Kubernetes may be coming to Apple's OS container project
Kubernetes on a MacBook? Could be sooner than you think...| The Stack
Modern Desktop Suite | Dank Linux
A modern Linux desktop suite with beautiful widgets and powerful monitoring - optimized for niri, Hyprland, MangoWC, Sway, and Miracle WM.| Dank Linux
Set Up WordPress Cron and Email Sending on Ubuntu 24.04
Chapter 5 of the complete guide to setting up Ubuntu 24.04 to run WordPress lightning fast. We configure WordPress cron, SSL certificate renewals and email sending.| SpinupWP
Simplify managing your Docker compose files with this handy tool - The New Stack
Dockge offers a web-based interface for managing Docker Compose files, making it easier to build and edit complex container stacks.| The New Stack
Back on team penguin
Post last updated 3 days, 6 hours ago| Home
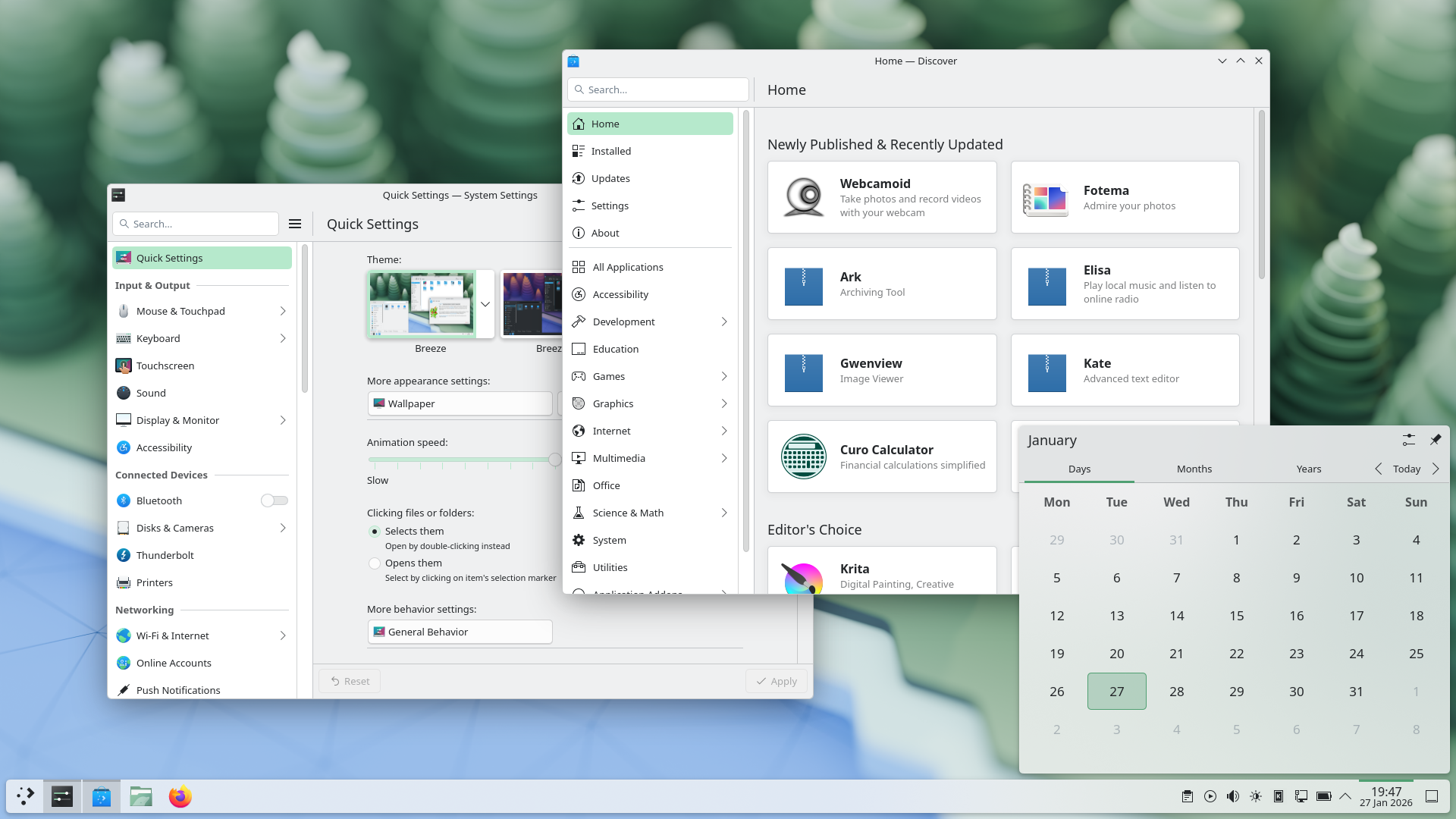
Plasma 6.6 - KDE Community
Plasma 6.6 is all about making your life as easy as possible without sacrificing any of the flexibility| kde.org
AsteroidOS 2.0 Released - AsteroidOS
AsteroidOS is an open-source operating system for smartwatches.| asteroidos.org
Virt-Manager
★★★½☆ - A front-end manager for Linux's built-in virtualization/emulation (QEMU and KVM, using libvirt). Much more customizable than Boxes, but missing a few convenience features.| Hyperborea: New Posts
Native Linux packages for rqlite
rqlite is a lightweight, open-source, distributed relational database built on SQLite and Raft. Starting with v9.4.1 rqlite now ships native Linux packages (.deb and .rpm) for easier installation and upgrades. Both amd64 and arm64 packages are available.| Vallified
ext4 | Internals for Interns
In the previous article , we explored FAT32—a filesystem that conquered the world through simplicity. Its linked-list approach (the FAT table) is easy to understand but has limitations: no journaling, linear directory search, and a 4GB file size limit. Let me introduce you to ext4, the filesystem running on millions of Linux machines right now. If you’re using Linux, there’s a good chance your files are stored on ext4. It’s been the default for most distributions for over a decade.| Internals for Interns
KRISÚ - Digitale Geiselhaft: Warum Windows in Europa eine tickende Zeitbombe ist
Wir leben in einer Ära der extremen Abhängigkeit. Während wir glauben, unsere Computer zu besitzen, sind wir in Wahrheit oft nur Mieter auf Gnaden von US-Giganten wie Microsoft, Google oder Adobe.| KRISÚ
HackerOS is what a Linux enthusiast’s OS should be
There are over 1,000 Linux distributions on the market. Throw a rock into the tech pond, and I guarantee that The post HackerOS is what a Linux enthusiast’s OS should be appeared first on The New Stack.| The New Stack | DevOps, Open Source, and Cloud Native News
Bluefin Linux: ChromeOS simplicity meets Linux power
Imagine you could use an operating system that’s as easy as ChromeOS, while also being as powerful as Linux. What The post Bluefin Linux: ChromeOS simplicity meets Linux power appeared first on The New Stack.| The New Stack | DevOps, Open Source, and Cloud Native News
The hunt for truly zero-CVE container images
Vendors chasing “zero-CVE” container images on top of traditional Linux distributions are running into structural limits in upstream release models. The post The hunt for truly zero-CVE container images appeared first on The New Stack.| The New Stack | DevOps, Open Source, and Cloud Native News
Building a FOSS live streaming camera
I have used a lot of cameras but never made one myself. Specifically one optimized for live streaming so it just outputs the camera feed over HDMI.| BrixIT Blog
Fdisk Command In Linux With Examples, Features & Advantages
In this blog, we cover everything about the fdisk command in Linux with examples, including what fdisk is, how it works, its role in the operating system, important features, advantages and disadvantages, types of partition schemes, common fdisk commands, interactive mode commands, real-world examples, fdisk vs other tools, and best practices for safe disk partitioning. […]| Online Tutorial Hub
Mkfs Command in Linux: Complete Guide With Examples, Types
Mkfs command in linux In essence, a new hard drive or partition is a “blank slate” comprising unprocessed magnetic or electrical sectors. The operating system requires a structure to keep track of the beginning and ending of files in order to store them. mkfs is the command that creates this structure. What is mkfs? mkfs […]| Online Tutorial Hub
Basic Disk Management Commands In Linux With Examples
Disk and Storage Management in Linux Disk and storage management in Linux refers to how the operating system detects, organizes, uses, and maintains storage devices such as hard disks, SSDs, USB drives, and virtual disks. It is one of the most important system administration skills because everything in Linux files, programs, users, logs depends on […]| Online Tutorial Hub
Kill Process Linux: Commands, Signals And Real Examples
Kill process linux Killing a process in Linux refers to signaling an active program to cease executing. Because programs can freeze, utilize excessive amounts of resources, or behave improperly, this is a crucial component of system administration. Linux enables you to manage or end just the problematic process rather than restarting the entire system. Killing […]| Online Tutorial Hub
Kubernetes Cluster Upgrade Using kubeadm
Complete kubernetes cluster upgrade guide using kubeadm, covering version compatibility, control plane updates, worker node upgrades, and zero downtime.| SysOpsTechnix
Avalue EMX-PTLP – A thin mini-ITX motherboard powered by up to an Intel Core Ultra 7 358H Panther Lake-H SoC
Avalue’s EMX-PTLP is an industrial, thin mini-ITX motherboard powered by Intel Panther Lake-H Core Ultra (Series 3) family, up to the 12-core Intel Core Ultra 7 358H SoC delivering up to 180 TOPS for AI and industrial automation deployments. The board supports up to 64GB of DDR5 SoDIMM/CSoDIMM memory, features M.2 PCIe 5.0 and PCIe 4.0 sockets for storage and expansion, M.2 E-Key and B-Key sockets for wireless and cellular connectivity, a PCIe x8 slot, HDMI, DisplayPort, USB-C, and LVDS/eDP...| CNX Software – Embedded Systems News
SlimeVR Butterfly Trackers – nRF52833-based, ultra-slim, full-body VR trackers offer up to 48h battery life (Crowdfunding)
Designed by SlimeVR in Rotterdam, Netherlands, the SlimeVR Butterfly Trackers are open-hardware, IMU-based, ultra-slim, full-body VR trackers designed for virtual reality gaming, motion capture, VTubing, and more. The trackers provide full-body positional tracking without base stations, cameras, Wi-Fi, or Bluetooth. Each tracker uses an IMU to measure absolute rotation and transmits data over a custom 2.4 GHz ESB protocol via a dedicated dongle supporting up to 10 trackers, eliminating occlus...| CNX Software – Embedded Systems News
de next-RAP8-EZBOX – An ultra-compact, fanless or actively-cooled Intel Core i7-1365UE Raptor Lake embedded system
AAEON’s de next-RAP8-EZBOX is an ultra-compact embedded system powered by an Intel Core i7-1365UE 10-core Raptor Lake SoC paired with 16GB of LPDDR5x system and one M.2 2280 M-Key slot for storage. It’s offered as either a 42.5mm thick fanless or a 45.4mm thick actively cooled mini PC. Key interfaces include HDMI 1.4b video output, two Ethernet (2.5GbE + GbE) ports, and two USB 3.0 ports. Its compact size, powerful processor, and range of interfaces make it suitable for space-constrained ...| CNX Software – Embedded Systems News
PiLink PL-R5/R5M Series – IP20/IP65 Industrial PCs powered by Raspberry Pi CM5
Made by Japan-based PiLink, the PL-R5 and PL-R5M Series are compact industrial PCs powered by a Raspberry Pi Compute Module 5 (CM5) and offered with either IP20 or IP65 ingress protection rating. The PL-R5 Series provides one USB 3.0 port, one Gigabit Ethernet port, and 9V to 40V DC input, while the PL-R5M Series offers one USB 2.0 port, one 100 Mbps Ethernet port, an optional extra Gigabit Ethernet port, and a 10.7V to 28.8V DC input range. Both include optional WiFi 5 and Bluetooth, an M.2 ...| CNX Software – Embedded Systems News
VU GPSDR – A low-cost GPS-disciplined SDR expansion board for the Vivid Unit RK3399 touchscreen SBC
UUGear’s VU GPSDR is a low-cost GPS-disciplined SDR expansion board designed specifically for the Vivid Unit, a palm-sized Rockchip RK3399-based touchscreen SBC we covered back in 2024. The VU GPSDR is built around the RTL2832U ADC and Rafael Micro R860 tuner, but what makes it different from SDRs like the PhaseLatch Mini and DeepRad SDR is the integration of a u-blox NEO-M8N GPS module. This module provides a GPS-disciplined 24 MHz clock reference to the Si5351 local oscillator, which e...| CNX Software – Embedded Systems News
PicoClaw ultra-lightweight personal AI Assistant runs on just 10MB of RAM
PicoClaw is an ultra-lightweight personal AI Assistant designed to work on less than 10 MB RAM and suitable for resource-constrained embedded boards such as the Sipeed LicheeRV Nano SBC going for around $15 and powered by a SOPHGO SG2002 RISC-V SoC with 256MB on-chip DDR3. I keep reading news about the OpenClaw personal AI assistant, after first finding out about it when the Cubie A7S SBC was launched. OpenClaw (previously ClawdBot) clears your inbox, sends emails, manages your calendar, and ...| CNX Software – Embedded Systems News
Beelink ME Pro 2-bay Intel N95/N150 NAS and mini PC supports 5GbE networking, up to 3x M.2 MVMe SSDs
Beelink ME Pro is a compact 2-bay hybrid NAS and Windows 11 mini PC built around Intel N95 (Alder Lake-N) or N150 (Twin Lake) SoC, and equipped with two 3.5-/2.5-inch SATA bays and three M.2 2280 NVMe slots for storage. It also features a “DIY drawer” design that lets users swap the motherboard for upgrades. The system also features up to 16 GB of LPDDR5 memory, 5 GbE and 2.5 GbE networking, Wi-Fi 6, Bluetooth 5.4, and various I/Os, including USB-C (10 Gbps), USB-A, HDMI 2.0, and a 3.5 mm...| CNX Software – Embedded Systems News
TOPST D3-G maker SBC is powered by Telechips TCT8050 “Dolphin3” Cortex-A72/A53/R5 automotive-grade SoC
TOPST D3-G is a single board computer (SBC) powered by a Telechips TCT8050 “Dolphin3/3M” 9-core automotive-grade SoC with four Cortex-A72 cores, four Cortex-A53 cores, and one real-time Cortex-R5 core. The board features 4GB or 8GB LPDDR4 RAM, 32GB eMMC flash and a microSD card for storage, a Gigabit Ethernet port, a DisplayPort 1.2 connector capable of driving four display through MST, two MIPI CSI connectors, a PCIe Gen3x 1 slot, a few USB ports, a 40-pin GPIO header compatible with Ras...| CNX Software – Embedded Systems News
Black Sesame Technologies Wudang C1200 “cross-domain” automotive SoCs feature up to 10x Cortex-A78AE cores
I found two interesting automotive SoCs in the Linux 6.19 changelog: Renesas R-Car X5H 16-/32-core Cortex-A720AE SoC and Black Sesame Technologies’ “Wudang” C1200 8-/10-core Cortex-A78AE processor family. While announced in 2024, there’s still no product page for the Renesas chip. So today, I’ll focus on the Wudang C1200 family. They are designed to be automotive-grade “cross-domain computing platforms” capable of handling multiple functions such as in-cabin sensing systems (e.g...| CNX Software – Embedded Systems News
Geniatech DB3506 is a full-featured Rockchip RK3506 development board and 3.5-inch industrial SBC
Geniatech DB3506 is a full-featured Rockchip RK3506 development board and 3.5-inch SBC designed for industrial control, human–machine interface (HMI) systems, IoT gateways, and other embedded applications. The board combines the tri-core Arm Cortex-A7 SoC with 256 MB to 1 GB LPDDR3 RAM and 256 MB or 512 MB NAND flash options, offers HDMI and RGB touchscreen display interfaces, dual Fast Ethernet, dual-band WiFi and Bluetooth 5.0, optional 4G LTE via a mini PCIe slot, two USB 2.0 p...| CNX Software – Embedded Systems News
86-type Smart Home control panel features a 3.5-inch display, physical buttons, Bluetooth SIG Mesh gateway
The Tuya WiFi 3.5-inch Smart Center Control Panel (CCP-S05) is designed to replace traditional 86-type switches while adding a Bluetooth SIG Mesh gateway, a touchscreen interface, and three buttons for smart homes, apartments, and small commercial spaces. Compared to other 86-type control panels such as the Luckfox-Pico-86-Panel, Dusun DSGW-130, and Waveshare’s ESP32-P4 Smart 86 Box, the Tuya device follows a hybrid approach, combining a capacitive touchscreen with three physical buttons fo...| CNX Software – Embedded Systems News
8devices Maca 2 – A ultra-long-range data radio with 80km range for drones and robotics
8devices Maca 2 high-power plug-and-play ultra-long-range wireless data radio targets drones, UAS, robotics, interceptor systems, industrial IoT, and defense-grade communications, where long range, resilience, and scalability are critical. The device features high transmit power of up to 39 dBm (with 36 dBm per RF chain) and a receiver sensitivity of –98 dBm, and is designed for air-to-ground and point-to-point connectivity over distances of up to 80 km. To maintain stable links over extrem...| CNX Software – Embedded Systems News
Windows Server: Mi ez és mikor van rá szüksége a vállalkozásodnak?
Mi az a Windows Server és mikor van rá szüksége a cégének? Útmutatónkból kiderül, hogyan segítheti a növekedést és mikor éri meg a szerverbérlés.| aWh
Terraform ate my minecraft server - a sad postmortem | WhyNot.Fail
Cause when you fail, somebody has to laugh at you| whynot.fail
C++17: Efficiently Returning std::vector from Functions
The discussion centers on returning std::vector from C++ functions, highlighting Return Value Optimization (RVO) introduced in C++17. RVO allows the compiler to avoid copying vectors by constructing them in place when there's a single return path. For multiple return paths, std::move is used to transfer ownership efficiently. Exceptions exist, particularly with the conditional operator, which requires copying. Returning references from member functions is safer than from free functions since ...| Tech For Talk
Step-by-Step Guide: Filezilla Setup for AWS EC2
Recently I have been involved in doing to some source code compilation on an AWS EC2 instance. However, after the compilation I encountered a problem.… Continue reading → Step-by-Step Guide: Filezilla Setup for AWS EC2| Tech For Talk
Resolving GobiSerial Module Errors on Raspberry Pi
Encountering 'Unknown Symbol' errors while loading the GobiSerial module on Raspberry Pi? This in-depth guide walks you through debugging missing kernel symbols, manually loading required modules, and properly configuring dependencies using depmod and modprobe for a clean and persistent fix. Learn how to resolve LTE driver issues with Sierra Wireless EM7565 on RPi effortlessly!| Tech For Talk
How to integrate a custom device driver into nuttx tree
I had written a blog on how to integrate a custom driver into Linux kernel tree previously here. Integrating a custom driver in nuttx kernel is pretty similar. But writing this down would probably be a good idea for any future reference.| Tech For Talk
How to create and run cppcheck executable from source code in linux machine (C++11 Static Analysis)
I do not have administrative rights on a linux server (openSuse Linux) I am working on right now. So installing anything is not an option… Continue reading → How to create and run cppcheck executable from source code in linux machine (C++11 Static Analysis)| Tech For Talk
How to detect memory leak in c program using valgrind?
valgrind is a popular tool which can detect memory in run-time. This blog post discusses how to install, and run valgrind at linux command line to detect memory leak in a sample C program.| Tech For Talk
CrossOver Linux: Run Windows Apps Smoothly on Linux Without Dual Boot
Switching to Linux raises one major question: What happens to your Windows applications? Many people who use Linux appreciate the operating system for its speed, stability, and the freedom it offers. But they still rely on some Windows software for their work or daily activities. In the past, the only choices were dual, booting or […]| CyberPanel
Timeshift Linux: Complete Guide to Backup, Restore, and System Snapshots
Only a single faulty update. Only a defective driver. Only an erroneous command. And that’s enough to bring down a Linux system that worked perfectly. Actually, if you have ever installed a package and, after that, your system did not boot, you already know how bad it can be. Besides, reinstalling Linux, getting everything ready […]| CyberPanel
CNC for Linux: Complete Guide to Linux for CNC Machines and Software Setup
CNC machines present only one demand at the highest level. Stability. If you are cutting metal, engraving wood, or doing precision manufacturing, even a small system delay can definitely spoil your work. That’s the main reason why experts are ditching Windows and going to CNC for Linux. Linux is mind your own business, and totally […]| CyberPanel
Linux Handheld: Complete Guide to Handheld Linux Computers and the Mecha Comet
The notion of carrying an entire Linux system in your pocket used to be quite a stretch. Linux was mostly associated with servers, desktops, or big, heavy laptops. But the situation has changed very quickly. Nowadays, a Linux handheld device can pack the power of a small PC in something you can literally hold in […]| CyberPanel
WinRAR for Linux: Download, Install, and Best Alternatives Explained
Many Windows users who move to Linux first look for WinRAR for Linux. It’s logical to think so. For years, WinRAR has been the default archiving tool on Windows. Users rely on it to open ZIP files, compress big folders, and handle backups. But this is where the trouble starts. When moving to Linux, you […]| CyberPanel
Postgres client_connection_check_interval
Saw this post on LinkedIn yesterday: I also somehow missed this setting for years. And it’s crazy timing, because it’s right after I published a blog about seeing the exact problem this solves. In my blog post I mentioned “unexpected behaviors (bugs?) in… Postgres itself.” Turns out Postgres already has the fix; it’s just disabled … … Continue reading →| Ardent Performance Computing
How Blocking-Lock Brownouts Can Escalate from Row-Level to Complete System Outages
This article is a shortened version. For the full writeup, go to https://github.com/ardentperf/pg-idle-test/tree/main/conn_exhaustion This test suite demonstrates a failure mode when application bugs which poison connection pools collide with PgBouncers that are missing peer config and positioned behind a load balancer. PgBouncer’s peering feature (added with v1.19 in 2023) should be configured if multiple PgBouncers are being used … … Continue reading →| Ardent Performance Computing
KubeCon 2025: Bookmarks on Memory and Postgres
Just got home from KubeCon. One of my big goals for the trip was to make some progress in a few areas of postgres and kubernetes – primarily around allowing more flexible use of the linux page cache and avoiding OOM kills with less hardware overprovisioning. When I look at Postgres on Kubernetes, I think … … Continue reading →| Ardent Performance Computing
Data Safety on a Budget | Ardent Performance Computing
Many experienced DBAs joke that you can boil down the entire job to a single rule of thumb: Don’t lose your data. It’s simple, memorable, and absolutely true – albeit a little…| Ardent Performance Computing
RHEL on ZFS Root: An Unholy Experiment
Running Red Hat Enterprise Linux on ZFS root is not supported. I did it anyway. Here’s how this cursed configuration came to be, why you shouldn’t replicate it, and what the proper alternative looks like.| Larvitz Blog
SELinux: A Practical Guide for Fedora and RHEL
Moving beyond “setenforce 0” - a practical guide to understanding, troubleshooting, and working with SELinux on Fedora and Red Hat Enterprise Linux.| Larvitz Blog
Podman 5.8: Quadlet Multi-File Install, Automatic SQLite Migration, and the Road to 6.0
Podman 5.8 lands with multi-file Quadlet installs, automatic BoltDB-to-SQLite migration in preparation for Podman 6.0, and several quality-of-life improvements for container workflows.| Larvitz Blog
Voraussetzungen für den E-Mail-Versand zu großen Mailprovidern (GMX, Web.de, Microsoft)
Wer erst seit kurzem einen eigenen Mailserver betreibt, wird vielleicht schon festgestellt haben, dass die eigenen E-Mails von anderen Server nicht immer akzeptiert werden und schnell im Spamverdachts-Ordner landen. Tatsächlich gibt es einige Dinge zu beachten, wenn man in die Liga der seriösen Mailprovider aufgenommen werden will. Um bei fremden System einen guten Ruf zu erreichen, sollten die folgenden Merkmale erfüllt sein: Statische IP-Adresse - möglichst nicht aus einem Netz für Pri...| thomas-leister.de
Linux Kernel 6.19 Is Out: What Sysadmins Should Actually Care About
Linux 6.19 has been officially released (announced by Linus Torvalds on February 8, 2026) and is now available from the upstream release channels. For most production environments, the real question isn’t “what’s new?”, but “what changes my risk profile, my observability, or my upgrade playbook?”. Kernel 6.19 is a mixed release in the best sense: […]| System Administration
VirtIO and QEMU Guest Agent: The Installation That Turns a “Working” Windows VM into a Production-Ready VM on Proxmox
In many Proxmox VE environments, Windows remains a common guest OS: application servers, remote desktops, corporate tools, or legacy workloads that have not yet been modernized. But there is a clear operational difference between a virtual machine that simply “boots and runs” and one that is truly ready for day-to-day datacenter operations: installing VirtIO drivers […]| System Administration
FRCTL releases SWRL Lite, a FREE modulation plugin for Windows, macOS, Linux
FRCTL has released SWRL Lite, a free modulation plugin for macOS, Windows, and Linux. SWRL Lite combines six movement-based effects into a super clean interface with just two controls: Amount and Mix. The idea here is simple, and I like it. You turn one knob to enhance your sound with motion, depth, and character. Then, [...] View post: FRCTL releases SWRL Lite, a FREE modulation plugin for Windows, macOS, Linux| Bedroom Producers Blog
NexPhone: a dual-booting phone with Linux (and even Windows) support
Nex is an interesting company and they make cool products. I had the chance to use the NexDock back when the Steam Deck first launched and it was awesome. But back in January, the announced the NexPhone. Somehow I missed this until just now... but I'm talking about| The Bryant Review
This One Multiplexer Replaced Tmux, Screen, and My Entire Terminal Workflow
Zellij is a modern terminal multiplexer similar to Tmux, offering a clear, organized interface and efficient session management.| Make Tech Easier
How to Fix the “Cannot Connect to the Docker Daemon” Error
Struggling with “Cannot connect to Docker daemon”? Learn why it happens and practical fixes to get Docker running smoothly.| Make Tech Easier
What Are The Types Of Process Management In Linux?Explain
Types of Process Management Linux groups processes according to their function and interaction: Foreground Processes (Interactive): These are initiated by the user on a terminal (for example, by entering nano). They block the terminal till they’re done and rely on user input. Background Processes (Non-interactive): Batch processes are automated scripts or tasks that are set up to […]| Online Tutorial Hub
Process Management In Linux Commands With Examples
Process Management in Linux In Linux and UNIX-based operating systems, one of the most crucial ideas is process management. Whether you’re running a command at the terminal, playing a movie, or launching a browser, every action you take on a Linux system takes the form of a process. You can effectively manage system resources, solve […]| Online Tutorial Hub
What Is SteamOS Holo? Features, Download & PC Install Guide
What is SteamOS holo? The 2026 “Console-Slayer” is SteamOS (Holo). Early in 2026, SteamOS 3.x (codenamed “Holo”) has effectively transcended its function as the “Steam Deck OS.” It is still at the core of Valve’s handheld, but it has now spread into a wider range of “Powered by SteamOS” gadgets and the eagerly anticipated 2026 […]| Online Tutorial Hub
The future for Tyr [LWN.net]
The team behind Tyr started 2025 with little to show in our quest to produce a Rust GPU driv [...]| LWN.net
GCC5 and the C++11 ABI | Red Hat Developer
The GNU C++ team works hard to avoid breaking ABI compatibility between releases, including between different -std= modes. But some new complexity requirements in the C++11 standard require ABI| Red Hat Developer
Adventures in Guix packaging
We talked about Nemin’s first impressions of the Guix System as someone coming from a Nix environment, but today they’ve got a follow-up article diving into the experience of creating new packages for Guix. I spent about a week packaging WezTerm and learning the ropes of being a Guix contributor along the way. During the packaging process I stumble many times, only to stand back up and figure out a solution. I also explain some of my complaints about the peculiarities of the process, but ...| OSnews
Microsoft Open-Sources LiteBox Library OS with Safe App Sandboxing
Microsoft has introduced LiteBox, a Rust-based sandboxing library OS that has enabled secure, low-overhead Linux app isolation on Windows without full VMs. The post Microsoft Open-Sources LiteBox Library OS with Safe App Sandboxing appeared first on WinBuzzer.| WinBuzzer
Linux 6.19 Released
Linux 6.19 Released Linux 6.19 is the first release of 2026, shipping several contributions from Igalia among its more than 14 thousand commits — keeping up the consistent work from last year. Have a look at our 2025 retrospective! For an overview of this kernel release and features, check the KernelNewbies page. Once again, our team delivered improvements, features, and bug fixes across different areas of the kernel — ranging from debugging and core infrastructure to filesystems, energy ...| Igalia
Igalia Kernel Team 2025 Achievements: A Retrospective
In 2025, the Igalia Kernel team made extensive contributions across the Linux ecosystem. Over the year, Igalians authored 362 commits to Linux kernel releases published in 2025, 321 commits to the sched_ext schedulers and tools project—with a strong focus on the LAVD BPF scheduler—and additional contributions to projects such as igt-gpu-tools (11 commits), libfuse (six commits), and others. This retrospective focuses on the two areas where our impact was most significant: upstream Linux k...| Igalia
A Samba Share on Manjaro – Logikal Blog
Manjaro is one of the better Arch based Linux distributions, but it has notorious frustrations with Samba. . .| Logikal Blog
Experimental Zones Protocol Merged To Wayland After 2+ Years, 620+ Comments - Phoronix
After the merge request was opened back in 2023 and after going through 628 comments/activity, merged now to Wayland Protocols is the experimental zones 'xx-zones' implementation for area-limited window positioning.| www.phoronix.com
How to review an AUR package | bertptrs.nl
On Friday, July 18th, 2025, the Arch Linux team was notified that three AUR packages had been uploaded that contained malware. A few maintainers including myself took care of deleting these packages, removing all traces of the malicious code, and protecting against future malicious uploads.| bertptrs.nl
postmarketOS // FOSDEM 2026 + Hackathon
Aiming for a 10 year life-cycle for smartphones| postmarketOS
Linux kernel 6.0
Linux kernel 6.0 introduces diverse performance improvements, support for new hardware and security fixes, among other things.| Stackscale
Linux kernel documents an emergency “project continuity” plan for life after Torvalds - System Administration
For more than three decades, the Linux kernel’s development has had a clear “last step”: subsystem maintainers send pull requests, reviews happen in public,| System Administration
The Linux kernel prepares for a “day after” Linus Torvalds
For more than three decades, the Linux kernel has grown with a comfortable paradox: a massive project maintained by hundreds of people worldwide, yet with a| Stackscale
ZFS on Linux: How to Use It Properly (With Real Examples)
Learn how to use ZFS on Linux correctly with real-world examples for storage pools, snapshots, backups, and performance tuning.| Fresh Tech Tips
March 2024 - Help Net Security
XZ Utils backdoor update: Which Linux distros are affected and what can you do?| Help Net Security
Forget third-party utilities: meet Armbian Imager
Armbian Imager eliminates the guesswork from flashing SBC images. Real-time board detection, persistent caching, and built-in safety make installation fast, simple, and risk-free| Armbian blog
Deploying Python Web Applications with Docker | Chris Warrick
Friendship ended with uWSGI Emperor, now Docker is my best friend| Chris Warrick
GNOME 40 available in Gentoo
GNOME 40 was released at the end of March, and yesterday I added the last bits of it to Gentoo. You may not think that's fast, and you'd be right, but it's a lot faster than any GNOME release has been added to Gentoo that I can recall. I wasn't looking to become Gentoo's GNOME maintainer when I joined the team 18 months ago. I only wanted to use a GNOME release that was a little less stale. So how did I get here? I asked about the GNOME 3.26 status when 3.28 and 3.30 were already out. Repeat ...| mattst88's blog
Combining constants in i965 fragment shaders
On Intel's Gen graphics, three source instructions like MAD and LRP cannot have constants as arguments. When support for MAD instructions was introduced with Sandybridge, we assumed the choice between a MOV+MAD and a MUL+ADD sequence was inconsequential, so we chose to perform the multiply and add operations separately. Revisiting that assumption has uncovered some interesting things about the hardware and has lead us to some pretty nice performance improvements. On Gen 7 hardware (Ivybridge,...| mattst88's blog
Laptop choices and aftermath
In November I was lamenting the lack of selection in credible Haswell-powered laptops for Mesa development. I chose the 15" MacBook Pro, while coworkers picked the 13" MBP and the System76 Galago Pro. After using the three laptops for a few months, I review our choices and whether they panned out like we expected. CPURAMGraphicsScreenStorageBattery 13" MacBook Pro2.8 GHz 4558U16 GiBGT3 - 1200 MHz13.3" 2560x1600512 GiB PCIe71.8 Wh 15" MacBook Pro2.0 GHz 4750HQ16 GiBGT3e - 1200 MHz15.4" 2880x...| mattst88's blog
mattst88's blog - Difficulty in Finding a Good Development Laptop
mattst88's blog - Difficulty in Finding a Good Development Laptop| mattst88.com
Survey says: Container security issues continue to befuddle software developers
Container security incidents are becoming more common, with nearly one in four respondents to a new survey from BellSoft saying they have experienced a security incident. The survey concluded that questions about security practices remain unresolved. According to the survey by OpenJDK provider BellSoft, 62% of participating developers reported that human errors were the biggest … continue reading The post Survey says: Container security issues continue to befuddle software developers appe...| SD Times
What Are The Arch Linux Advantages And Disadvantages?
Learn about the Arch Linux history, philosophy, tools, installation, AUR, advantages, disadvantages, and how it compares to Ubuntu and Fedora.| Tutorials
Beating an old, but not dead horse: what to do with the Oxygen and Air themes? – Filip Fila's blog
Minimalism came in like a wrecking ball somewhere around 2013. It delivered a terminal diagnosis to all but a few prevailing designs at the time. One of them, called Oxygen, had reigned supreme in …| Filip Fila's blog
Useful linux/unix commands
Collection of handy command-line tricks for Unix/Linux systems| Alan Norbauer
Linux Search and Replace
Command-line search and replace across multiple files in Unix/Linux| Alan Norbauer
Discover Roundup: Mac Software Communities
This month's Discover Roundup highlights Discourse communities built around beloved indie Apple apps - NetNewsWire, Bear, and Infuse - where developers engage directly with users and peer support becomes searchable knowledge.| Discourse
Linux 6.18 improves server performance under DDoS attacks
Recent kernel updates led by Google engineer Eric Dumazet, and first reported by Michael Larabel (Phoronix), show that Linux 6.18 delivers significant improvements in how servers handle high-rate DDoS traffic. The work focuses on optimising the UDP receive path under stress—scenarios where multiple CPU cores handle massive packet floods targeting one or more sockets. Dumazet’s […] The post Linux 6.18 improves server performance under DDoS attacks first appeared on FastNetMon DDoS Detect...| FastNetMon DDoS Detection Tool
Unix Operating System: Features, Benefits, Drawbacks & Types
"Unixed Information and Computing System" (UNIX)| Tutorials
通信量を劇的に節約!Terminal System 2のデルタアップデート機能
aptpod Advent Calendar 2025 12月19日の記事です。 intdashグループの野本です。組込Linuxソフトウェア開発を担当しています。 本記事では、車載などのエッジ環境で利用可能なゲートウェイアプライアンス intdash Terminal System 2 向けに開発している デルタアップデート機能 について紹介します。| aptpod Tech Blog
AppImageでLinuxアプリケーションを配布しよう
intdashグループの大久保です。aptpod Advent Calendar 2025の12月3日の記事を担当します。 Linuxでアプリケーションを開発するとき、その依存ライブラリ含めどう配布するかは悩ましい問題です。debのようなパッケージであれば、対応するディストリビューションごとにビルドしなければなりません。muslであれば単体で動作する実行バイナリを作れますが、依存するライブラリが...| aptpod Tech Blog
MARC: Mailing list ARChives
*BSD| marc.info
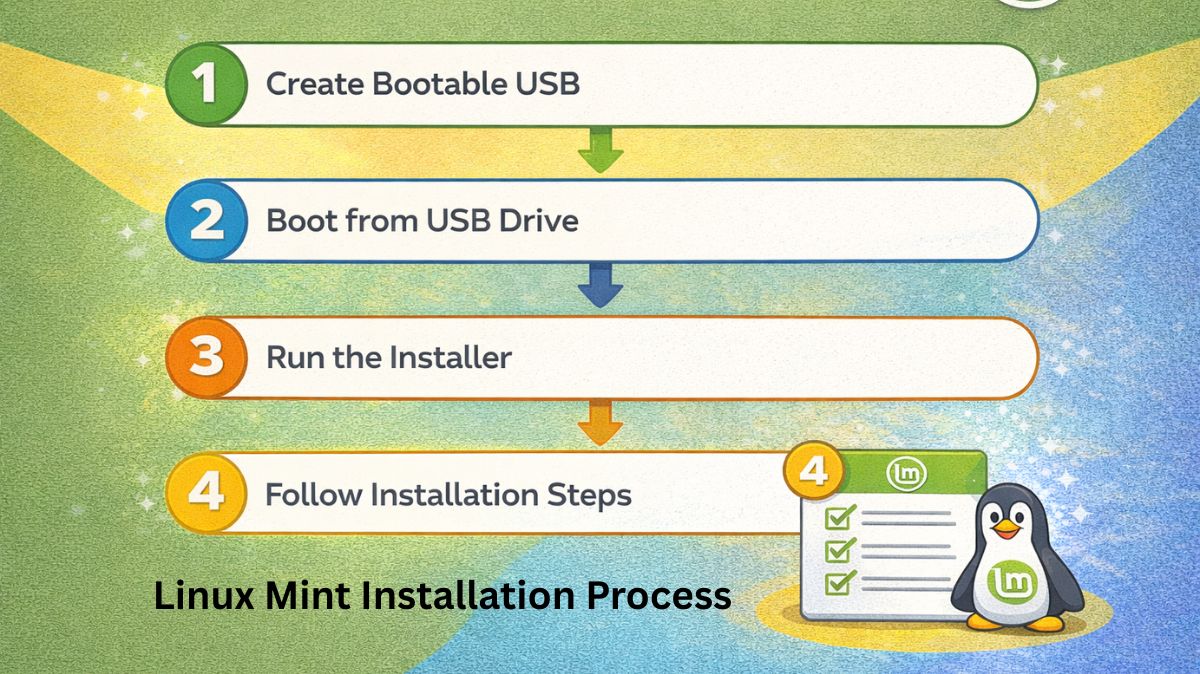
Linux Mint Installation Process Step By Step For Beginners
Learn about Linux Mint Installation Process with simple steps for downloading ISO, creating bootable USB, installing codecs, and setting up users.| Tutorials
January 2026 ClangBuiltLinux Work | Nathan Chancellor
Occasionally, I will forget to link something from the mailing list in this post. To see my full mailing list activity (patches, reviews, and reports), you can view it on lore.kernel.org. Linux kernel patches Build errors: These are patches to fix various build errors that I found through testing different configurations with LLVM or were exposed by our continuous integration setup. The kernel needs to build in order to be run :)| Nathan Chancellor
RISC-V Linux on ESP32
I've been playing with the idea of running linux on ESP32 since the first days I've met its more robust module, the WROVER-B, on paper it seem possible since its a dual core 240Mhz and has 16MB flash and 8MB RAM, compared to our antique machines that could run linux, it seems like a beast.| Dror Gluska
Is it possible to program an AVR chip (atmega328p) via i2c?
Currently I am using avrdude and I'm programming my atmega328p chip via the spi pins by pulling the RESET pin low (spidev programmer). In my project I'm using predominantly i2c and this the only place where spi is used. I was wondering whether it is possible to program the chip via the i2c protocol and remove the spi connections altogether? My searches were unsuccessful.| Recent Questions - Arduino Stack Exchange