Privileged File System Vulnerability Present in a SCADA System
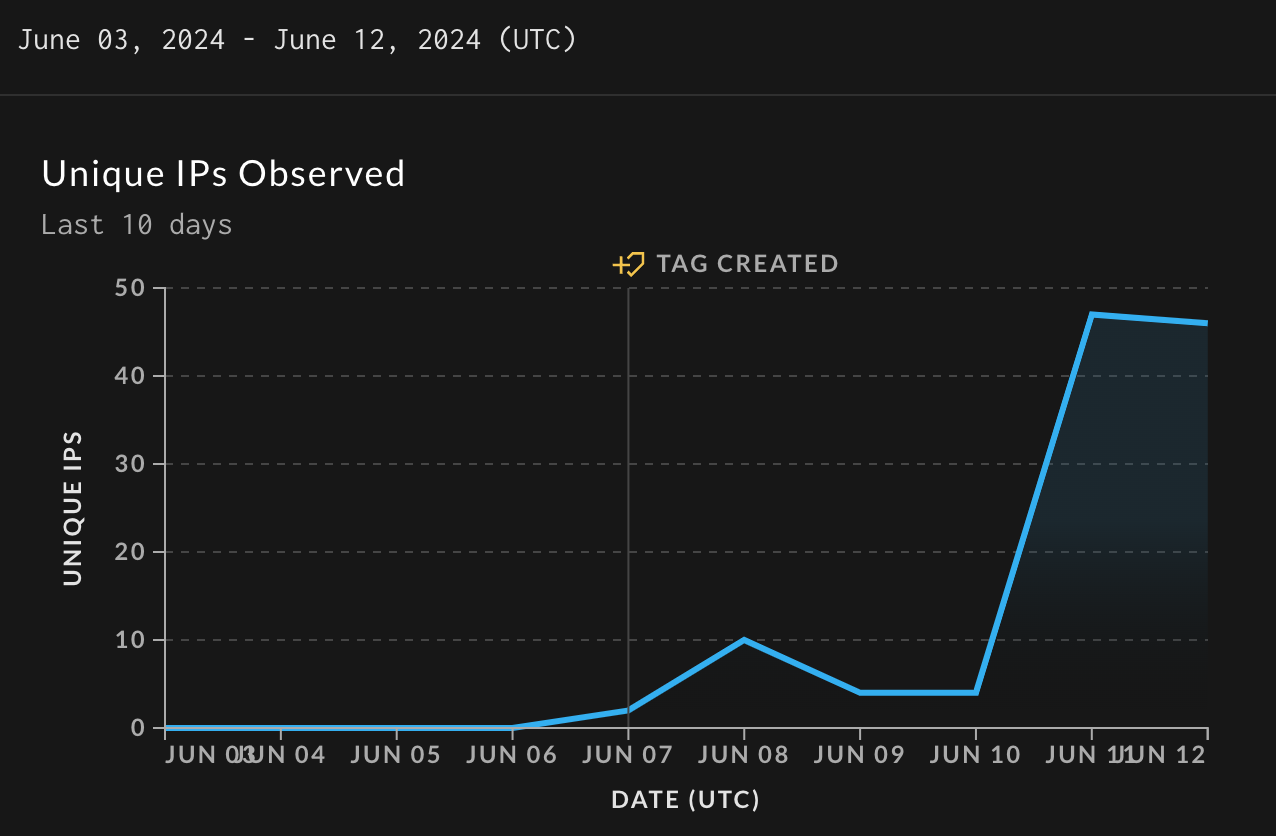
We detail our discovery of CVE-2025-0921. This privileged file system flaw in SCADA system Iconics Suite could lead to a denial-of-service (DoS) attack. The post Privileged File System Vulnerability Present in a SCADA System appeared first on Unit 42.| Unit 42
November 2025 Security Releases
Read November 2025 Security Releases| Express Blog
July 2025 Security Releases
Read July 2025 Security Releases| Express Blog
June 2025 Security Releases
Read June 2025 Security Releases| Express Blog
How Express.js Rebuilt Its Vulnerability Reporting Process
Read How Express.js Rebuilt Its Vulnerability Reporting Process| Express Blog
May 2025 Security Releases
Read May 2025 Security Releases| Express Blog
September 2024 Security Releases
Read September 2024 Security Releases| Express Blog
CVE-2025-40551
SolarWinds Web Help Desk Deserialization Vulnerability | Active Exploitation| Horizon3.ai
Cybercriminals hijack AI hosting service to compromise users
Bitdefender researchers have uncovered an Android remote access trojan campaign that highlights how legitimate developer platforms can be repurposed as part of large-scale mobile malware operations, with attackers abusing Hugging [...]| Australian Cyber Security Magazine
How we mitigated a vulnerability in Cloudflare’s ACME validation logic
A vulnerability was recently identified in Cloudflare’s automation of certificate validation. Here we explain the vulnerability and outline the steps we’ve taken to mitigate it.| The Cloudflare Blog
Critical Vulnerability in AI Vibe Coding platform Base44 | Wiz Blog
New discovery underscores security implications of AI-powered development and the rise of Vibe Coding Platforms.| wiz.io
AIs Are Getting Better at Finding and Exploiting Security Vulnerabilities
From an Anthropic blog post: In a recent evaluation of AI models’ cyber capabilities, current Claude models can now succeed at multistage attacks on networks with dozens of hosts using only standard, open-source tools, instead of the custom tools needed by previous generations. This illustrates how barriers to the use of AI in relatively autonomous cyber workflows are rapidly coming down, and highlights the importance of security fundamentals like promptly patching known vulnerabilities. [...| Schneier on Security
AIs are Getting Better at Finding and Exploiting Internet Vulnerabilities
Really interesting blog post from Anthropic: In a recent evaluation of AI models’ cyber capabilities, current Claude models can now succeed at multistage attacks on networks with dozens of hosts using only standard, open-source tools, instead of the custom tools needed by previous generations. This illustrates how barriers to the use of AI in relatively autonomous cyber workflows are rapidly coming down, and highlights the importance of security fundamentals like promptly patching known vul...| Schneier on Security
Command injection in Apache bRPC heap profiler
The CyberArk Labs team have identified Apache bRPC users are exposed to a critical command injection flaw in the /pprof/heap endpoint (CVE‑2025‑60021, CVSS 9.8) that enables unauthenticated remote code execution [...]| Australian Cyber Security Magazine
Network Attacks Outpace Malware in Australia
Australian businesses are now facing significantly more network-based attacks than traditional malware, according to WatchGuard Technologies’ Q4 2025 Threat Landscape Report, highlighting a marked shift in the country’s cyber threat [...]| Australian Cyber Security Magazine
CVE-2026-24061
GNU InetUtils telnetd Authentication Bypass Vulnerability| Horizon3.ai
Threat Brief: MongoDB Vulnerability (CVE-2025-14847)
Database platform MongoDB disclosed CVE-2025-14847, called MongoBleed. This is an unauthenticated memory disclosure vulnerability with a CVSS score of 8.7. The post Threat Brief: MongoDB Vulnerability (CVE-2025-14847) appeared first on Unit 42.| Unit 42
Remote Code Execution With Modern AI/ML Formats and Libraries
We identified remote code execution vulnerabilities in open-source AI/ML libraries published by Apple, Salesforce and NVIDIA.| Unit 42
MongoBleed (CVE-2025-14847): A Critical MongoDB Memory Leak Vulnerability Hidden for 8 Years
Overview In late 2025, a high-severity memory information disclosure vulnerability that had been lurking in MongoDB for years was finally revealed. Dubbed MongoBleed, this flaw allows unauthenticated attackers to read uninitialized heap memory, potentially exposing sensitive information. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added this vulnerability to its Known Exploited Vulnerabilities (KEV) […]| ASEC
Latest email threats – from QR code deception to callback phishing
Over the last month, Barracuda threat analysts have investigated the following email threats targeting organisations and their employees: Tycoon phishing kit using QR codes built out of HTML tables Callback phishing through [...]| Australian Cyber Security Magazine
New WhatsApp Scam Hijacks Accounts Without Stealing Passwords
Security researchers at Avast have uncovered a new WhatsApp takeover scam that does not rely on stolen passwords, broken encryption or SIM-swapping. Instead, it tricks users into granting access to [...]| Australian Cyber Security Magazine
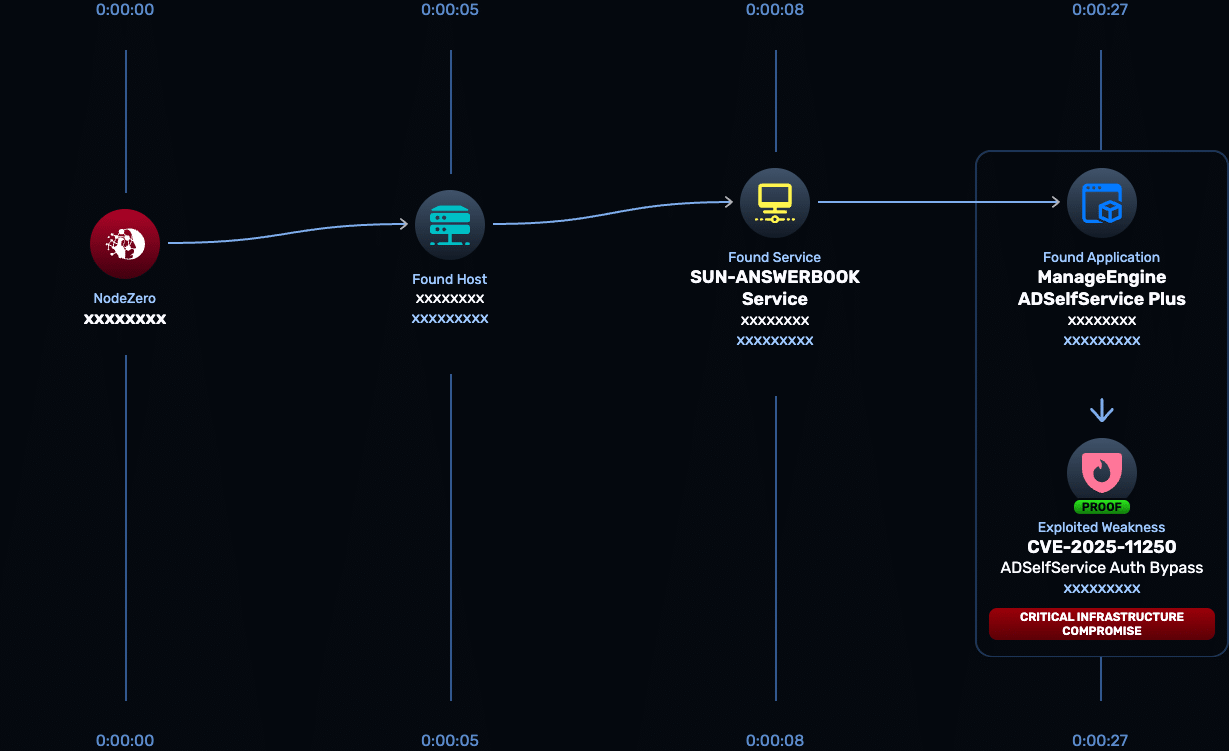
CVE-2025-11250: ManageEngine Auth Bypass | Horizon3.ai
Critical authentication bypass in ManageEngine ADSelfService Plus allows unauthenticated access. Learn impact, patch guidance, and how to verify exposure.| Horizon3.ai
React2Shell Vulnerability
React2Shell Remote Code Execution in React Server Components Vulnerability The bug dubbed as React2Shell, comprising two CVE’s, mainly CVE-2025-55182 and CVE-2025-66478, allows remote unauthenticated users to gain code execution on servers running vulnerable versions of React RSC or Next.JS App Router via single HTTP request. MITRE Tactic ID Technique Name Initial Access T1109 Exploit Public-Facing Application Execution T1059 Command and Scripting Interpreter Persistence T1505.003 Server So...| The Versa Networks Blog
React2Shell: Serious RCE Vulnerability Threatening the Latest Web Frameworks (CVE-2025-55182) - ASEC
React2Shell: Serious RCE Vulnerability Threatening the Latest Web Frameworks (CVE-2025-55182) ASEC| ASEC
SHA-3 Buffer Overflow (Part 2)
Following up on the SHA-3 buffer overflow in the “official” SHA-3 implementation, many people have been asking me how the vulnerability was found… As I explain in an upcoming paper at ACISP 2023, the vulnerability was found using the KLEE| Nicky Mouha
Buffer Overflow Attacks (Part 2)
This is the second post on buffer overflow attacks! Feel free to check out Buffer Overflow Attacks (Part 1) as well.| Nicky Mouha
React2Shell and related RSC vulnerabilities threat brief: early exploitation activity and threat actor techniques
Early activity indicates that threat actors quickly integrated this vulnerability into their scanning and reconnaissance routines and targeted critical infrastructure including nuclear fuel, uranium and rare earth elements. We outline the tactics they appear to be using and how Cloudflare is protecting customers.| The Cloudflare Blog
A vehicle’s head unit hacked via its modem | Securelist
Kaspersky researchers describe how they gained access to a vehicle's head unit by exploiting a single vulnerability in its modem.| Securelist
Exploitation of Critical Vulnerability in React Server Components (Updated December 12)
We discuss the CVSS 10.0-rated RCE vulnerability in the Flight protocol used by React Server Components. This is tracked as CVE-2025-55182.| Unit 42
Cloudflare WAF proactively protects against React vulnerability
Cloudflare offers protection against a new high profile vulnerability for React Server Components: CVE-2025-55182. All WAF customers are automatically protected as long as the WAF is deployed.| The Cloudflare Blog
You Thought It Was Over? Authentication Coercion Keeps Evolving
A new type of authentication coercion attack exploits an obscure and rarely monitored remote procedure call (RPC) interface.| Unit 42
LANDFALL: New Commercial-Grade Android Spyware in Exploit Chain Targeting Samsung Devices
Commercial-grade LANDFALL spyware exploits CVE-2025-21042 in Samsung Android’s image processing library. The spyware was embedded in malicious DNG files.| Unit 42
This Hidden Comet/Atlas AI Browser Flaw That Hackers Are Exploiting
This Hidden Comet/Atlas AI Browser Flaw That Hackers Are Exploiting - Vulnerabilities - Information Security Newspaper | Hacking News| Information Security Newspaper | Hacking News
Schneier on LLM vulnerabilities, agentic AI, and “trusting trust”
Last month, I was having dinner with a group and someone at the table was excitedly sharing how they were using agentic AI to create and merge PRs for them, with some review but with a lot of trust and automation. I admitted that I could be comfortable with some limited uses for that, such … Continue reading Schneier on LLM vulnerabilities, agentic AI, and “trusting trust”→| Sutter’s Mill
Production Security, Not That Kind - Include Security Research Blog
The Include Security team takes a foray into the world of audio production equipment in our latest blog post. We look under the hood of a professional-grade audio mixer to explore its security profile, consider how its functionality could be leveraged by an attacker in a real world setting, and develop a proof-of-concept exploit to demonstrate quick n' easy privilege escalation.| Include Security Research Blog
Exploits Explained: ZIP embedding attack on Google Chrome extensions
Growtika / Unsplash Editor's note: In this installment of Exploits Explained, security researcher Malcolm Stagg recounts his discovery of CVE-2024-0333, a vulnerability in Google Chrome that could have been exploited to enable the installation of malicious extensions. Be sure to follow README on LinkedIn to keep up with future additions to this series.| ReadMe
Wiz Finds Critical Redis RCE Vulnerability: CVE‑2025‑49844 | Wiz Blog
A 13‑year Redis flaw (CVE‑2025‑49844) allows attackers to escape Lua sandbox and run code on hosts. See Wiz Research’s analysis and mitigations.| wiz.io
Threat Brief: Salesloft Drift Integration Used To Compromise Salesforce Instances
This Threat Brief discusses observations on a campaign leveraging Salesloft Drift integration to exfiltrate data via compromised OAuth credentials.| Unit 42
Is Your Condo Board Actually Safe Against Cyberattacks? - CPO Management
Is your condo corporation safe against cyberattacks? We look at common condo corporation vulnerabilities and cybersecurity solutions.| CPO Management
Zip Slip, Path Traversal Vulnerability during File Decompression - ASEC
Zip Slip, Path Traversal Vulnerability during File Decompression ASEC| ASEC
Wrench Attacks: How Old Tactics Still Threaten Crypto Owners - BlackCloak | Protect Your Digital Life™
Crypto holders and high-profile individuals are targeted by criminals wielding blunt force and old-school tactics. Here's what you need to know.| BlackCloak | Protect Your Digital Life™
ThrottleStop driver abused to terminate AV processes | Securelist
In an incident response case, Kaspersky experts discovered new malware that terminates AV processes by abusing the legitimate ThrottleStop driver. Kaspersky solutions successfully counter and detect this threat.| securelist.com
How to Use Google’s OSS Rebuild: A New Open Source Software Supply Chain Security Tool
In a bold move to counter the growing number of open-source software supply chain attacks, Google has launched OSS Rebuild, a program designed to automatically rebuild OSS packages in isolatedRead More → The post How to Use Google’s OSS Rebuild: A New Open Source Software Supply Chain Security Tool appeared first on Information Security Newspaper | Hacking News.| Information Security Newspaper | Hacking News
Checking the Scope of CVE-2025-48927 – GreyNoise Labs
CVE-2025-48927 found in TeleMessage TM SGNL in May, and reported by KEV in July, allows attackers to trivially extract sensitive credentials via an unauthenticated, exposed /heapdump endpoint.| GreyNoise Labs
MCP 2025-06-18 Spec Update: Security, Structured Output & Elicitation
Real talk about MCP Spec update (v2025-06-18), including important changes, security implications and what developers should actually care about.| Forge Code Blog
CTEM Enhances Threat Prioritization in Complex Networks
Discover how CTEM enhances threat prioritization in complex networks and helps security teams focus on critical vulnerabilities.| Strobes Security
Misinterpreted: What Penetration Test Reports Actually Mean - Include Security Research Blog
This month's post discusses pentest reports and how the various audiences that consume them sometimes misinterpret what they mean. We cover why findings in a report are not a sign of failure, why "clean" reports aren't always good news, and why it may not be necessary to fix every single identified vulnerability. The post concludes with a few takeaways about how the information in a pentest report helps inform the reader about the report subject's security posture.| Include Security Research Blog
AyySSHush: Tradecraft of an emergent ASUS botnet – GreyNoise Labs
Using an AI powered network traffic analysis tool we built called SIFT, GreyNoise has caught multiple anomalous network payloads with zero-effort that are attempting to disable TrendMicro security features in ASUS routers, then exploit vulnerabilities and novel tradecraft in ASUS AiProtection features on those routers.| GreyNoise Labs
New FritzFrog Botnet Sample Exploits Log4Shell and PwnKit – Gridinsoft Blog
Analysts discovered a new FritzFrog malware sample that uses exploitation of Log4Shell and PwnKit flaws for self-propagation| Gridinsoft Blogs
CVE Program Almost Unfunded - Schneier on Security
Mitre’s CVE’s program—which provides common naming and other informational resources about cybersecurity vulnerabilities—was about to be cancelled, as the US Department of Homeland Security failed to renew the contact. It was funded for eleven more months at the last minute. This is a big deal. The CVE program is one of those pieces of common infrastructure that everyone benefits from. Losing it will bring us back to a world where there’s no single way to talk about vulnerabilities....| Schneier on Security
CVE-2025-1974: The IngressNightmare in Kubernetes | Wiz Blog
Wiz Research uncovered RCE vulnerabilities (CVE-2025-1097, 1098, 24514, 1974) in Ingress NGINX for Kubernetes allowing cluster-wide secret access.| wiz.io
Steps to TruRisk™ – 1: Shift to Priority-Driven Strategies | Qualys
Shift to a priority-driven cybersecurity strategy! Learn how risk-based vulnerability management helps focus on what truly matters, reducing cyber risk efficiently. #TruRisk #Cybersecurity| Qualys
Replacing a Space Heater Firmware Over WiFi - Include Security Research Blog
Our team hacks space heater firmware updates over wifi in the latest Include Security blog post. We break down, literally and figuratively, each step of the attack to demonstrate how anonymous users on the same wireless network as an affected space heater could overwrite its firmware causing it to behave in unpredictable and potentially dangerous ways!| Include Security Research Blog
Vulnerability Forecasting Technical Colloquium – A Few Thoughts – Rants of a deranged squirrel.
[I wrote this on September 21st, but apparently forgot to ultimately move from GDoc to Blog. I suspect because it really needs to be cleaned up as it is my first draft. Rather than do that, since t…| Rants of a deranged squirrel.
Threat Brief: Operation Lunar Peek, Activity Related to CVE-2024-0012 and CVE-2024-9474 (Updated Nov. 22)
We detail the observed limited activity regarding authentication bypass vulnerability CVE-2024-0012 affecting specific versions of PAN-OS software, and include protections and mitigations. We detail the observed limited activity regarding authentication bypass vulnerability CVE-2024-0012 affecting specific versions of PAN-OS software, and include protections and mitigations.| Unit 42
Exploiting AMD atdcm64a.sys arbitrary pointer dereference - Part 1 - hn security
After attending the OST2 – Exp4011 […]| hn security
Deceptive Delight: Jailbreak LLMs Through Camouflage and Distraction
We examine an LLM jailbreaking technique called "Deceptive Delight," a technique that mixes harmful topics with benign ones to trick AIs, with a high success rate. We examine an LLM jailbreaking technique called "Deceptive Delight," a technique that mixes harmful topics with benign ones to trick AIs, with a high success rate.| Unit 42
Unpatched Vulnerability in TI WooCommerce Wishlist Plugin | WPScan
A Few weeks ago an Sql Injection was discovered in the TI WooCommerce Wishlist plugin. After checking closer we found another entry point, affecting over 100,000 active installs. Despite the severi…| WPScan
Introducing: The Xamarin Security Scanner
The Xamarin Security Scanner finds well known security vulnerabilities by analyzing the source code of your Xamarin application.| Marcofolio.net
Unauthenticated Privilege Escalation in Profile-Builder plugin | WPScan
During a routine audit of various WordPress plugins, we identified some issues in Profile Builder and Profile Builder Pro (50k+ active installs). We discovered an Unauthenticated Privilege Escalati…| WPScan
10 of the Best Website Security Tools to Stay Ahead of Hackers | WPScan
Which website security tools are really necessary for your site? What to consider before investing in new software. 10 must-have tools you can’t skip.| WPScan
The 10 Best Vulnerability Scanners for Effective Web Security | WPScan
7 factors for choosing the best vulnerability scanner. Top options compared on features, pros, cons, & pricing. 5 things that make a great scanner| WPScan
Surge of JavaScript Malware in sites with vulnerable versions of LiteSpeed Cache Plugin | WPScan
If you’ve recently encountered the admin user wpsupp-user on your website, it means it’s being affected by this wave of infections. Identifying Contamination Signs: The malware typicall…| WPScan
New Malware Campaign Targets WP-Automatic Plugin | WPScan
A few weeks ago a critical vulnerability was discovered in the plugin WP-Automatic. This vulnerability, a SQL injection (SQLi) flaw, poses a severe threat as attackers can exploit it to gain unauth…| WPScan
What’s Going on With CVE-2024-4577 (Critical RCE in PHP)? – GreyNoise Labs
CVE-2024-4577 is a critical argument-injection vulnerability in PHP that affects Windows deployments and leads to a remote code execution.| GreyNoise Labs
Paycheck to Paycheck and Trapped in an MLM
Recently I received a message from Mary in Dallas, Texas: I found your blog, someone very close to me is trapped in an MLM - howdo I get her out? Please help. She is in SuperPatch Company and shetells everyone she makes millions, I know for a fact her and herhusband live pay check to| LaConte Consulting | Resilient Profit Strategies
Adaptive SLA for Vulnerability Management Guide- Strobes
Learn how an adaptive SLA for vulnerability management improves security by aligning remediation with risk, team maturity, and system criticality.| Strobes Security
Ransomware Attacks are on the Rise
Lockbit is by far this summer’s most prolific ransomware group, trailed by two offshoots of the Conti group.| Threatpost
Cybercriminals Are Selling Access to Chinese Surveillance Cameras
Tens of thousands of cameras have failed to patch a critical, 11-month-old CVE, leaving thousands of organizations exposed.| Threatpost
Firewall Bug Under Active Attack Triggers CISA Warning
CISA is warning that Palo Alto Networks’ PAN-OS is under active attack and needs to be patched ASAP.| Threatpost
iPhone Users Urged to Update to Patch 2 Zero-Days | Threatpost
Separate fixes to macOS and iOS patch respective flaws in the kernel and WebKit that can allow threat actors to take over devices and are under attack.| threatpost.com
Google Patches Chrome’s Fifth Zero-Day of the Year | Threatpost
An insufficient validation input flaw, one of 11 patched in an update this week, could allow for arbitrary code execution and is under active attack.| threatpost.com
Storage Vulnerabilities: The Neglected Cybersecurity Frontier | CIO Insight
Storage infrastructure presents cybersecurity vulnerabilities that are often overlooked. Learn more today.| CIO Insight
Buffer Overflow Attacks (Part 1)
This is my very first blog post! More will follow…| Nicky Mouha