How to Store Session Tokens in a Browser (and the impacts of each) - ropnop blog
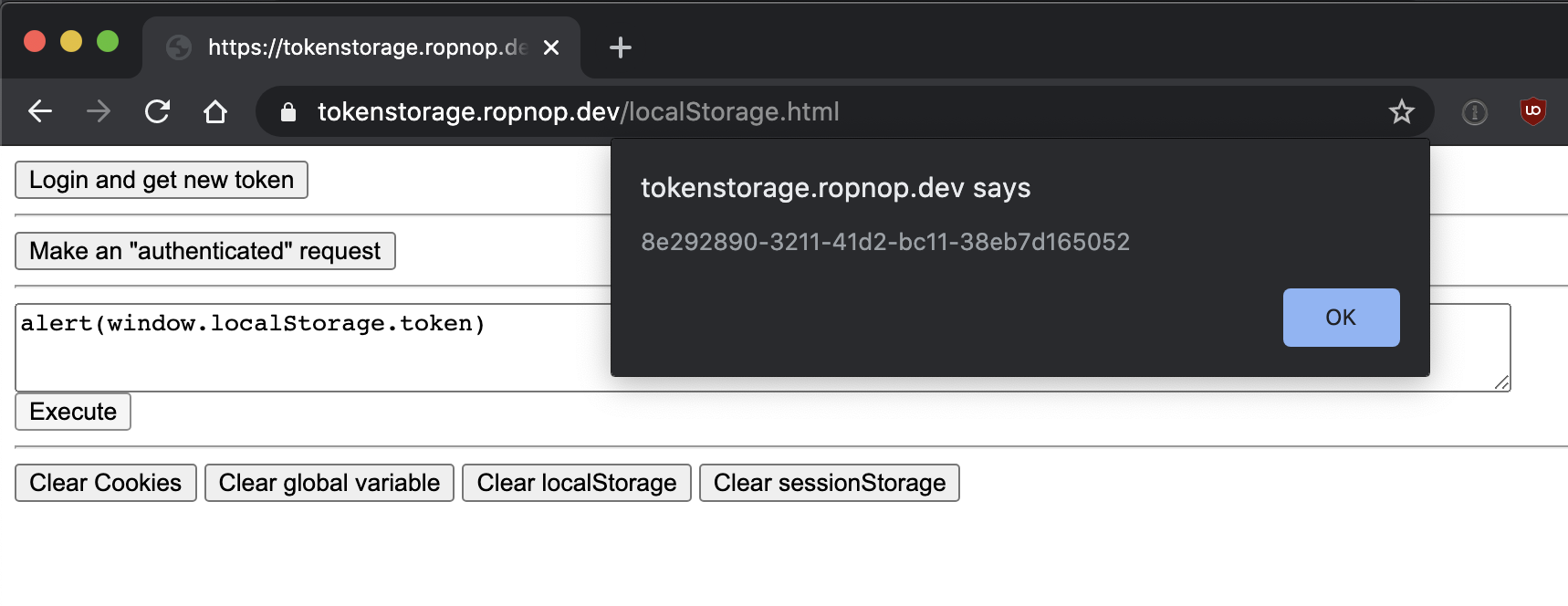
A common question when building a SPA is: where do I store my session tokens? I’ll talk through the main options and the pros/cons of each| ropnop blog
Learning Go Concurrency From Factorio - ropnop blog
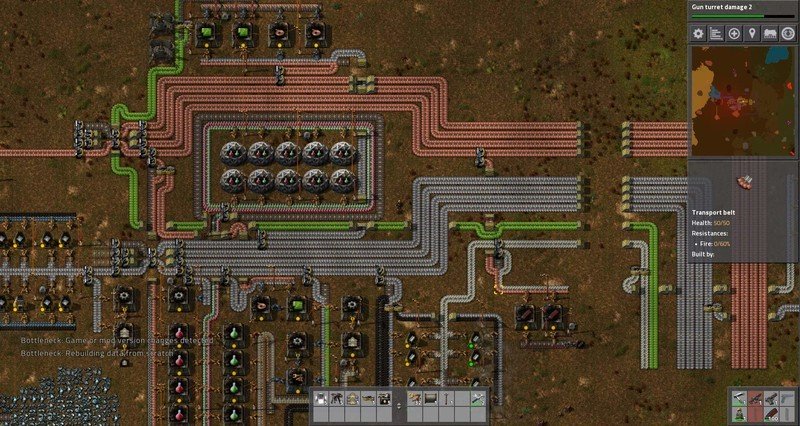
Go’s concurrency model confused me at first, but it finally clicked when I thought of it like building an assembly line in Factorio| ropnop blog
Hosting the CLR and executing .NET assemblies from Go - ropnop blog
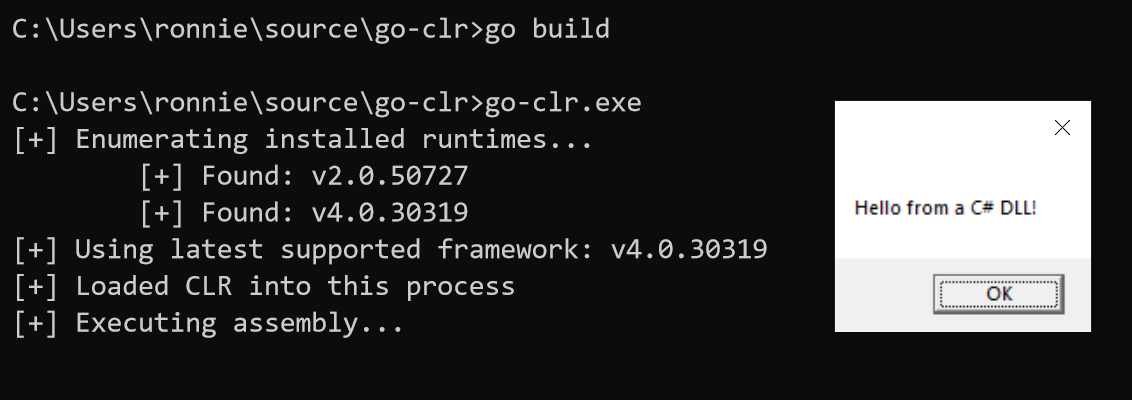
Write up of my journey figuring out how to host the CLR and execute .NET assemblies from memory in pure Go.| ropnop blog
Proxying and Intercepting CLI Tools - ropnop blog
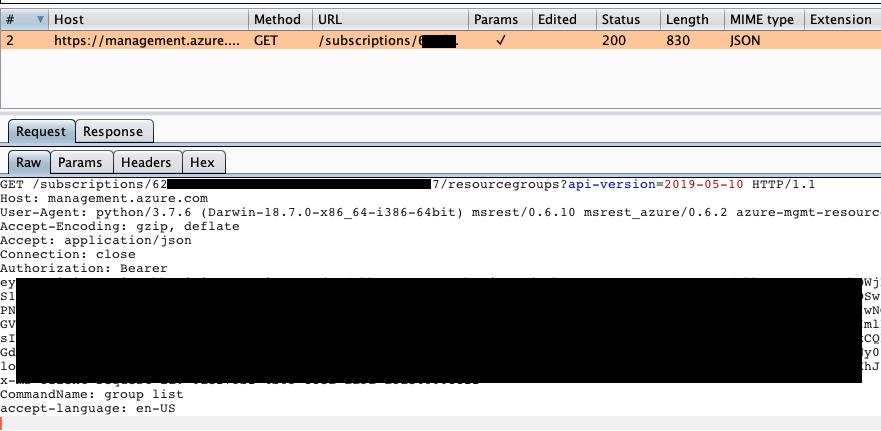
Sometimes you need to intercept traffic from CLI tools. In this post I cover using Burp to intercept traffic from Java, Python, Node and Go CLIs| ropnop blog
ChiBrrCon 2020: Don't Cross Me! Same Origin Policy and all the "cross" vulns - ropnop blog
All too often, even seasoned web security professionals get mixed up by the subtle differences between cross site scripting (XSS), cross site request forgery (CSRF) and cross origin resource sharing (CORS). In this talk, I’ll start at the basics and discuss the browser security model and same origin policy - the security boundary that protects and limits JavaScript’s power within the browser. After covering the basics of origins and JavaScript, I’ll walk through each of the three “cro...| ropnop blog
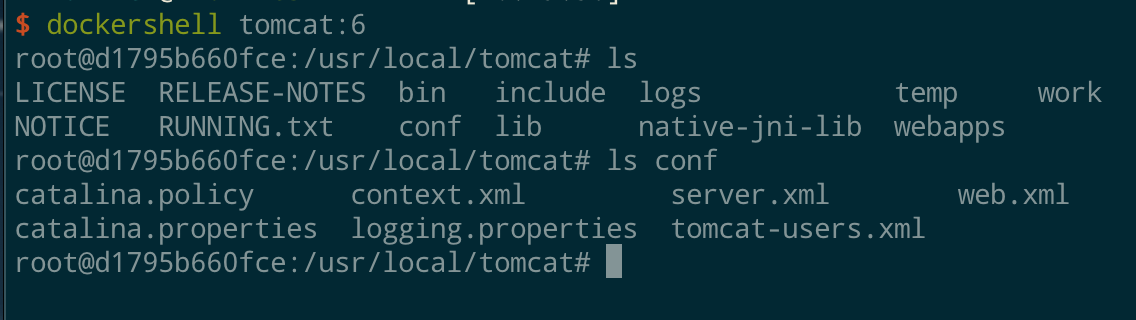
Docker for Pentesters - ropnop blog
Docker has become such an integral part of my worfklow recently. These examples should demonstrate how Docker can help you be a more efficient pentester| ropnop blog
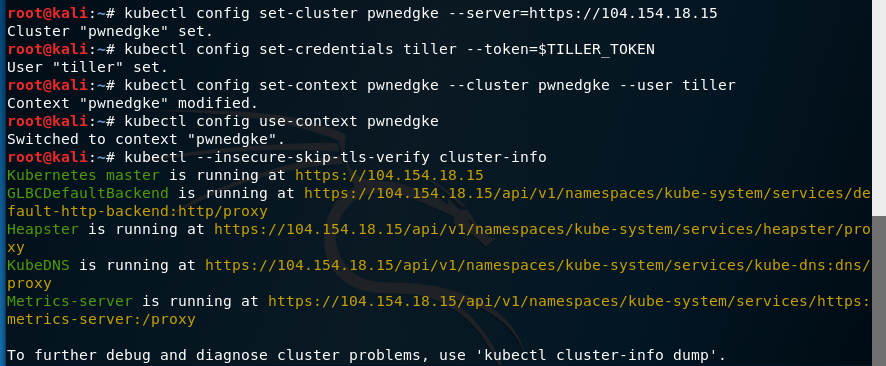
Attacking Default Installs of Helm on Kubernetes - ropnop blog
Default installations of Helm on Kubernetes can make it trivial for attackers to escalate to cluster admin. In this post I’ll demonstrate how.| ropnop blog
OWASP Chicago 2018 - Pentesting with Serverless Infrastructure - ropnop blog
Slides Supplemental Serverless Toolkit available here: https://github.com/ropnop/serverless_toolkit| ropnop blog
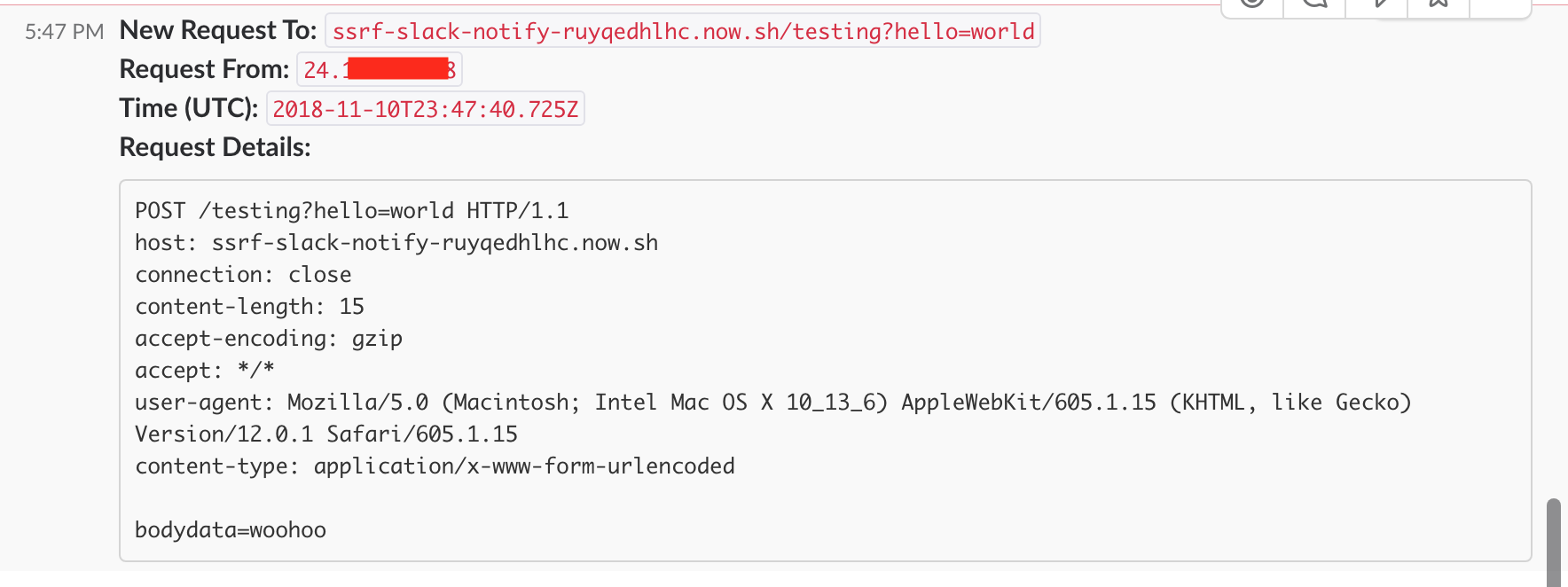
Serverless Toolkit for Pentesters - ropnop blog
Serverless functions have so much potential - here’s a few useful examples I use when pentesting or doing bug bounties. Who needs testing infrastructure?| ropnop blog
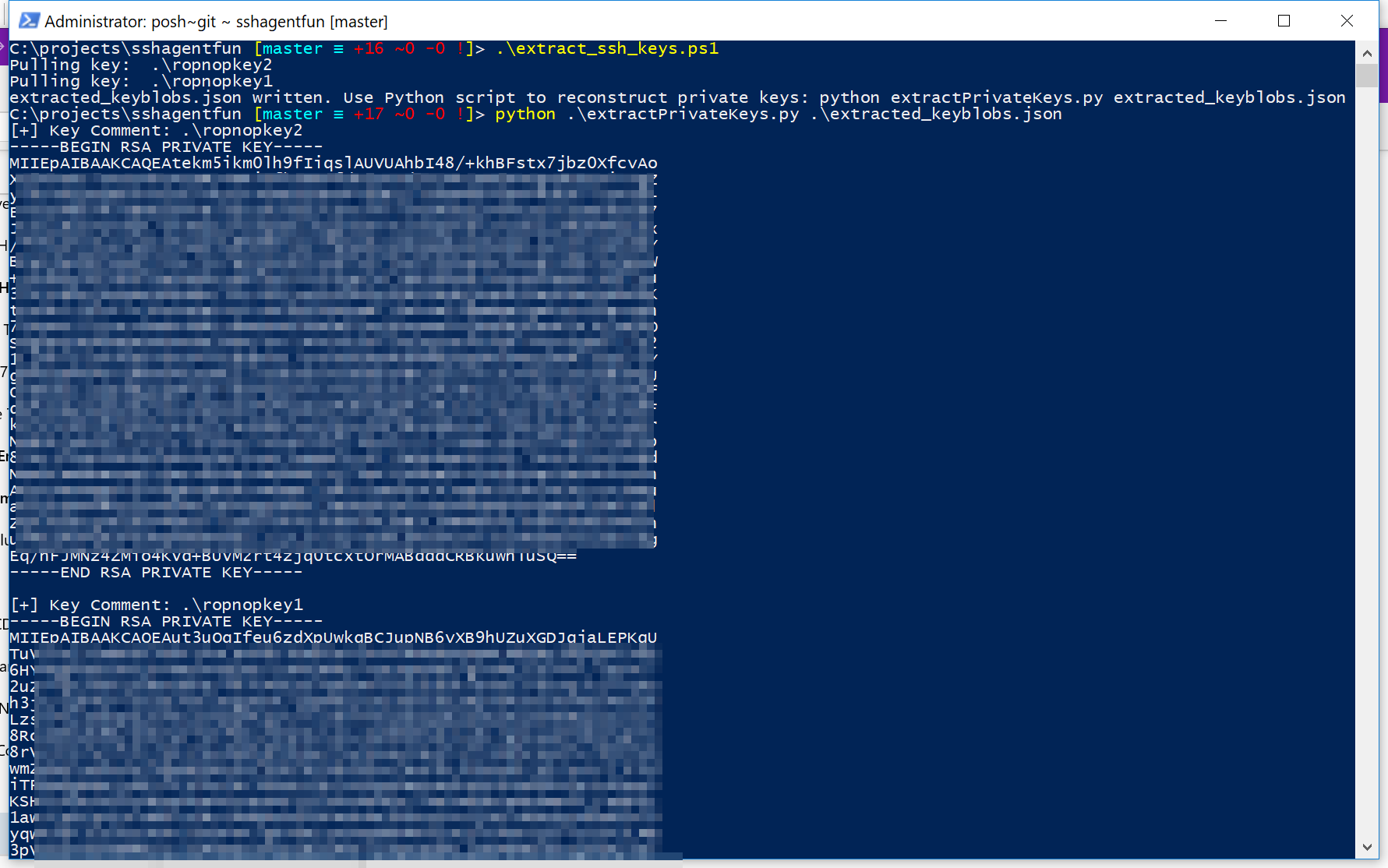
Extracting SSH Private Keys From Windows 10 ssh-agent - ropnop blog
The newest Windows 10 update includes OpenSSH utilities, including ssh-agent. Here’s how to extract unencrypted saved private keys from the registry| ropnop blog
Thotcon 2018 - Fun With LDAP, Kerberos (and MSRPC) in AD Environments - ropnop blog
Slides Supplemental The original (large) PowerPoint wih all embedded GIFs/Videos: https://1drv.ms/p/s!Aq5mEA03Lijrg9h-hsezBkUC5qwXag| ropnop blog
Configuring Burp Suite With Android Nougat - ropnop blog
Android Nougat changed the default behavior for apps, so installing the Burp CA to user certs no longer works. Here’s two ways to bypass it| ropnop blog
SANS Holiday Hack 2017 Writeup - ropnop blog
The SANS team hit another homerun with the HHC including awesome challenges that mimicked real-world pentest activities. Here’s my solutions!| ropnop blog
Configuring a Pretty and Usable Terminal Emulator for WSL - ropnop blog
I’m a big fan of Bash on Windows (WSL), but was unable to find a good terminal emulator to use. In this post I talk about configuring Terminator for WSL| ropnop blog
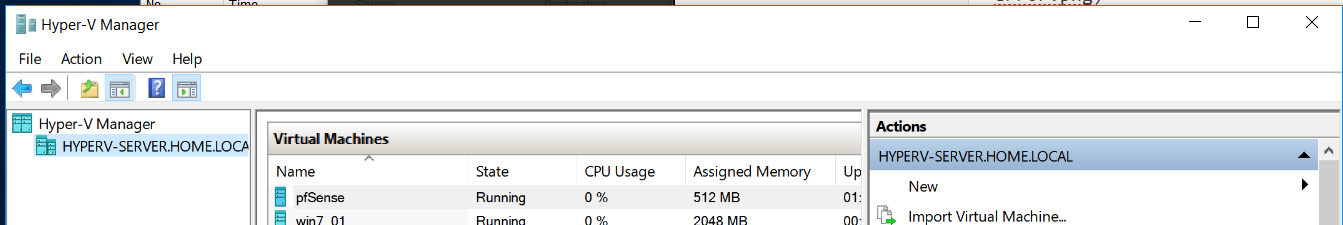
Remotely Managing Hyper-V in a Workgroup Environment - ropnop blog
After lots of mucking around, this is the bare minimum configuration I found to successfully connect to and mange Hyper-V in a non-domain network| ropnop blog
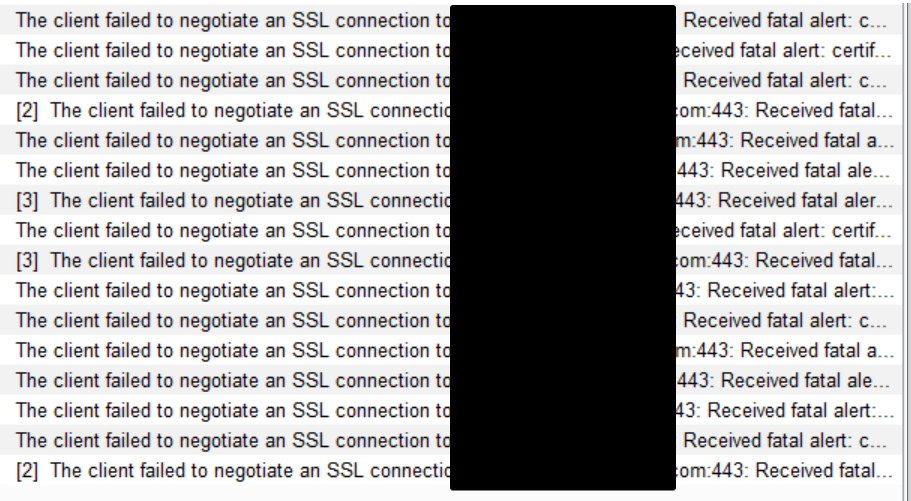
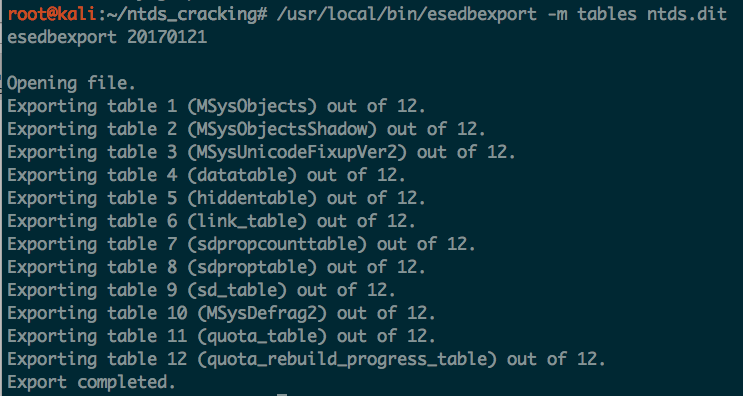
Extracting Hashes and Domain Info From ntds.dit - ropnop blog
If you end up with a copy of NTDS.dit and the SYSTEM registry hive, you can extract domain computer info offline and user NTLM hashes for cracking.| ropnop blog
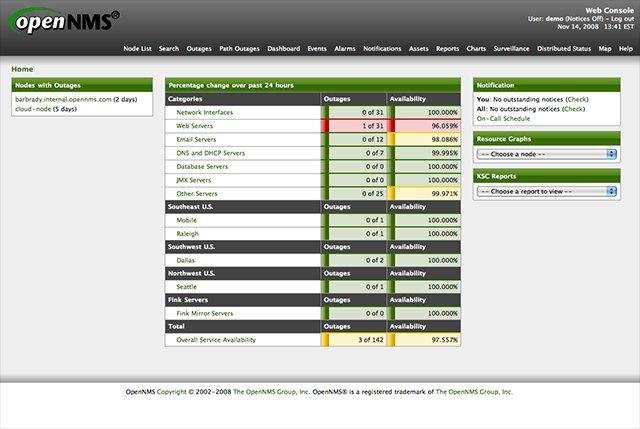
Cracking OpenNMS Password Hashes - ropnop blog
After compromising an OpenNMS server, I recovered salted password hashes. I couldn’t find any info online, so I reversed them and wrote a tool to crack them| ropnop blog
Sans Holiday Hack 2016 - Writeup - ropnop blog
After my last report for work went out the door and my company entered its end-of-year shutdown period, I found myself at my parents house for several days for the holidays, relaxed and with nothing to do. I saw some people on Twitter talking about the SANS Holiday Hack Challenge, and decided I would finally give it a try. I started on Christmas Eve and after several days of borderline dangerous obsessive completion-compulsion, I had solved all the challenges.| ropnop blog
DerbyCon 2016 - Abusing Linux Trust Relationships - ropnop blog
Recording Slides Supplemental Demo Video:| ropnop blog
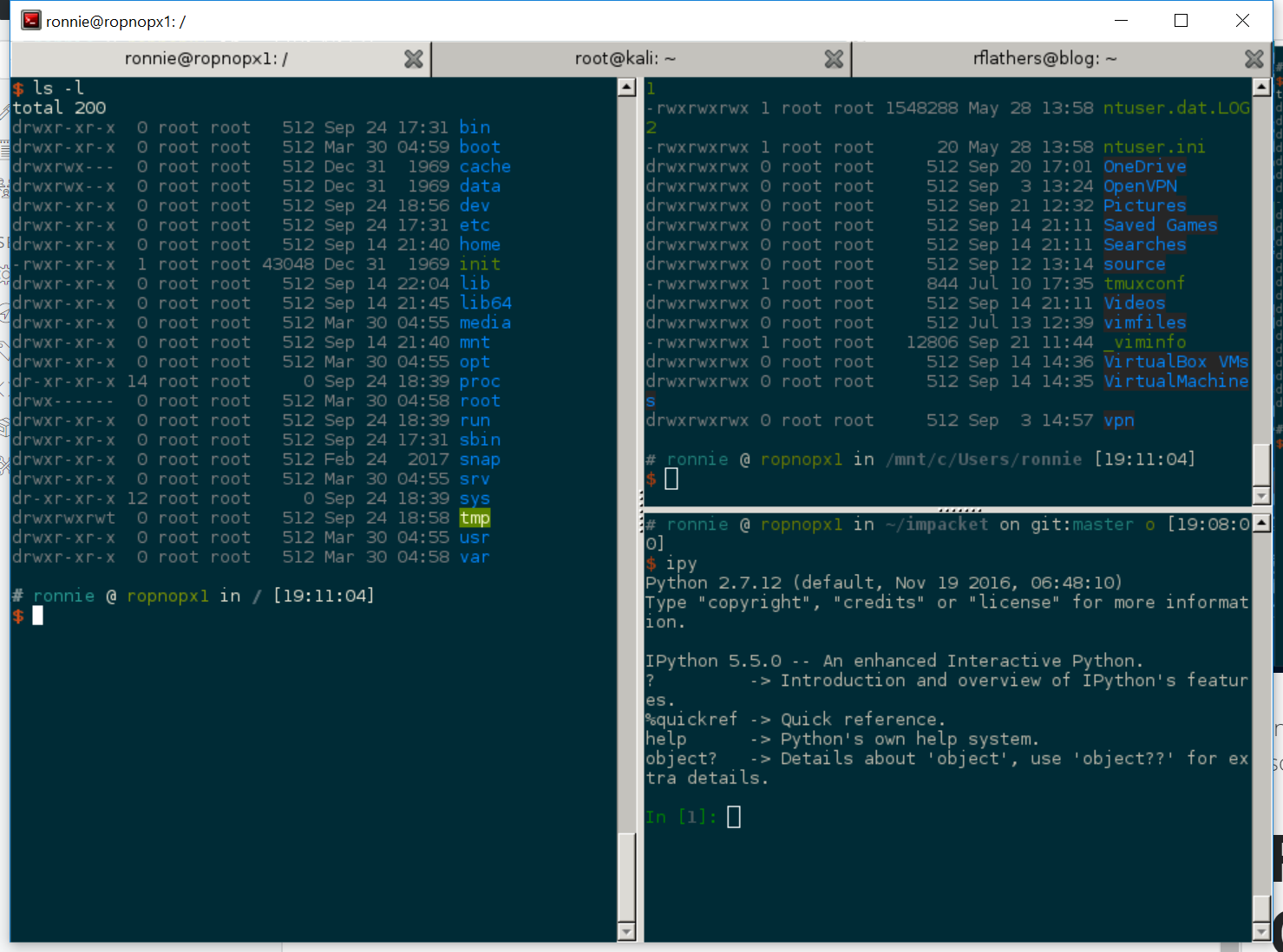
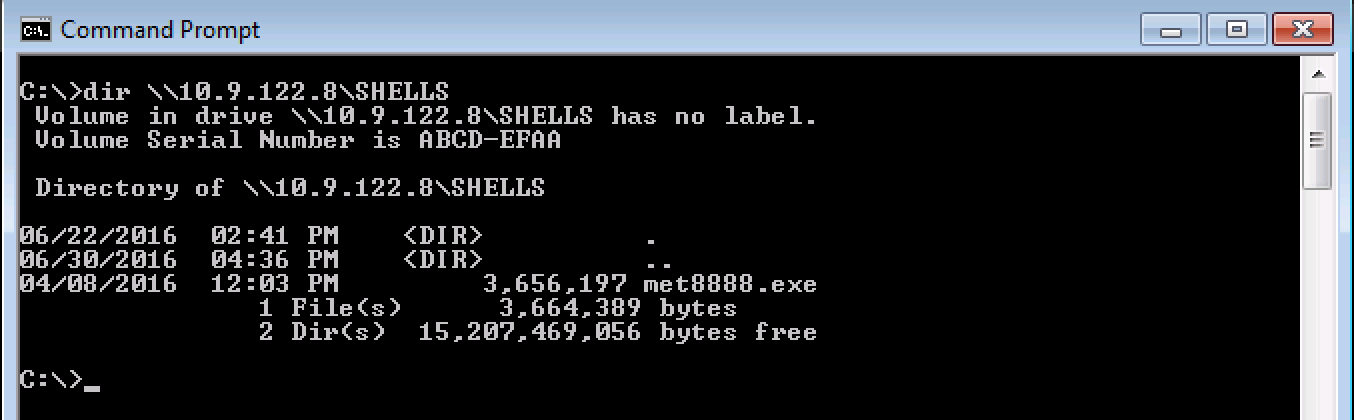
Transferring Files from Linux to Windows (post-exploitation) - ropnop blog
I often need to copy a tool or a payload from my Kali linux attack box to a compromised Windows machine. These are some of my favorite techniques.| ropnop blog
Practical Usage of NTLM Hashes - ropnop blog
I’ve shown all the different ways to own a Windows environment when you have a password - but having a hash is just as good! Don’t bother cracking - PTH!| ropnop blog
Abusing Linux Trust Relationships - Thotcon Talk - ropnop blog
Had an awesome time presenting at Thotcon this year. I plan to expand on this topic quite a bit and eventually turn it into a blog posts/series, but in the meantime, here’s the slides and the demo video| ropnop blog
Thotcon 2016 - Abusing Linux Trust Relationships - ropnop blog
Slides Supplemental Demo Video:| ropnop blog
Using Credentials to Own Windows Boxes - Part 3 (WMI and WinRM) - ropnop blog
WMI and WinRM are two Windows administrative “features” that are ripe for abuse if you have credentials. In this post, I’ll show how to (mis)use them…| ropnop blog
Using Credentials to Own Windows Boxes - Part 2 (PSExec and Services) - ropnop blog
Pentesters use PsExec style commands all the time, and in this post I’m going to explore and manually recreate the technique using native Windows tools.| ropnop blog
Using Credentials to Own Windows Boxes - Part 1 (from Kali) - ropnop blog
Du’h…if you have admin creds you can own a box. But how many different ways can you do it? Here’s a blog-ified version of my notes and my favorite methods| ropnop blog
Plundering Docker Images - ropnop blog
On a recent pentest, we recovered credentials to a private Docker registry. Looting the contained images yielded us source code and admin ssh keys.| ropnop blog
Upgrading Simple Shells to Fully Interactive TTYs - ropnop blog
Catching a reverse shell over netcat is great…until you accidentally Ctrl-C and lose it. These techniques let you upgrade your shell to a proper TTY| ropnop blog