Shifting boundaries: Exploiting an Integer Overflow in Apple Safari - Exodus Intelligence
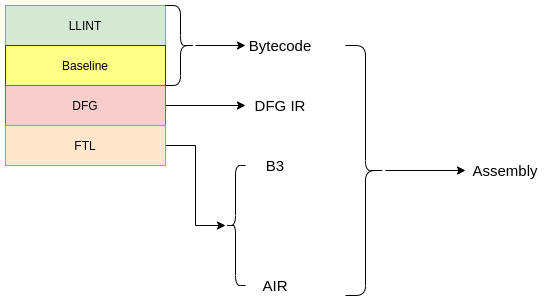
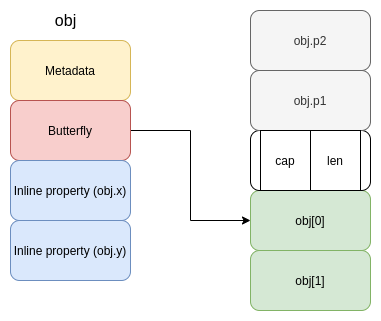
By Vignesh Rao Overview In this blog post, we describe a method to exploit an integer overflow in Apple WebKit due to a vulnerability resulting from incorrect range computations when optimizing Javascript code. This research was conducted along with Martin Saar in 2020. We show how to convert this integer overflow into a stable out-of-bounds ... Read more Shifting boundaries: Exploiting an Integer Overflow in Apple Safari| Exodus Intelligence