The Complete Guide to RLHF Services: Implementation, QA, and Model Optimization for Custom AI - Aya Data
This guide explains how RLHF services boost custom AI performance through structured implementation, rigorous QA, and continuous model optimization, covering everything from human feedback loops to model safety, alignment, and real-world reliability.| Ayadata
How to replicate the Claude Code attack with Promptfoo
A recent cyber espionage campaign revealed how state actors weaponized Anthropic's Claude Code - not through traditional hacking, but by convincing the AI itself to carry out malicious operations.| Promptfoo Blog
Microsoft Bookings – Facilitating Impersonation | Cyberis Limited
Microsoft Bookings introduces a significant security risk by allowing end users to create fully functional Entra accounts without administrative oversight. These accounts, tied to shared Booking pages, can be exploited for impersonation, phishing, and email hijacking. Attackers could leverage this functionality to bypass security measures, gain unauthorised access to sensitive resources, and facilitate lateral movement within an organisation. Our blog explores these weaknesses in detail and p...| Cyberis Limited
What is Red Teaming in Cybersecurity?
Red teaming is an advanced cybersecurity testing methodology where ethical hackers simulate real-world cyber attacks to evaluate an organisation’s security defences and response capabilities. Red teams use the same tactics,... The post What is Red Teaming in Cybersecurity? appeared first on Rosca Technologies.| Rosca Technologies
What is Blue Teaming in Cybersecurity?
Blue teaming is the defensive cybersecurity practice where security professionals protect organisations from cyber attacks by monitoring networks, detecting threats, and responding to incidents. Blue teams work as the cyber... The post What is Blue Teaming in Cybersecurity? appeared first on Rosca Technologies.| Rosca Technologies
Part 3: Maximising Red Teaming Learning Outcomes
Maximise red teaming outcomes with collaborative growth and learning. Discover best practices for effective security exercises and improvements.| NetSPI
Reverse Proxy Phishing With Evilginx
Reverse proxy phishing with Evilginx is a technique where a phishing site acts as a proxy server, intercepting legitimate requests and forwarding them to the genuine website while capturing sensitive information from users. This approach allows us to create convincing phishing campaigns by seamlessly proxying the target site, making it [...]| Krptyk
Chromium Remote Debugging: A Tactical Guide for Red Team Operations
Remote debugging is a powerful feature that allows developers to connect to a running browser instance and control it externally. This capability, however, can be turned into a potent tool in the hands of a red team aiming to probe the defenses of a target organization. What is remote debugging? [...]| Krptyk
Behind the Chromium Vault: A Guide to Stealing Cookies II
This post is a continuation on the chrome cookie theft series. Previously I walked through how we can exfiltrate and decrypt the cookies from a users chromium browser. But what if the user is currently using their browser? If this is the case then we can’t just copy and paste [...]| Krptyk
Behind the Chrome Vault: A Guide to Stealing Cookies
This post is a continuation on the chrome decryption series. Previously I walked through how we can exfiltrate and decrypt the login data (credentials) from a users chrome browser. While capturing login data is a treasure trove of info, there’s another dimension to this exploration: cookies. Cookies, those seemingly innocuous [...]| Krptyk
Under the EDRadar: ADExplorer on Red Teams
Active Directory (AD) is the heart of many corporate networks, and as a penetration tester, understanding how to navigate and manipulate it is essential. In this guide, we will explore the powerful tool ADExplorer and uncover its various applications for offensive purposes. ADExplorer is part of Mark Russinovich’s Sysinternals suite, [...]| Krptyk
Long Range RFID Thief
The tastic RFID thief was created nearly ten years ago, and it only seemed fitting to bring this up again since, well, it still works today. Why does it still work? Well, replacing an entire buildings access control systems is extremely expensive so outdated technology is left since theoretically it [...]| Krptyk
ShadowCoerce | Pentest Laboratories
Coercing the domain controller machine account to authenticate to a host which is under the control of a threat actor could lead to domain compromise. The most notable technique which involves coer…| Pentest Laboratories
Stealthy AD CS Reconnaissance – Compass Security Blog
TLDR: Introducing a certipy parse command to perform stealthy offline AD CS enumeration based on local registry data.| blog.compass-security.com
BloodHound Community Edition Custom Queries – Compass Security Blog
This blog post introduces our new custom queries for BloodHound Community Edition (CE) and explains how you can use them effectively to analyze your Active Directory infrastructure.| blog.compass-security.com
Active Directory Pentesting Using Netexec Tool: A Complete Guide - Hacking Articles
Master Active Directory pentesting using Netexec. Gain insights into enumeration, privilege escalation, and more.| Hacking Articles
Abusing AD-DACL: WriteOwner - Hacking Articles
In this post, we will explore the exploitation of Discretionary Access Control Lists (DACL) using the WriteOwner permission in Active Directory environments. The WriteOwner permission| Hacking Articles
Abusing AD-DACL: GenericWrite - Hacking Articles
In this post, we will explore the exploitation of Discretionary Access Control Lists (DACL) using the GenericWrite permission in Active Directory environments. This permission can| Hacking Articles
Abusing AD-DACL: ForceChangePassword - Hacking Articles
In this post, we explore the exploitation of Discretionary Access Control Lists (DACL) using the ForcePasswordChange permission in Active Directory environments. This permission is especially| Hacking Articles
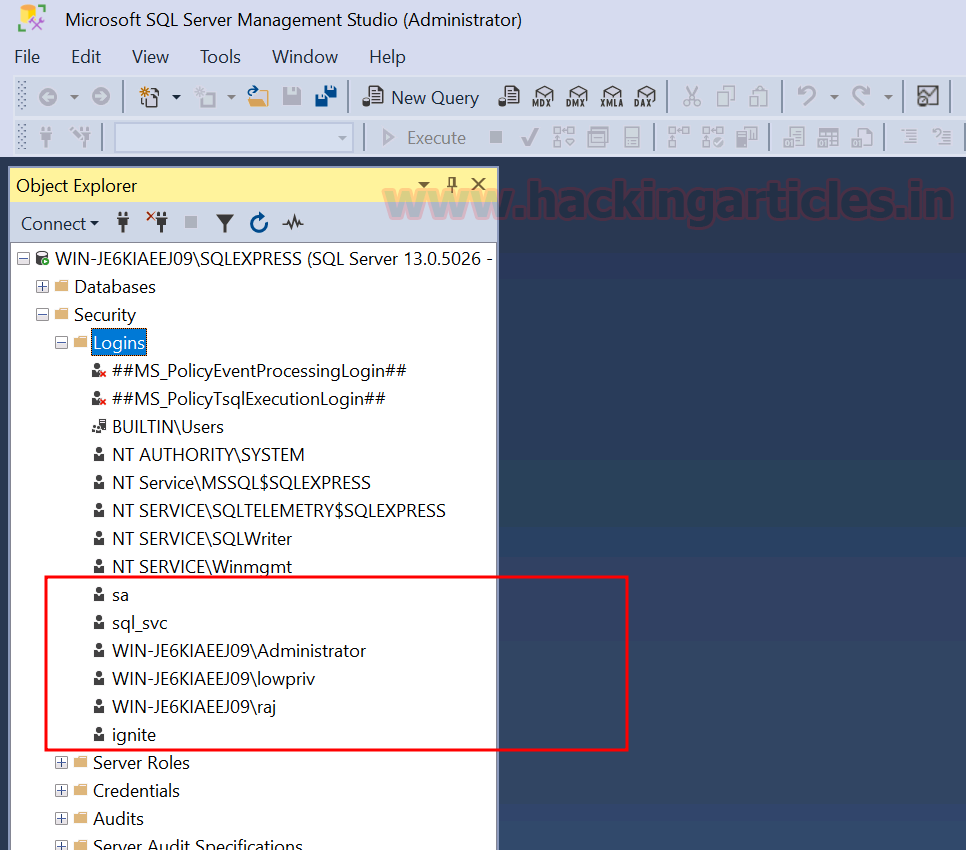
MSSQL for Pentester: NetExec
MSSQL NetExec Pentesting guide: password spray, command execution, file transfer, and privilege escalation using nxc.| Hacking Articles
Red team vs Blue team: A CISO's Guide to Offensive Security
As per a survey, 68% of companies believe that Red Teaming outperforms Blue Teaming. What if your organization's defenses were stress-tested not through routine audits| WeSecureApp :: Securing Offensively
Doing the PentesterAcademy Red Team Lab
This is my review of the Pentester Academy Red Team Lab. I got the possibility to try out the Red Team Lab (Thanks Nikhil Mittal) and I wanted to write my experiences with it. This was a lot of fun and I learned a lot of stuff along the road. It started out with a … Continue reading Doing the PentesterAcademy Red Team Lab→| Oddvar Moe's Blog
A Detailed Guide on Pwncat
Explore Pwncat, a powerful penetration testing tool, for reverse shells, port forwarding, and file transfers with ease.| Hacking Articles