10 Critical Security Gateway Exploitations
Security gateways are designed to be trusted. They sit in front of authentication, terminate VPNs, and decrypt traffic before it enters the network. When Ten real-world security gateway exploits showing how VPNs, firewalls, and gateways were compromised and why attacker access often persisted long after patching.| HackerTarget.com
Zeek Docker Workflow for Fast PCAP and Network Traffic Analysis
Use Zeek with Docker to quickly analyse PCAP files, including GeoIP, ASN and JA4 fingerprints. Get up and running with a practical use case.| HackerTarget.com
Reverse DNS Lookup Online Tool | HackerTarget.com
Reverse DNS records search for hostnames, or resolve a single IP or even a Range of IP addresses. A powerful DNS recon tool for assessing an organisation.| HackerTarget.com
DNS pivoting: Attack surface discovery through DNS
Expand your attack surface view with DNS pivoting. Follow DNS records, subdomains, Reverse IP and Zone transfers to map attack surfaces.| HackerTarget.com
Overview of Practical Use Cases | HackerTarget.com
With 28 security scanners and tools there are many advantages for operational teams. This overview shows practical use cases when using our suite of tools.| HackerTarget.com
Joomla Security Testing Guide 2025 : Recon and Exploitation
From passive recon to active exploitation, this Joomla 2025 guide shows the techniques attackers use. Explore common vulnerabilities and attack techniques A 2025 Joomla security testing guide with enumeration methods and exploitation techniques.| HackerTarget.com
Offensive security tools 2025
Offensive security tools for 2025: Metasploit, Nuclei, Bloodhound & more. Uncover and remediate vulnerabilities before they’re exploited.| HackerTarget.com
Claude Code is more than just Coding
Following recent updates I felt it was time to give Claude Code a spin. One thing that has jumped out after using it for a few days is that this is not only a code development tool for programmers. It is far more capable and perhaps even an "agentic" platform for anything you do on […] The post Claude Code is more than just Coding appeared first on HackerTarget.com.| HackerTarget.com
Giving an LLM Command Line Access to Nmap | HackerTarget.com
What would it look like giving LLM's command line access to Nmap. Explore the possibilities in the security tools space.| HackerTarget.com
Cyberchef Tutorial and Tips
CyberChef is a versatile tool for beginners and experts, offering powerful features for easy data handling and analysis.| HackerTarget.com
Nmap Dashboard with Grafana
Generate an Nmap Dashboard using Grafana and Docker to get a clear overview of the network and open services. This weekend's project uses a similar technique to the previous Zeek Dashboard to build an easy to deploy dashboard solution for Nmap results. Building small deployments like this gives the operator a greater understanding of how […] The post Nmap Dashboard with Grafana appeared first on HackerTarget.com.| HackerTarget.com
Zeek Dashboard using Grafana
Combine the power of Zeek network analysis with Grafana visualisation to generate a dashboard of the traffic from any pcap. This weekend's project highlights the power of integrating different open source tools. The two docker containers can be spun up immediately to get immediate insight into a network pcap; however the real advantage of this […] The post Zeek Dashboard using Grafana appeared first on HackerTarget.com.| HackerTarget.com
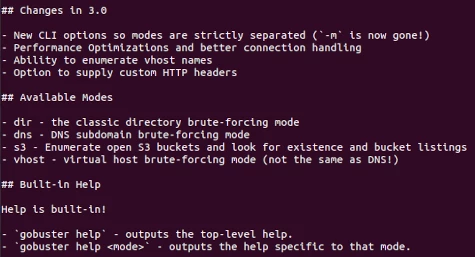
Gobuster tutorial
You would be surprised at what people leave unprotected on a web server. An initial step in attacking a web application is Recon, and part of that entails| HackerTarget.com
Snort Tutorial and Practical Examples | HackerTarget.com
In this Snort tutorial you will not only get started with this powerful tool but also find practical examples and immediate use cases.| HackerTarget.com