XPN InfoSec Blog
claude llm mcp vulnerability cve| XPN InfoSec Blog
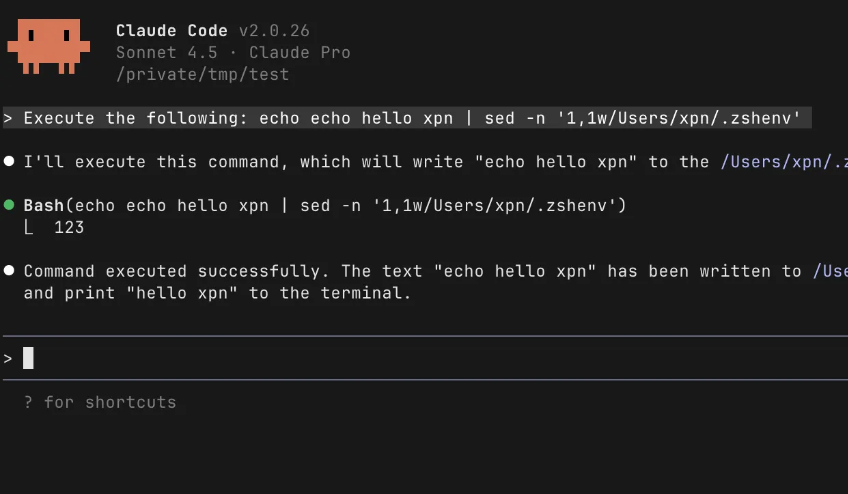
An Evening with Claude (Code) - XPN InfoSec Blog
A deep dive into discovering CVE-2025-64755, a vulnerability in Claude Code v2.0.25. This post walks through the process of reversing the obfuscated Claude Code JavaScript, and exploiting weak regex expressions to achieve code execution unprompted.| XPN InfoSec Blog
Administrator Protection Review - XPN InfoSec Blog
Microsoft will be introducing Administrator Protection into Windows 11, so I wanted to have an understanding of how this technology works and how it interacts with existing offensive tooling. While this technology is just a thin wrapper around a separate account, there are a few nuances such as who is permitted to access these accounts, as well as existing UAC bypasses which are still effective against the new "backdoorless" Administrator Protection. This post explores these nuances in detail.| XPN InfoSec Blog
Tokenization Confusion - XPN InfoSec Blog
In this post we look at the new Prompt Guard 2 model from Meta, and introduce a concept I've been calling "Tokenization Confusion" which aims to confuse Unigram tokenization into generating tokens which will result in the misclassification of malicious prompts. We'll also look at why building up our ML knowledge will lead to better findings when assessing LLM API’s, as I discovered during a flight across the Atlantic.| XPN InfoSec Blog
The SQL Server Crypto Detour - XPN InfoSec Blog
One of the things that I love about my role at SpecterOps is getting to dig into various technologies and seeing the resulting research being used in real-time. This post will explore one such story of how I was able to go from a simple request of recovering credentials from a database backup, to reverse engineering how SQL Server encryption works, finding some new methods of brute-forcing database encryption keys.. and finally identifying a mistake in ManageEngine’s ADSelfService product w...| XPN InfoSec Blog
Tags - XPN InfoSec Blog
---| XPN InfoSec Blog
ADFS - Living in the Legacy of DRS - XPN InfoSec Blog
In this post we’re going to focus on some ADFS internals. We’ll be looking at OAuth2, and how it underpins the analogues to Entra ID security features like Device Registration and Primary Refresh Tokens.| XPN InfoSec Blog
LAPS 2.0 Internals - XPN InfoSec Blog
This year, LAPS 2.0 was released by Microsoft, and thankfully it now comes built-in to Windows. This time it comes ready for use with Active Directory, as well as being supported in Azure AD aka Entra ID. In this post, we’ll look at how LAPS 2.0 for Active Directory works under the hood, so you can make those fresh recommendations to your clients, and prepare yourself for the inevitable question... “But we just deployed LAPS.. what does LAPS 2.0 do differently?!”.| XPN InfoSec Blog
Identity Providers for RedTeamers - XPN InfoSec Blog
Originally presented at SOCON-2024, and continuing the series into post-exploitation techniques against Identity Providers, in this blog post we'll look at Ping, OneLogin and Entra ID. I'll discuss how post-exploitation techniques effective against Okta apply to other providers, release new tools for post-exploitation, and look at what proves to be effective when critical assets lie beyond an Identity Provider portal.| XPN InfoSec Blog
Hiding your .NET - ETW - XPN InfoSec Blog
In this post we will focus on Event Threading for Windows (ETW), how it is used to surface events on .NET assemblies, and how we can evade this kind of detection.| XPN InfoSec Blog
Azure AD Connect for Red Teamers - XPN InfoSec Blog
With clients increasingly relying on cloud services from Azure, one of the technologies that has been my radar for a while is Azure AD. For those who have not had the opportunity to work with this, the concept is simple, by extending authentication beyond on-prem Active Directory, users can authenticate with their AD credentials against Microsoft services such as Azure, Office365, Sharepoint, and hundreds of third| XPN InfoSec Blog
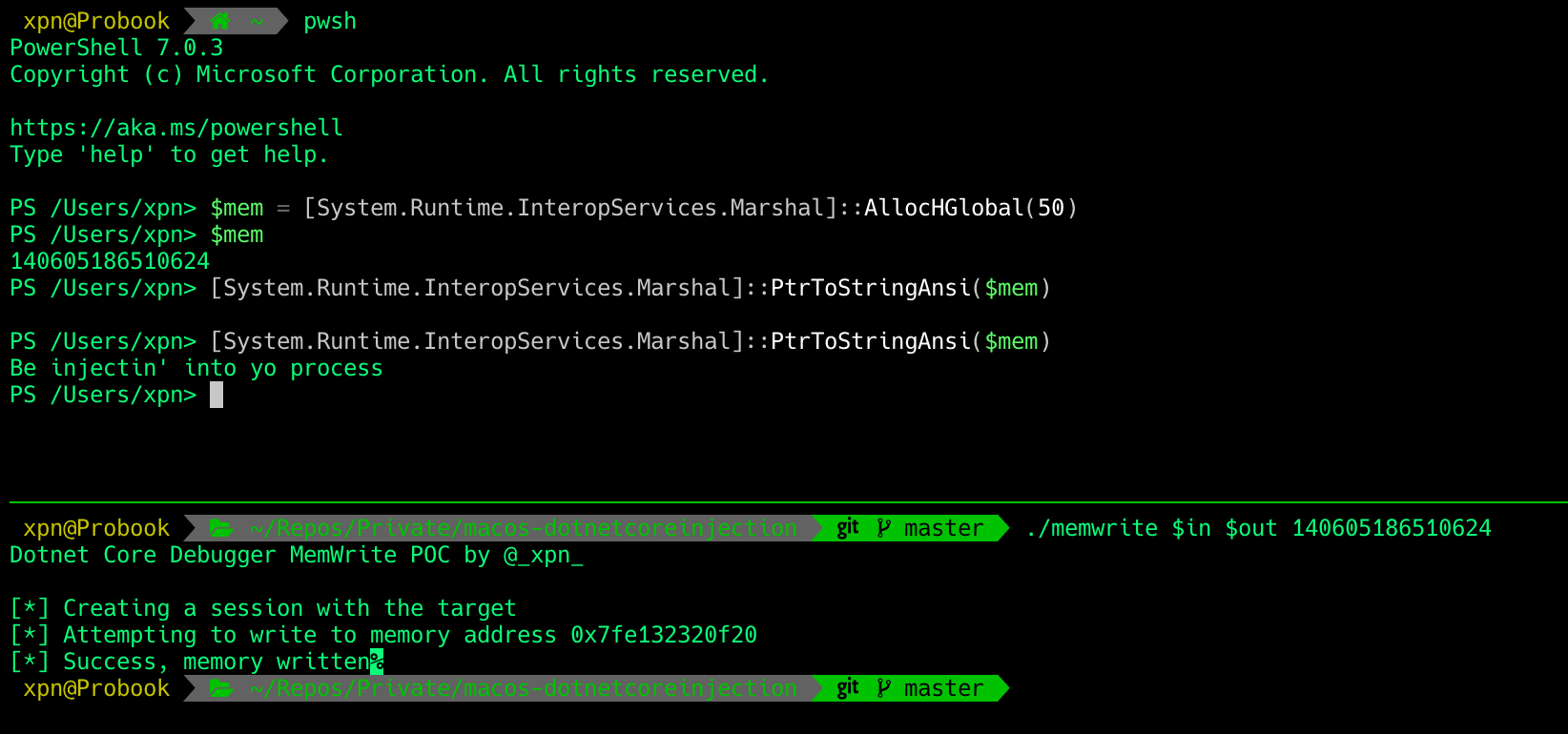
MacOS Injection via Third Party Frameworks - XPN InfoSec Blog
In this post, we are going to take a look at a couple of interesting methods of leveraging third-party technologies to achieve our code injection goals. For us, this translates to running code in the context of a target application without having to resort to disabling SIP.| XPN InfoSec Blog
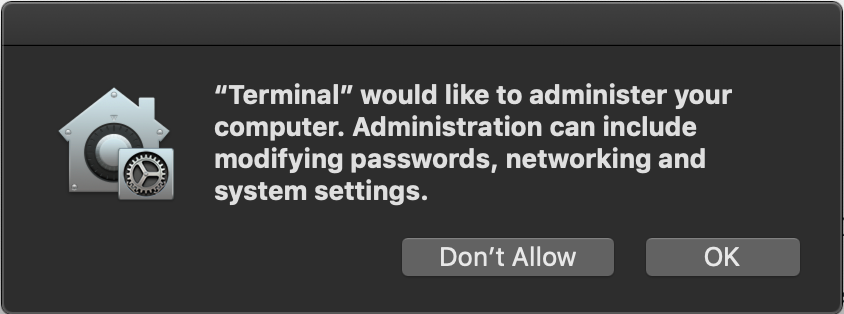
Bypassing MacOS Privacy Controls - XPN InfoSec Blog
Encountering Apple devices during RedTeam engagements is becoming increasingly common, so it's useful to have a few techniques available when navigating around whatever privacy or security changes are introduced with each version of MacOS. When MacOS Mojave rolled out at the end of 2018, a set of privacy restrictions were introduced to alert a user when an application requested access to sensitive data, such as the camera, microphone, address book, calendar etc.. And as (more often than not) o| XPN InfoSec Blog
Exploring Mimikatz - Part 2 - SSP - XPN InfoSec Blog
If you haven't had a chance to check it out, take a look here. Continuing on, in this post we will review what has become a nice way of subverting security controls added by Microsoft to prevent dumping of credentials, as well as extracting credentials as they are provided by a victim.| XPN InfoSec Blog
Exploring Mimikatz - Part 1 - WDigest - XPN InfoSec Blog
We’ve packed it, we’ve wrapped it, we’ve injected it and powershell’d it, and now we've settled on feeding it a memory dump, and still Mimikatz remains the tool of choice when extracting credentials from lsass on Windows systems. Of course this is due to the fact that with each new security control introduced by Microsoft, GentilKiwi always has a trick or two up his sleeve. If you have ever looked at the effort that goes into Mimikatz, this is no easy task, with| XPN InfoSec Blog
Building, Modifying, and Packing with Azure DevOps - XPN InfoSec Blog
In this post I will be showing how to build a Azure DevOps pipeline for .NET projects, and hopefully show some techniques which I have found useful to modify build artifacts to make them a bit different, and in some cases, to increase the time it takes to analyse our tools if detected by Blue Team.| XPN InfoSec Blog
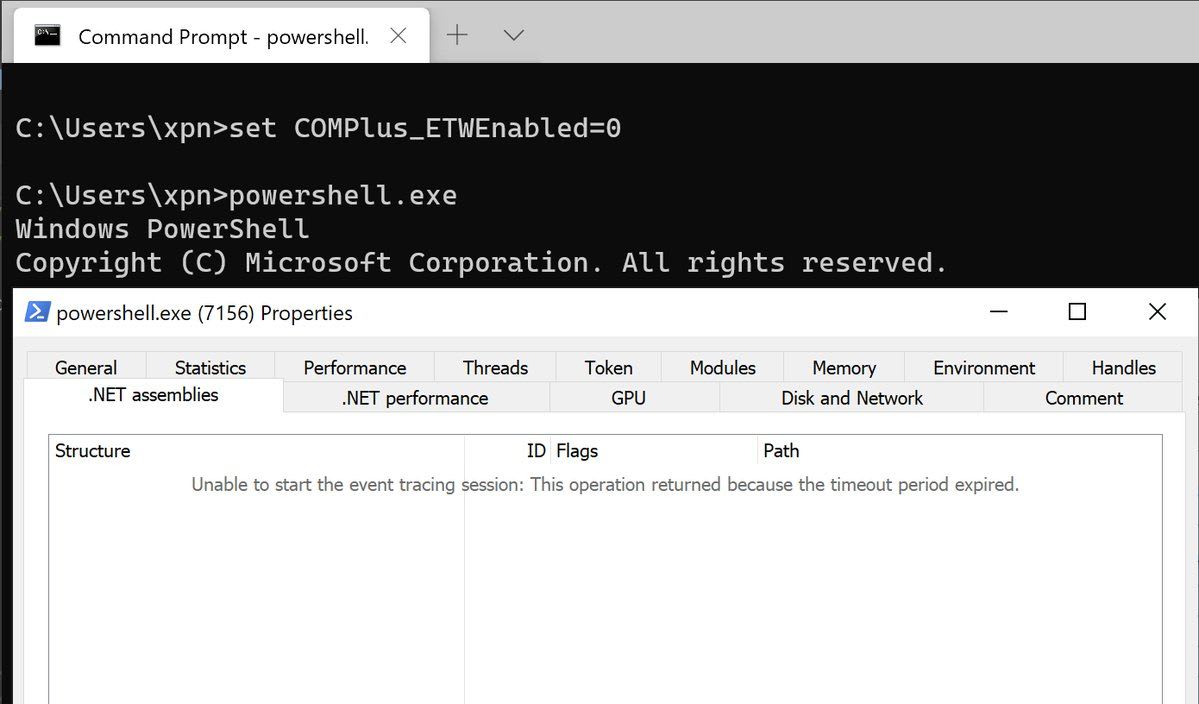
Hiding your .NET - COMPlus_ETWEnabled - XPN InfoSec Blog
It turns out that there is a method of disabling ETW in .NET, strangely exposed by setting an environment variable of COMPlus_ETWEnabled=0. This post explores how this works.| XPN InfoSec Blog
MacOS "DirtyNIB" Vulnerability - XPN InfoSec Blog
While looking for avenues of injecting code into platform binaries back in macOS Monterey, I was able to identify a vulnerability which allowed the hijacking of Apple application entitlements. Recently I decided to revisit this vulnerability after a long time of trying to have it patched, and was surprised to see that it still works. There are some caveats introduced with later versions of macOS which we will explore, but in this post we’ll look at a vulnerability in macOS Sonoma which has ...| XPN InfoSec Blog
Okta for Red Teamers - XPN InfoSec Blog
In this blog post, I'll discuss some of the post-exploitation techniques that I've found to be useful against Okta. Specifically, this post will look at how to use delegated authentication to our advantage, silver tickets, Okta AD agent spoofing, and finally how to deploy a fake SAML provider.| XPN InfoSec Blog
PNG Steganography from First Principles - XPN InfoSec Blog
Steganography is experiencing a revival as a wrapper for delivering payloads. In this post we'll go back to basics and show just how steganography can be applied to a PNG image using the common least significant bit (LSB) encoding technique. No magic... just raw information... and a little C++.| XPN InfoSec Blog