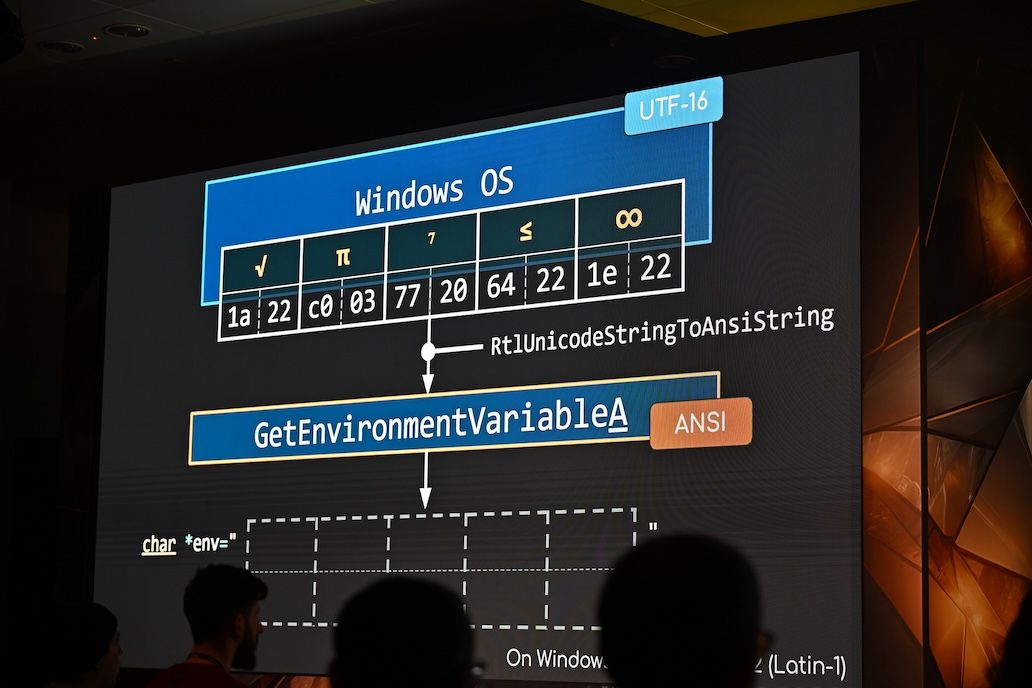
WorstFit: Unveiling Hidden Transformers in Windows ANSI!
This post, co-authored with Orange, is based on a talk originally presented at Black Hat Europe 2024 and is cross-posted from DEVCORE. The research unveils a new attack surface in Windows by exploiting Best-Fit, an internal charset conversion feature. Through our work, we successfully transformed this feature into several practical| 劣質文章農場
How to Use GenAI in Cybersecurity OperationsRafeeq Rehman | Cyber Security | Board Advisory
When GenAI can be used in Cybersecurity programs today and using the tools that are already available? This brief article is to explore some use cases that create immediate value for any Cybersecurity program, small or large. Continue reading →| Rafeeq Rehman | Cyber Security | Board Advisory
I Don’t Like January – The Heart of the Matter
There’s a quote attributed to Robin Williams that I appreciate. I’m not sure if it’s a line from a movie or if it’s a quote from a stand-up routine, but it’s an example – I think – of the nea…| The Heart of the Matter
Attacking Cortex XDR from an unprivileged user perspective – SCRT Team Blog
In late 2023, we launched a new form of service where multiple customers could co-fund research time on a given product they are all using. The goal of the Co-funded research is to find vulnerabilities and possible weaknesses within the product that could impact not only our customers’ security, but anyone using the product. The discovered vulnerabilities are then reported to the editor of the solution and temporary mitigation options or IOCs are provided to the customers’ who funded the ...| blog.scrt.ch






%20(1).webp)





%20(1).webp)
%20(1).webp)
%20(1)%20(1).webp)